Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Analysis of Black Basta Ransomware Chat Leaks
By Jambul Tologonov and John Fokker · March 18, 2025
Introduction
On Feb 11, 2025 a Telegram user @ExploitWhispers shared via their Telegram channel ‘shopotbasta’ (EN: ‘basta whisper’) Black Basta RaaS (Ransomware as a Service) Matrix chat leaks containing over 200,000 messages spanning from September 2023 to September 2024. The @ExploitWhispers claim that Black Basta has recently attacked Russian banks and thus crossed the line, therefore they decided to leak their internal chat communications.
Trellix obtained access to Black Basta's chat leaks at the end of February 2025 and immediately began analyzing the chat logs. Given that Black Basta is a rebrand of Conti RaaS, our approach mirrored that which we took in Conti Leaks: Examining the Panama Papers of Ransomware.
In the following sections, we will provide noteworthy chat observations made during our research regarding Black Basta RaaS's potential connection to the Russian authorities, their usage of AI, and collaboration with other RaaS and malware groups.
We reformatted the original JSON leak file into an easily readable structure and will support our findings with screenshots of the original chat as well as the translated-to-English chat logs.
Interesting chats
We will start by saying that our analysis of the chat logs did not reveal any evidence of Black Basta ransomware targeting Russian banks, nor is the Trellix Advanced Research Center aware of such an event occurring in recent months. Therefore, the identity and intention of @ExploitWhispers remain unclear; they could be a disgruntled affiliate, a security researcher, or a competitor of Black Basta RaaS.
Connection to Russian authorities
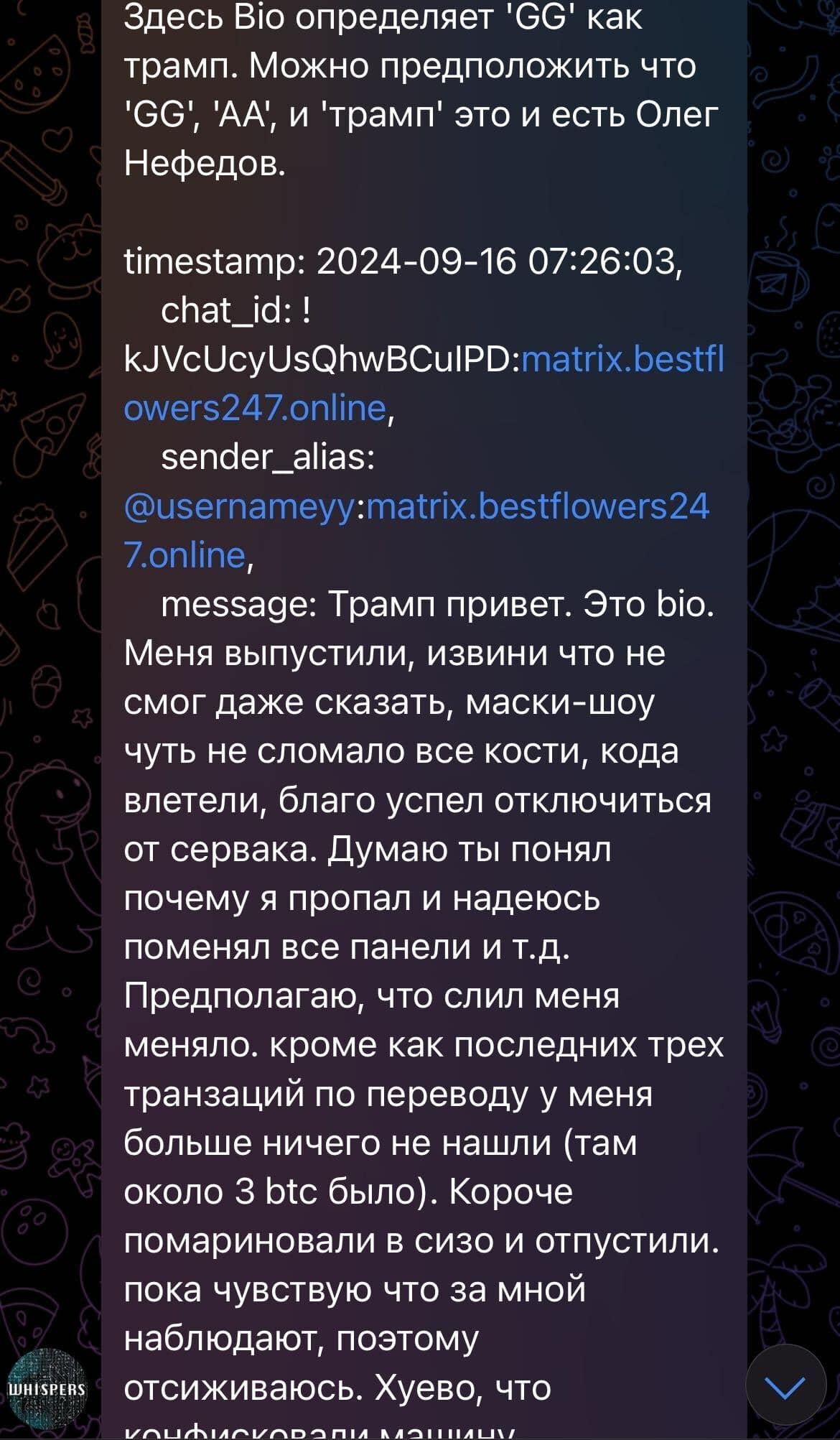
According to @ExploitWhispers, Black Basta’s leader GG aka AA is a Russian individual named Oleg Nefedov. Based on Open-source intelligence (OSINT) research we came across an Armenian article where O. Nefedov, wanted by the US Law Enforcement (LE), was detained in Yerevan on the 21/06/2024 and mysteriously escaped the Armenian court two days after his arrest.
Analysis of the chat leaks showed that GG sent no message from June 20, 2024 until July 3, 2024. When GG resumed activity in the Matrix chat, he had a lengthy conversation with Chuck discussing the circumstances surrounding his arrest and how Russian authorities helped him. GG stated that he contacted Russian authorities and requested a ‘green corridor’ and they promptly flew to extricate him. GG implies he has friends at the very high level, the level of the number 1 and the number 1 was aware of his situation and his rescue would not have been possible without his coordination. Chuck asked if the number 1 is ‘vvp’ (potentially V.V. Putin) however received no confirmation or denial.
Furthermore, Chuck mentioned a $10 million reward for information on ‘tr’ (possibly ‘-amp’), potentially referring to the US bounty for five key members of the Conti gang, including the hacker Tramp. In the leaked chat, GG was indeed identified as Tramp (Conti leader) by ‘bio’, (also known as ‘pumba’, another Conti member).
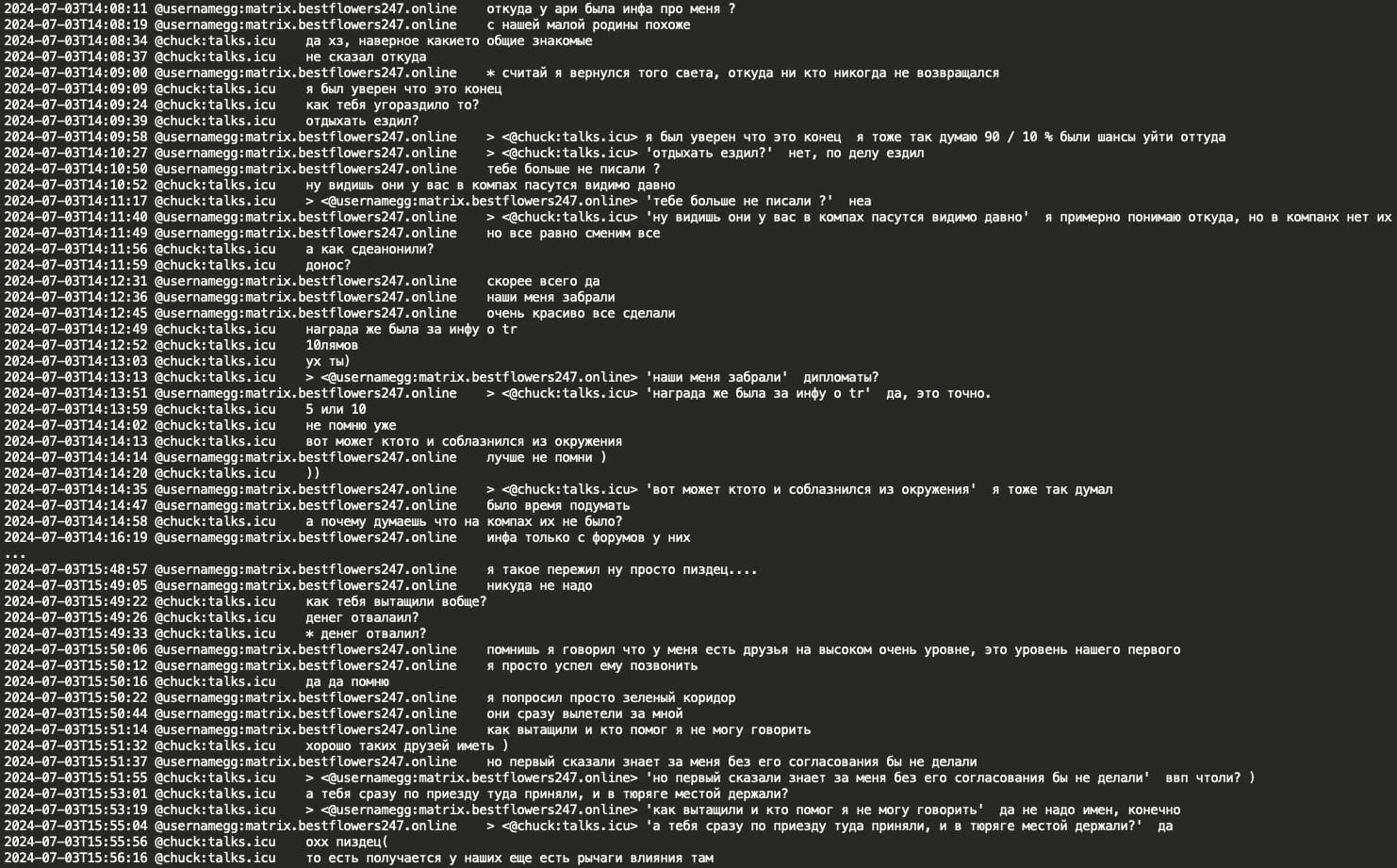
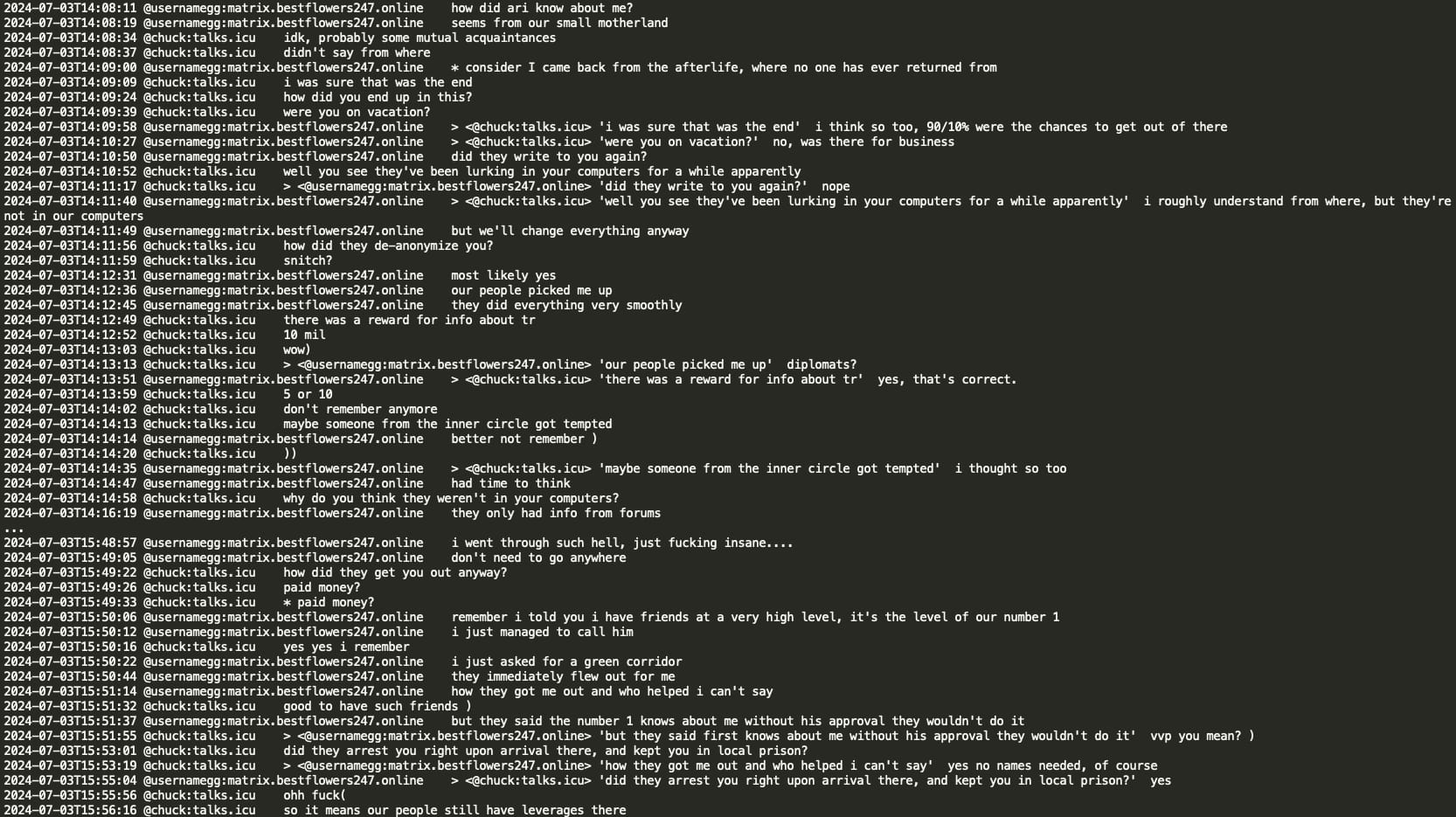
It is noteworthy that GG indicated that Russian law enforcement possesses leverage in a country where he was apprehended. GG stated that if there were an official request from Interpol, Russian law enforcement would ‘strangle’ it to prevent any complaints or questions from arising.
Furthermore, while discussing the duration of their involvement in illicit activities, GG and Chuck stated that they would continue as long as the 'grandpa' lives and would work until the Special Military Operation (SMO) concludes, referencing Russia's invasion of Ukraine. It is unclear who 'grandpa' refers to, however, it could be a reference to a senior individual who provides protection to Black Basta leaders. Chuck expressed that the SMO would last for an extended period.

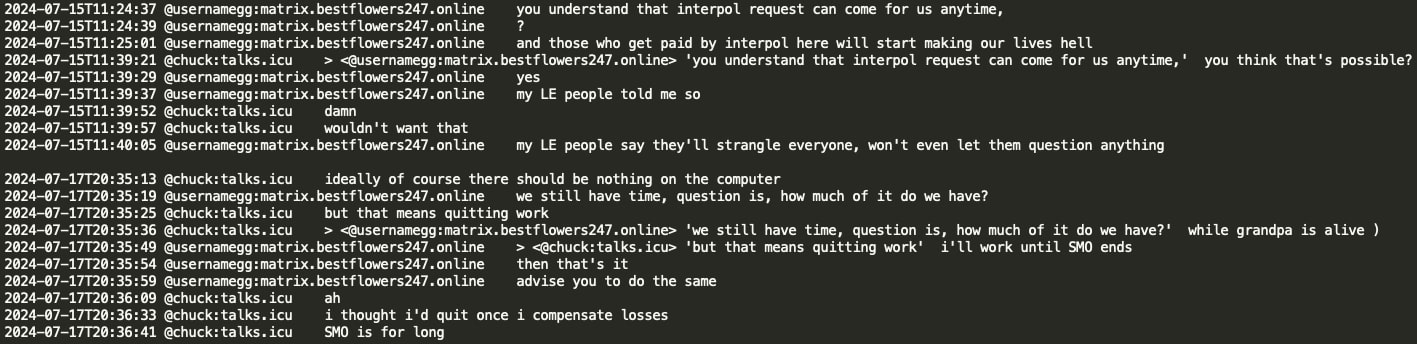
Further communication between GG and Chuck concerns a member of the Conti/Trickbot group, Fedor Andreev, who has a Red Notice on Interpol's website. GG states that he believed Trickbot members were all of Ukrainian origin; however, F. Andreev apparently has Russian citizenship. GG (aka Tramp) indicates that 'ari' (also known as 'arik' and potentially GG's superior) is acquainted with individuals from that gang and mentions ‘bentley’, one of the Conti/Trickbot gang's team leaders, who is from Russia and allegedly works for the FSB.
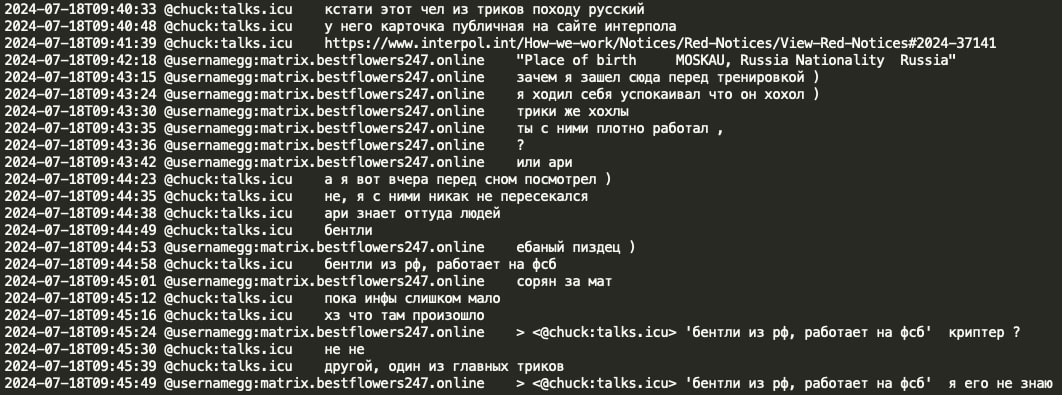
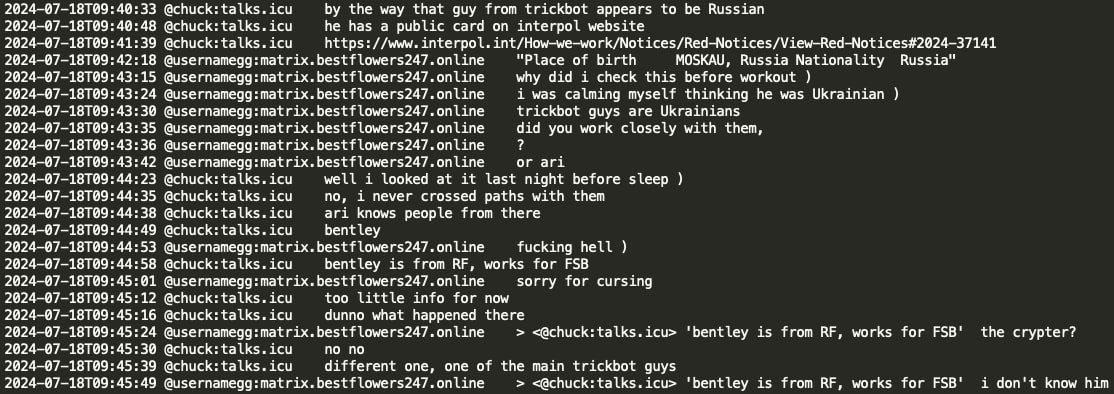
In March 2024, Tinker (a negotiator and Conti member) informed GG that a pentester ‘alpha’ (also known as ‘forest’) from the BlackSuit/Royal ransomware group (a Conti spinoff), inquired about GG's targeting of ‘friendly countries’. Due to an attack linked to Black Basta RaaS, ‘the office’ was searching for him. GG responded by asking ‘which office - the FSB, FSO, or the department K?’ (FSB: Federal Security Service, FSO: Federal Protective Service, Department K: Federal Internal Affairs department handling IT/cybercrime). Tinker revealed the office was the FSB. GG clarified that they do not target friendly countries, stating, ‘we occasionally probe China but never lock anything there’. Tinker suggested the situation might be related to an Israeli oil company with numerous trusts in Latin America and provided TOX contact for further discussion. Tinker also mentioned working as a negotiator for BlackSuit RaaS and that former REvil members handle the ‘locking’ (encrypting PCs, network) there.
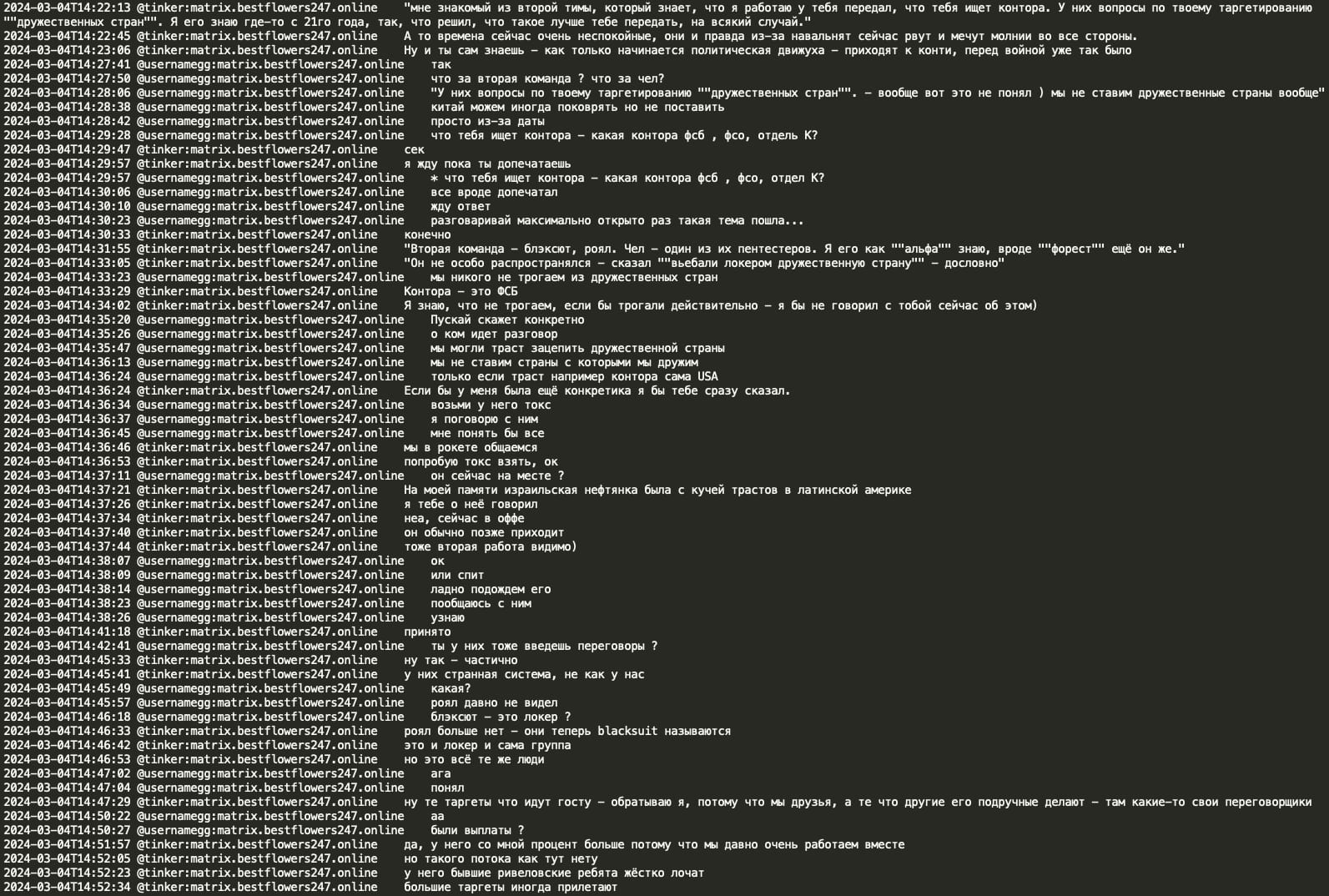
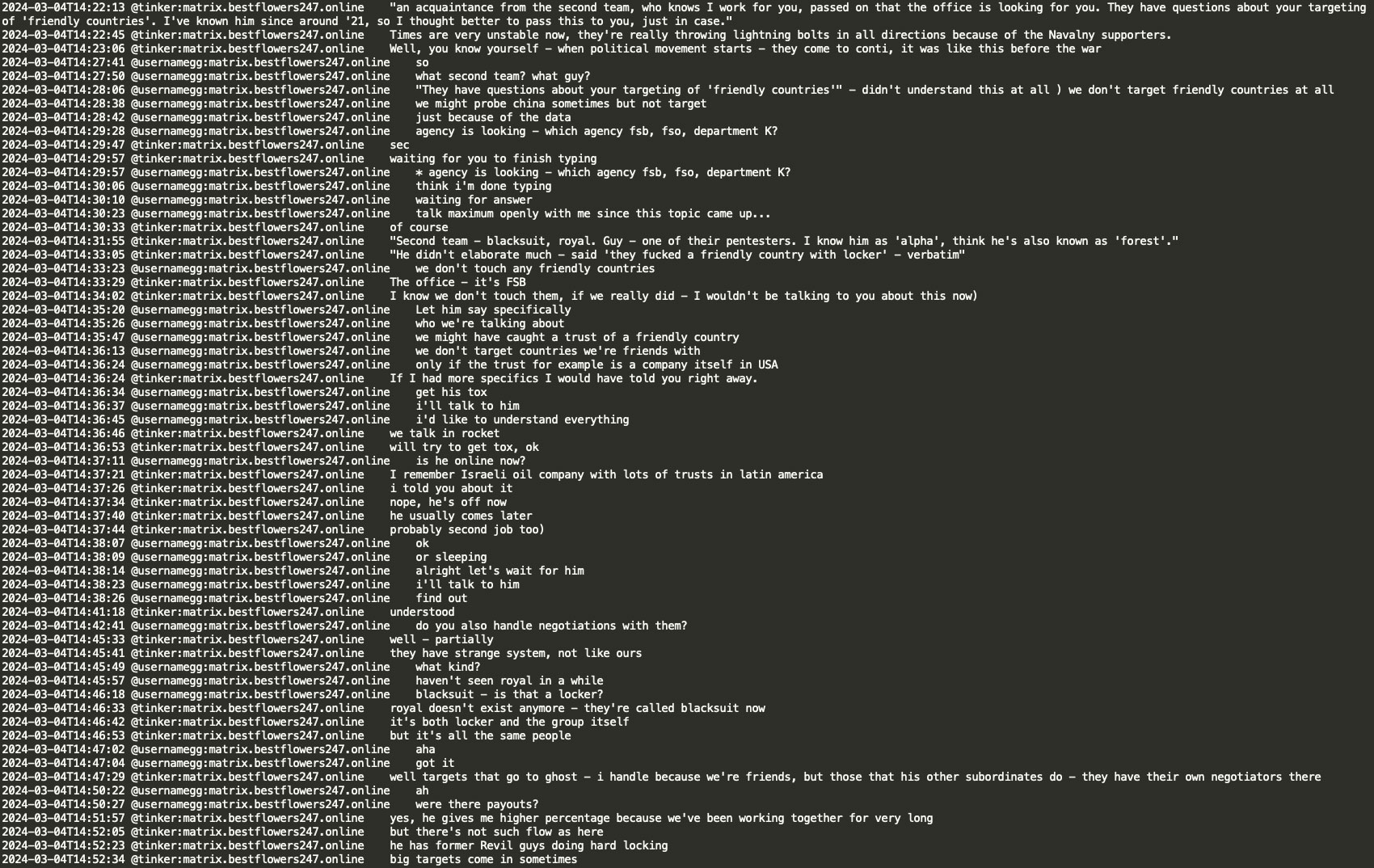
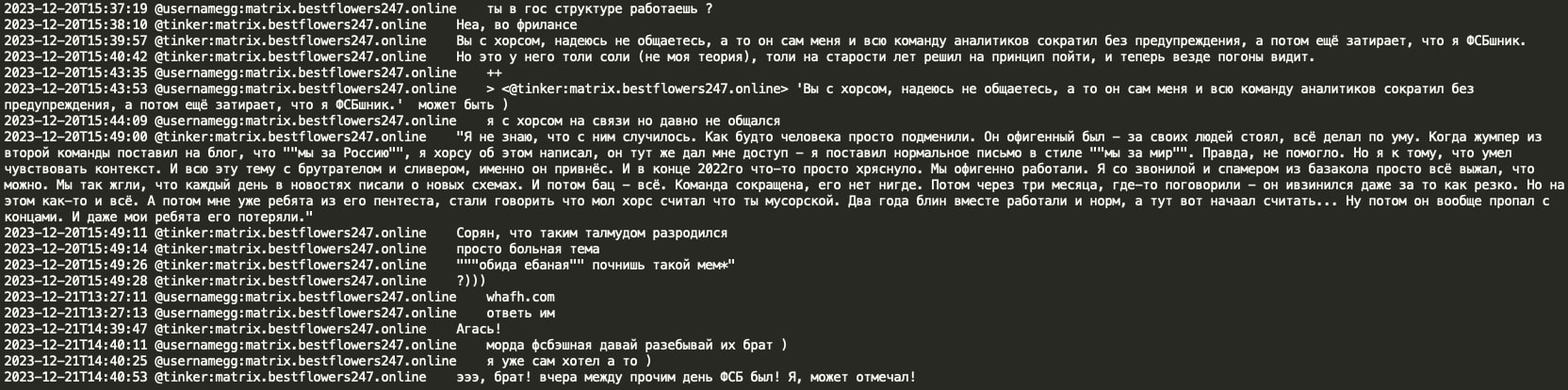
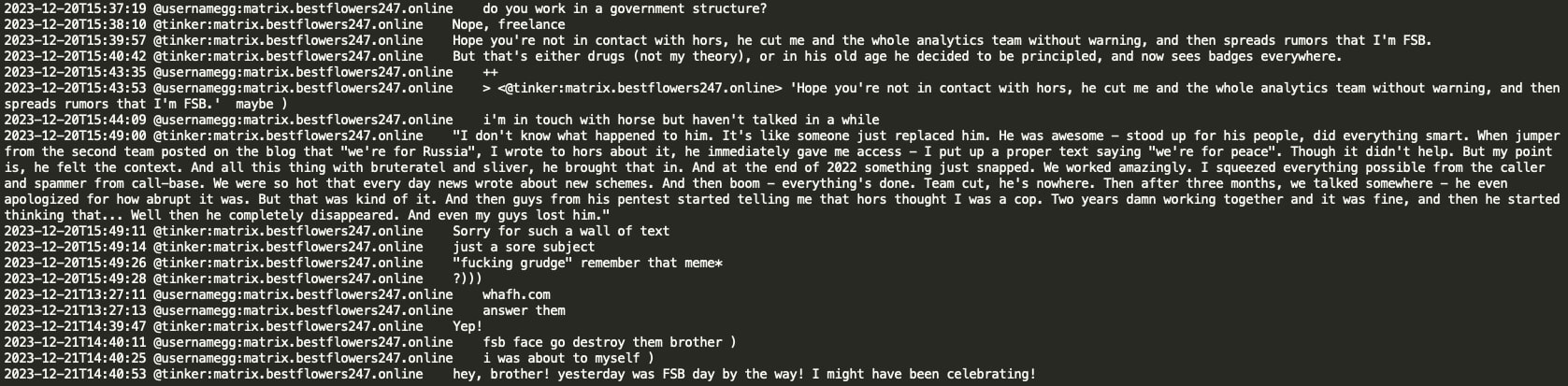
Tinker also indicated that he had previously worked for Hors's team (Conti's leader/sysadmin). Tinker mentions that he does freelance work as a second job and that he lost contact with Hors because Hors believed he worked for the FSB. Tinker advises that this is not the case, although he joked that the previous day was a ‘day of the FSB’ and they may have celebrated it. Interestingly, Tinker mentions that while working for Hors, ‘jumper’ from the second team posted ‘We are pro Russia’ on the blog, and Tinker was the one who then edited the text to ‘We are for peace’, though it did not help in the end. This is a potential reference to the Conti blog where, indeed, similar text modifications were observed in 2022.
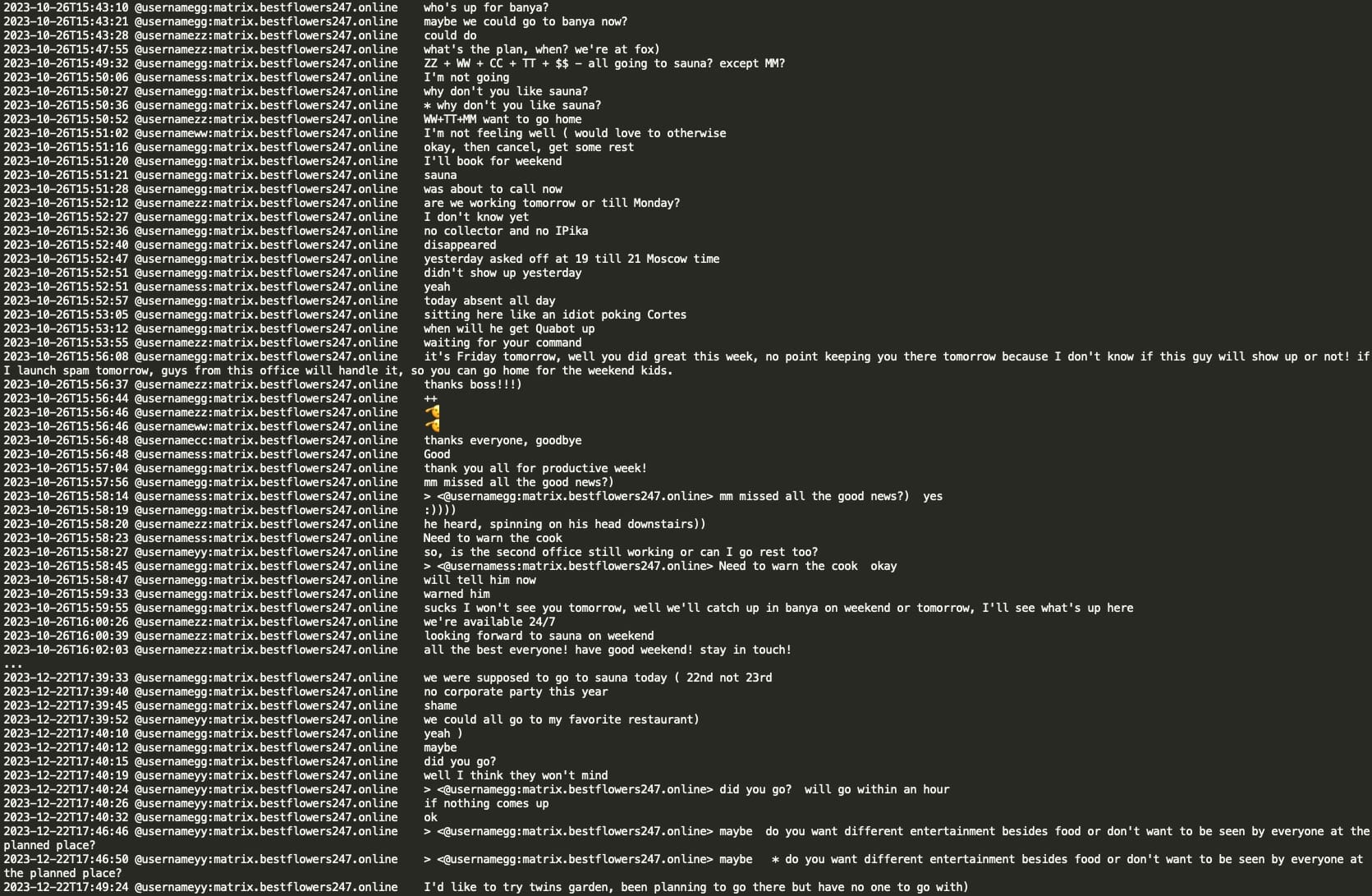
Offices in Moscow
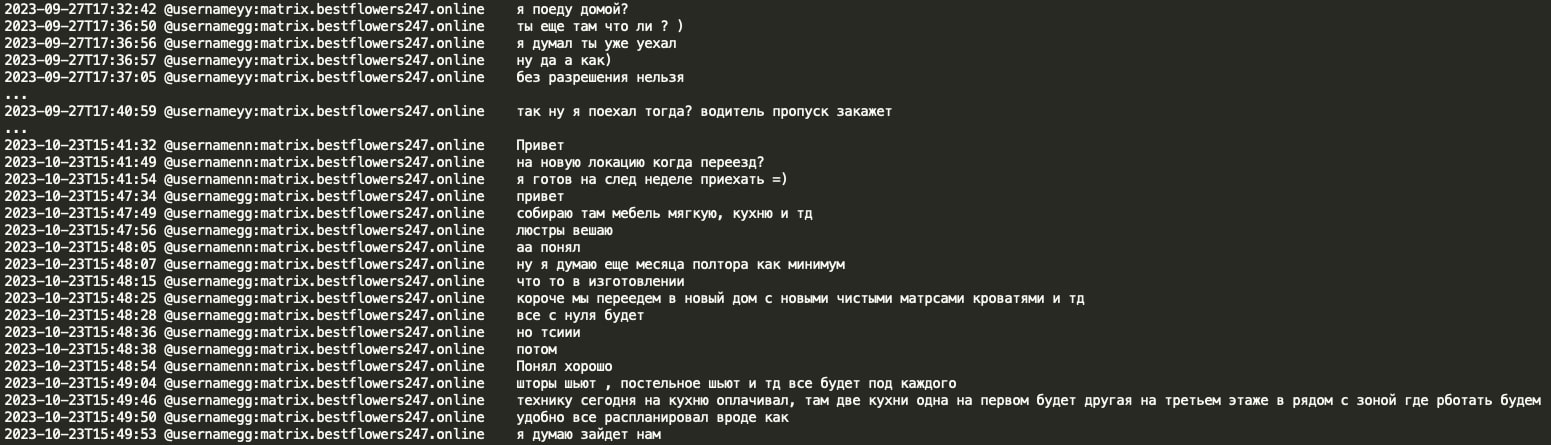
Black Basta appears to have two offices in Moscow. GG seems to travel between the offices with their driver. Whenever team members visit the offices, they need to arrange office entrance passes, which is typically done through drivers. Drivers are also used to transport equipment between the offices at Tramp's order (for example, new SIM cards for Internet usage). Office workers cannot leave without requesting permission from Tramp or notifying their supervisors. In October 2023, Tramp advised that they would be moving to a new office in a few months and that they were assembling new furniture there, ordering new kitchen appliances, lamps, new beds and clean mattresses, etc. The office has two kitchens, one on the 1st floor and the second on the 3rd floor close to their working space, suggesting that the office is an administrative building.
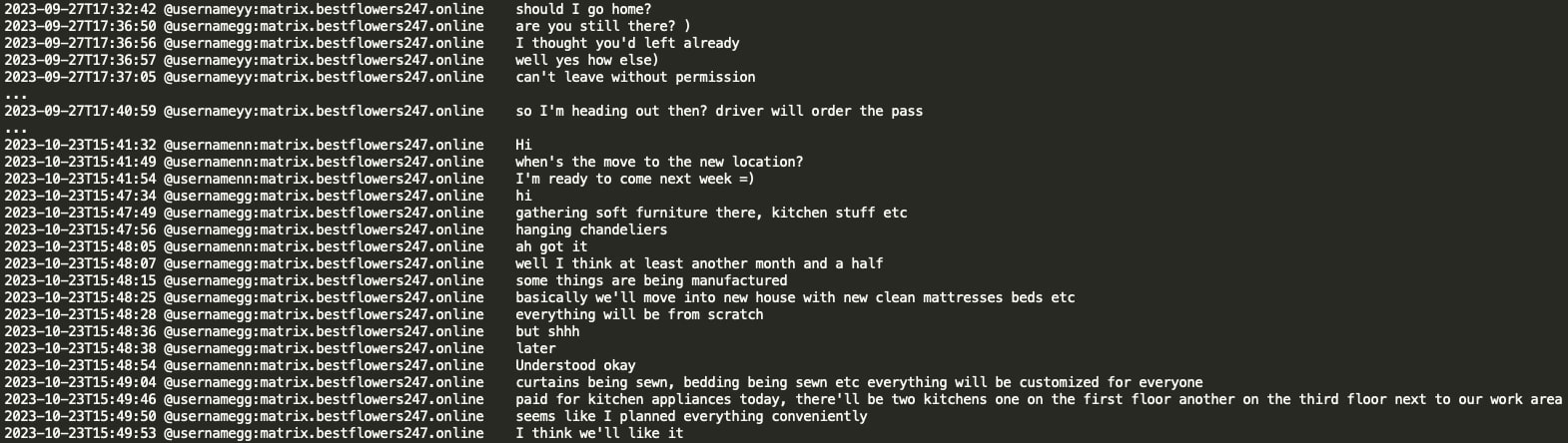
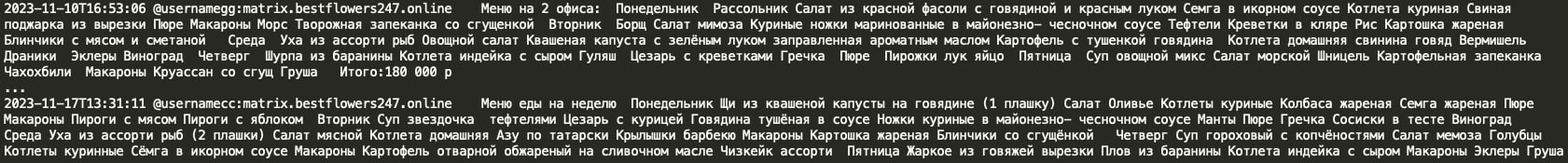
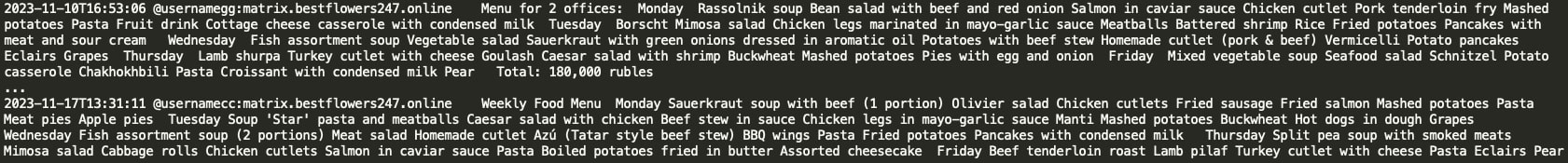
Black Basta gang members share the weekly canteen menu and frequently discuss matters in the kitchen. Weekly kitchen expenses for two offices appear to be approximately $2,000 USD.
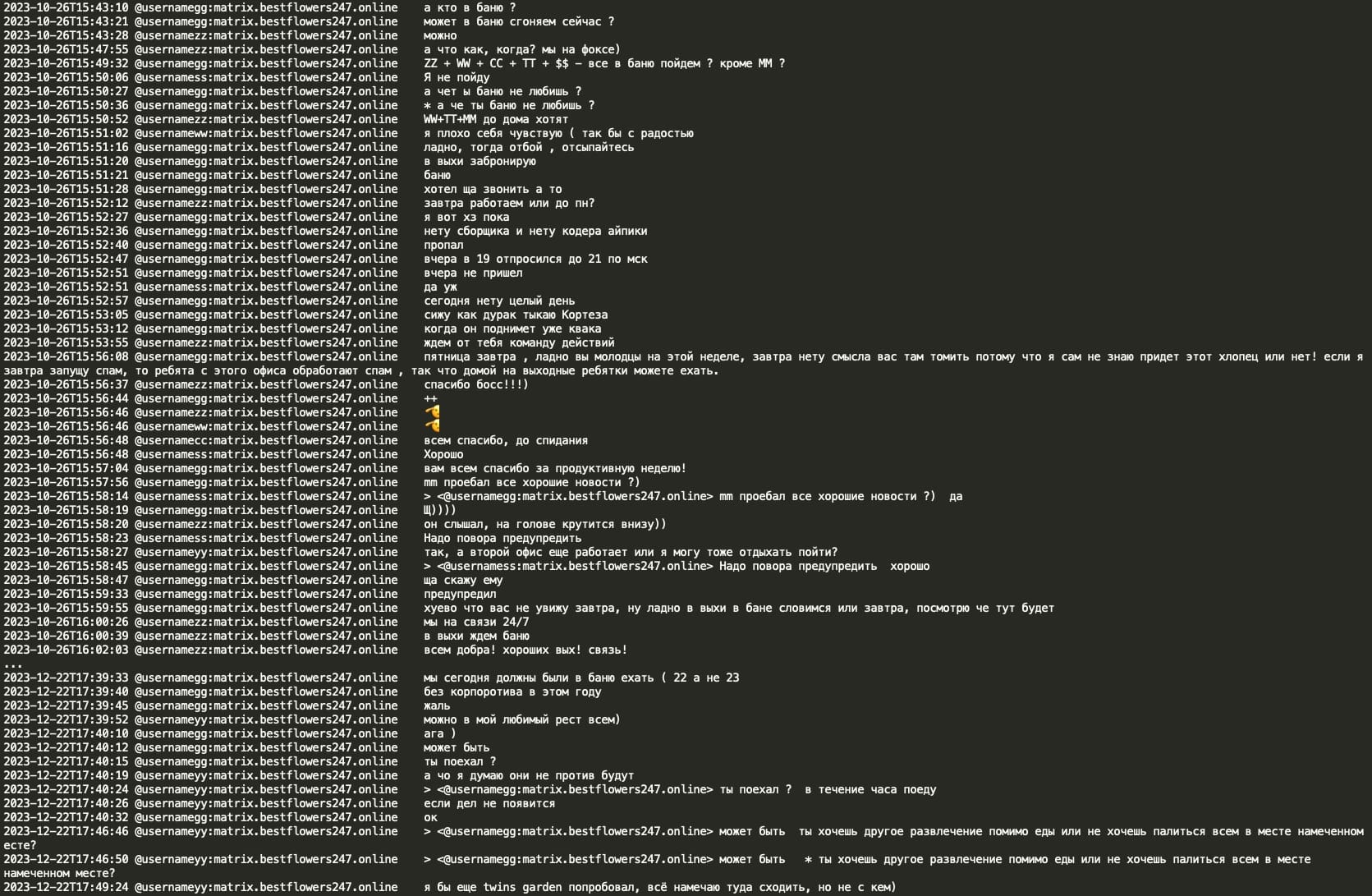
Furthermore, it is noteworthy that at the end of the year, they typically visit a Russian 'banya' (sauna) and host a corporate New Year event at upscale restaurants, such as the two Michelin star restaurant Twins Garden in Moscow. This further substantiates their physical presence in the Russian capital.
Black Basta’s AI usage
The Black Basta group utilizes ChatGPT for a variety of purposes, including composing fraudulent formal letters in English, paraphrasing text, rewriting C#-based malware in Python, debugging code as well as collecting victim data. It appears that GG acquires ChatGPT accounts from marketplaces/forums such as ‘Plati Market’, and occasionally shares the credentials with other team members. Below are notable instances in which Black Basta RaaS members used ChatGPT for malicious purposes.
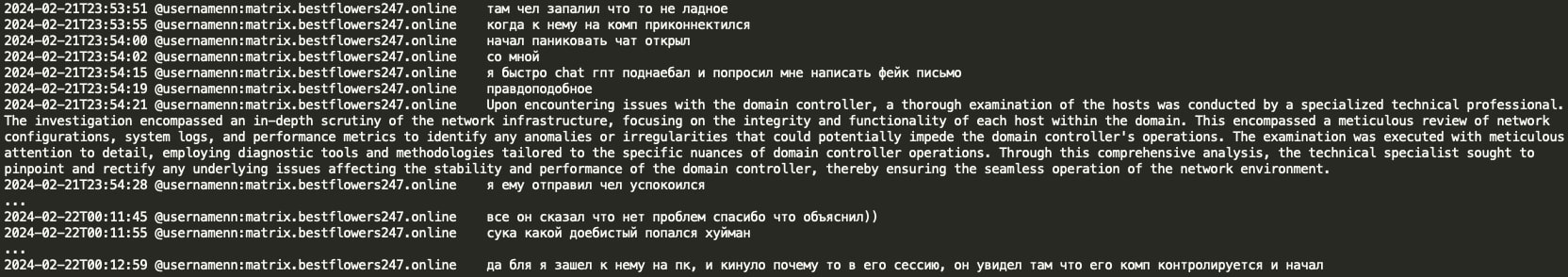
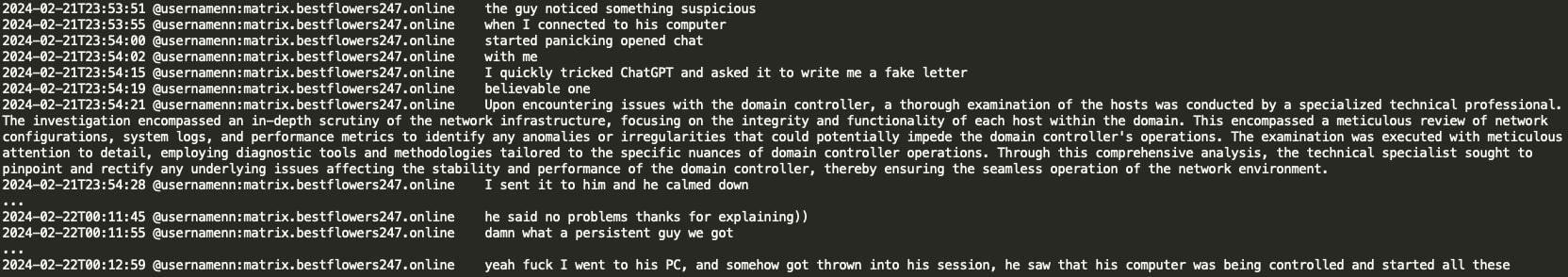
In this instance, NN inadvertently logged into an active user PC on the victim organization's network, alerting the user of a remote login within their current session. NN utilizes ChatGPT to rapidly generate a deceptive message, falsely asserting that a professional network check is underway and assuring the user that there is no cause for concern.
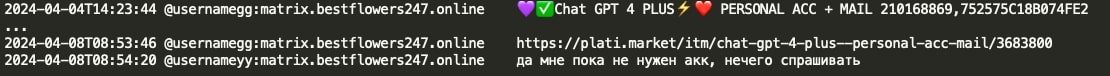
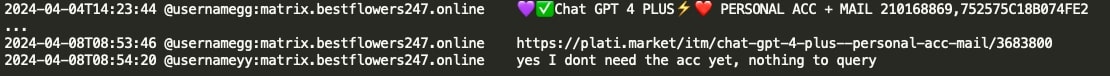
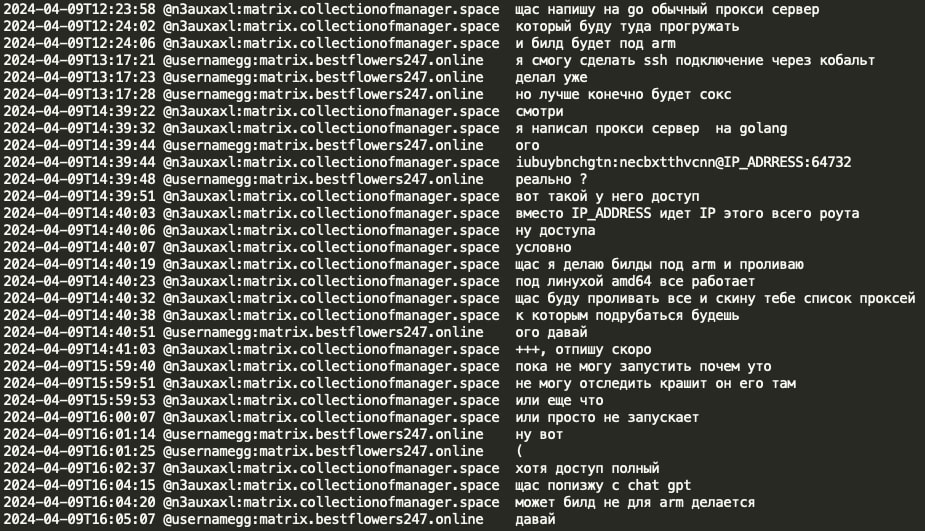
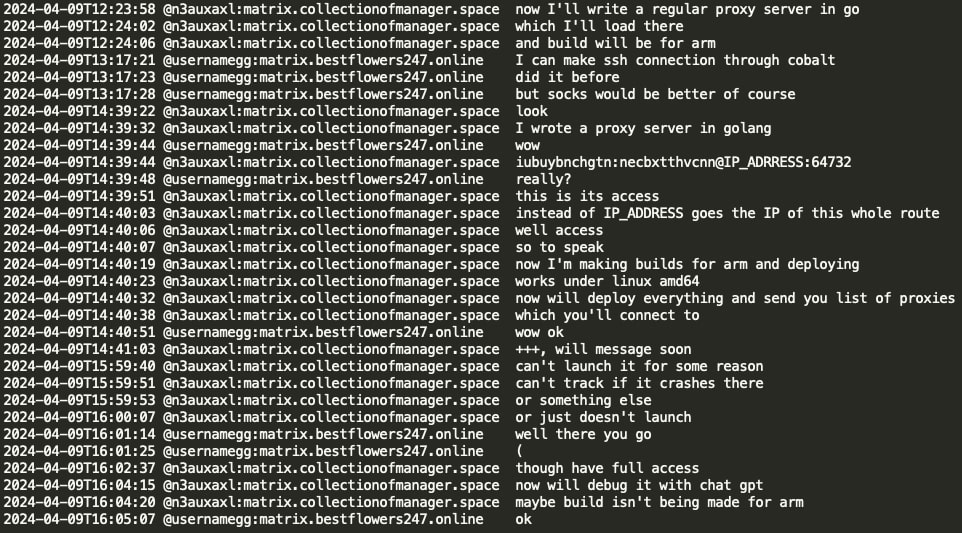
Mecor (developer of Pikabot) created a Proxy Server using the Go programming language, including builds for ARM/Linux. However, the ARM build encountered a runtime error, and mecor utilized ChatGPT to diagnose and resolve the issue.
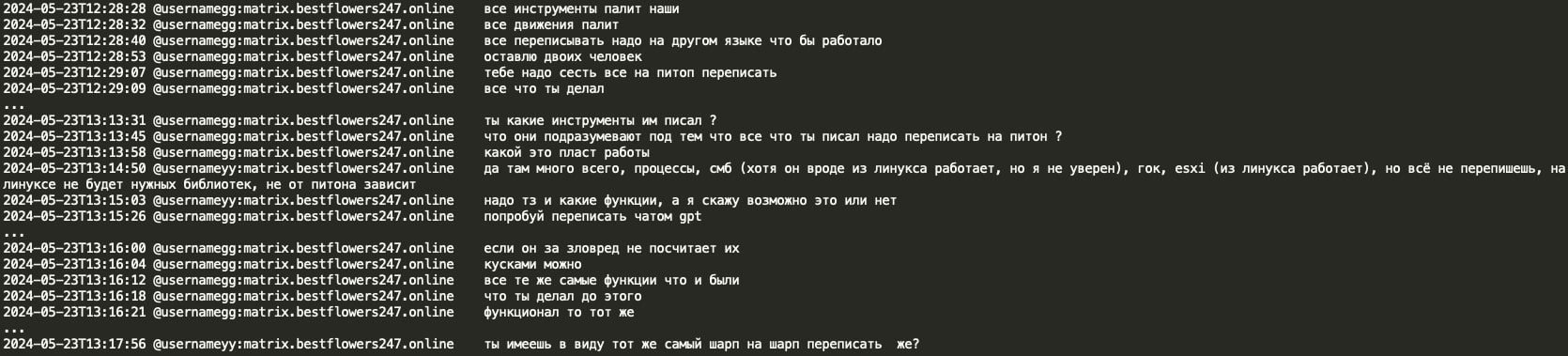
YY (coder of Black Basta) was instructed to rewrite the tools in Python as some of the gang’s malware got detected by AV/EDR. GG asked YY to use ChatGPT for that, and if ChatGPT would complain about malware, YY can instead provide code in chunks. YY later inquired if GG's suggestion was to rewrite C# in C#, revealing that Tramp instructed to rewrite the malware from C# to Python using ChatGPT.

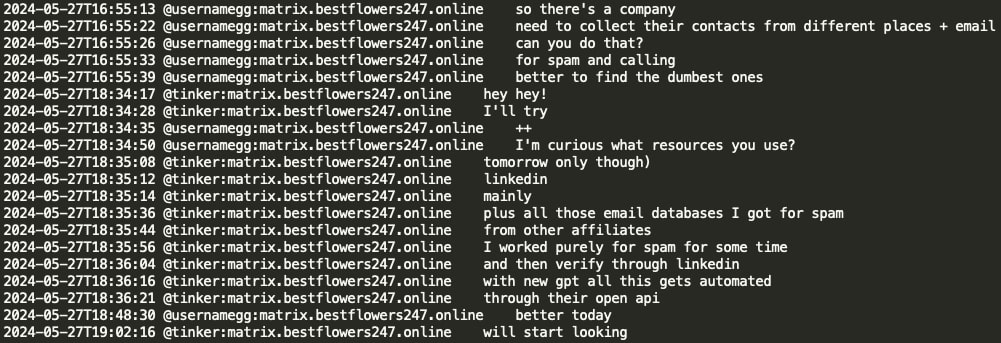
Here GG requested that Tinker (negotiator) gather victim company contacts and emails from various sources for the purpose of spamming and calling. GG inquired about the resources Tinker utilizes, to which Tinker responded that he uses an email database for spamming, verifies contacts via LinkedIn, and that with the new ChatGPT, everything is being automated through their API services.

Ascension Health hack
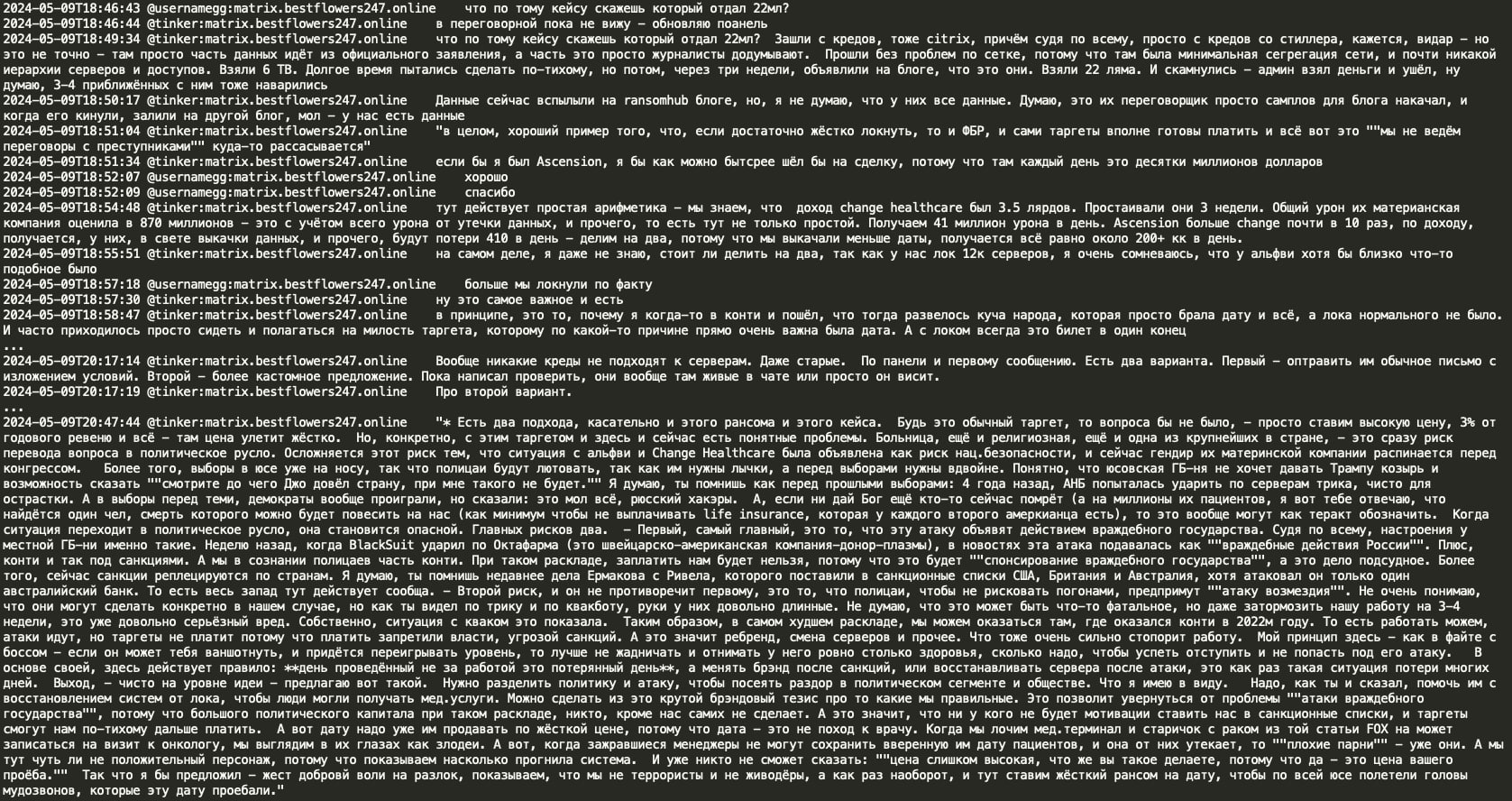
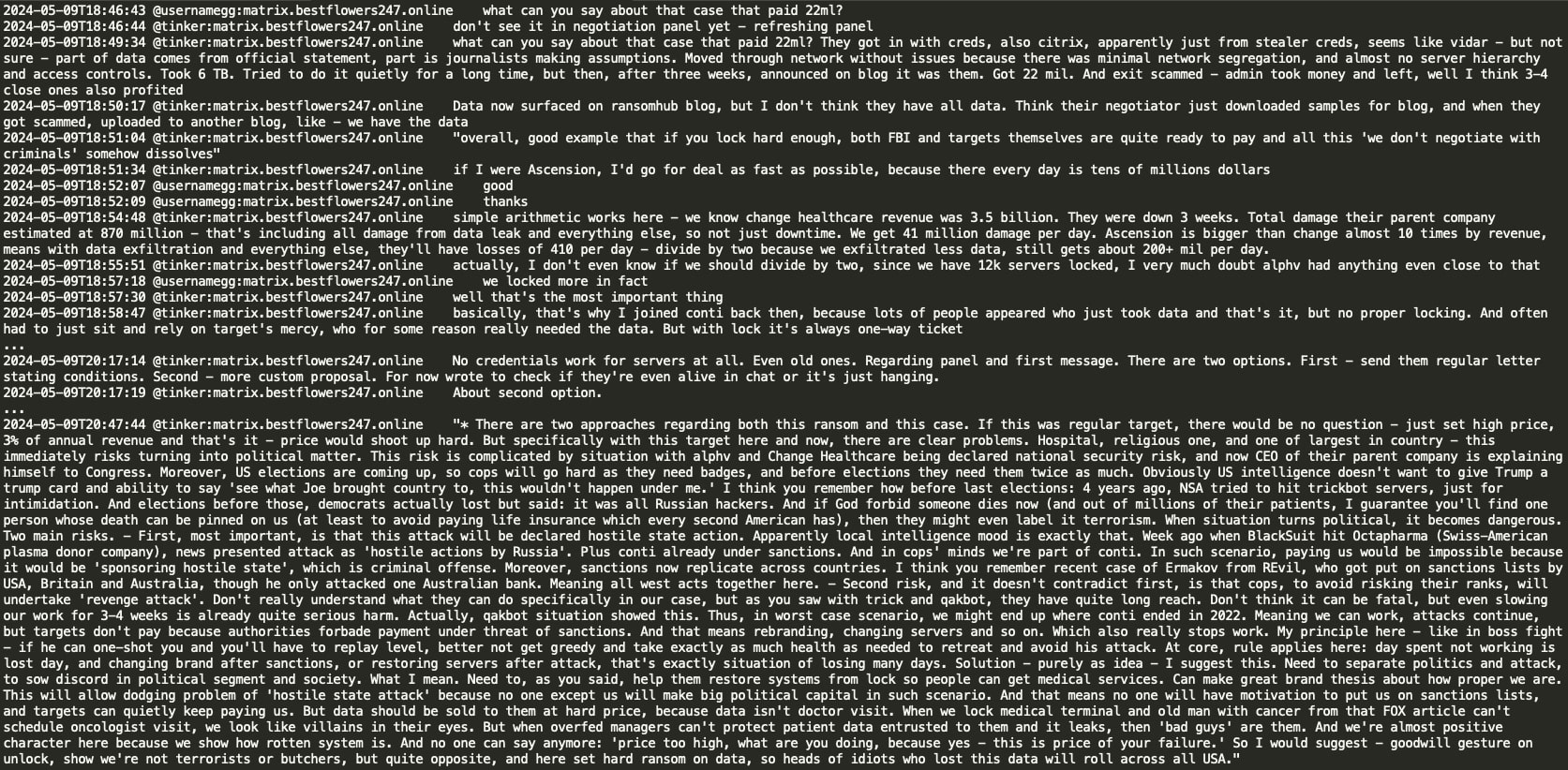
In a notable conversation, threat actors Tinker and GG discussed the Ascension Health data breach and compared it to the Change Healthcare incident perpetrated by the ALPHV RaaS operation, where Change Healthcare allegedly paid a $22 million ransom. The Black Basta group discovered that they had not encrypted the Ascension Healthcare data correctly due to a crypt error and decided to share the decryption key to avoid potential political sanctions and retaliation from US law enforcement against their infrastructure. However, they planned to demand a ransom for the exfiltrated patient data from Ascension Health.
The conversation also touched upon the consequences of RaaS closure, overhead costs associated with rebranding, and the sanctions imposed on the Conti RaaS, which prevented victims from paying ransoms as it would imply supporting an enemy country. The Black Basta group expressed their desire to avoid a repeat of the challenging circumstances they faced in 2022.
It appears that the provided decryption key was not working properly and Black Basta put the Ascension Health case on hold.
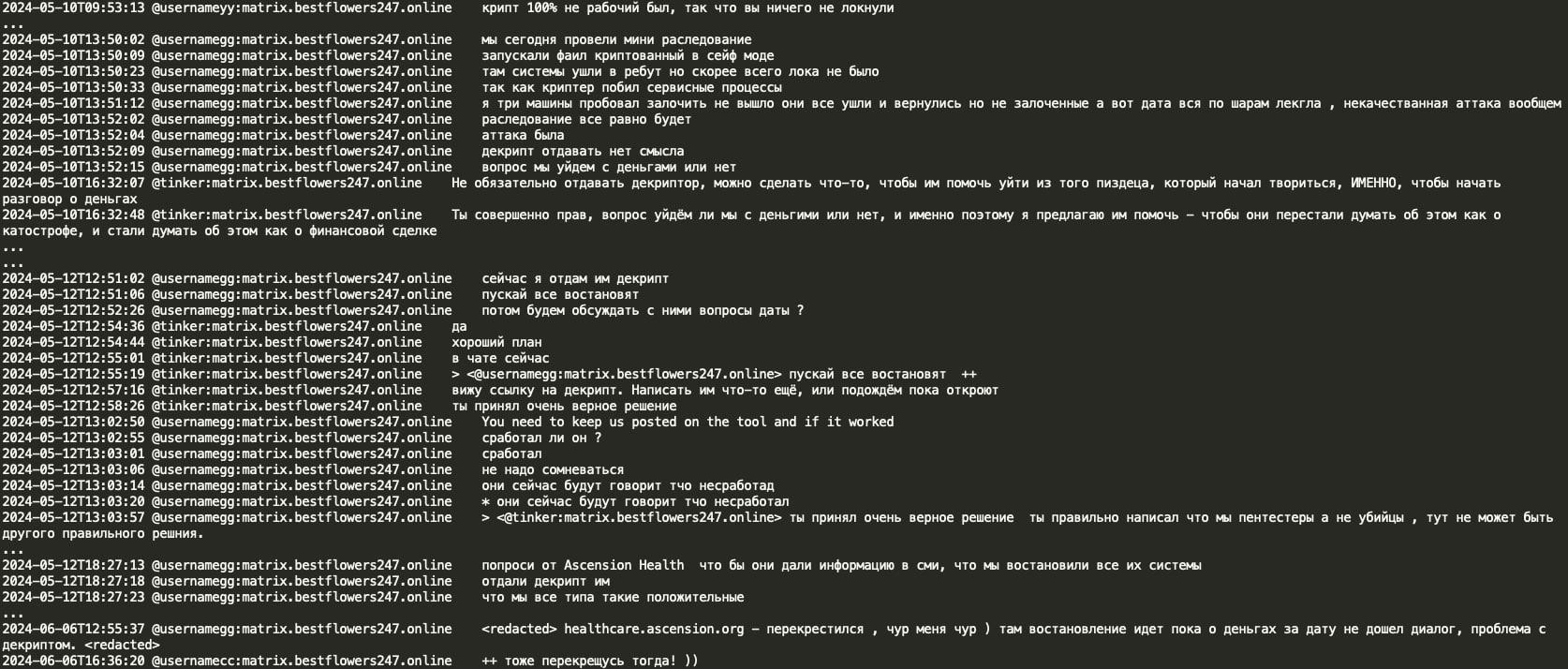
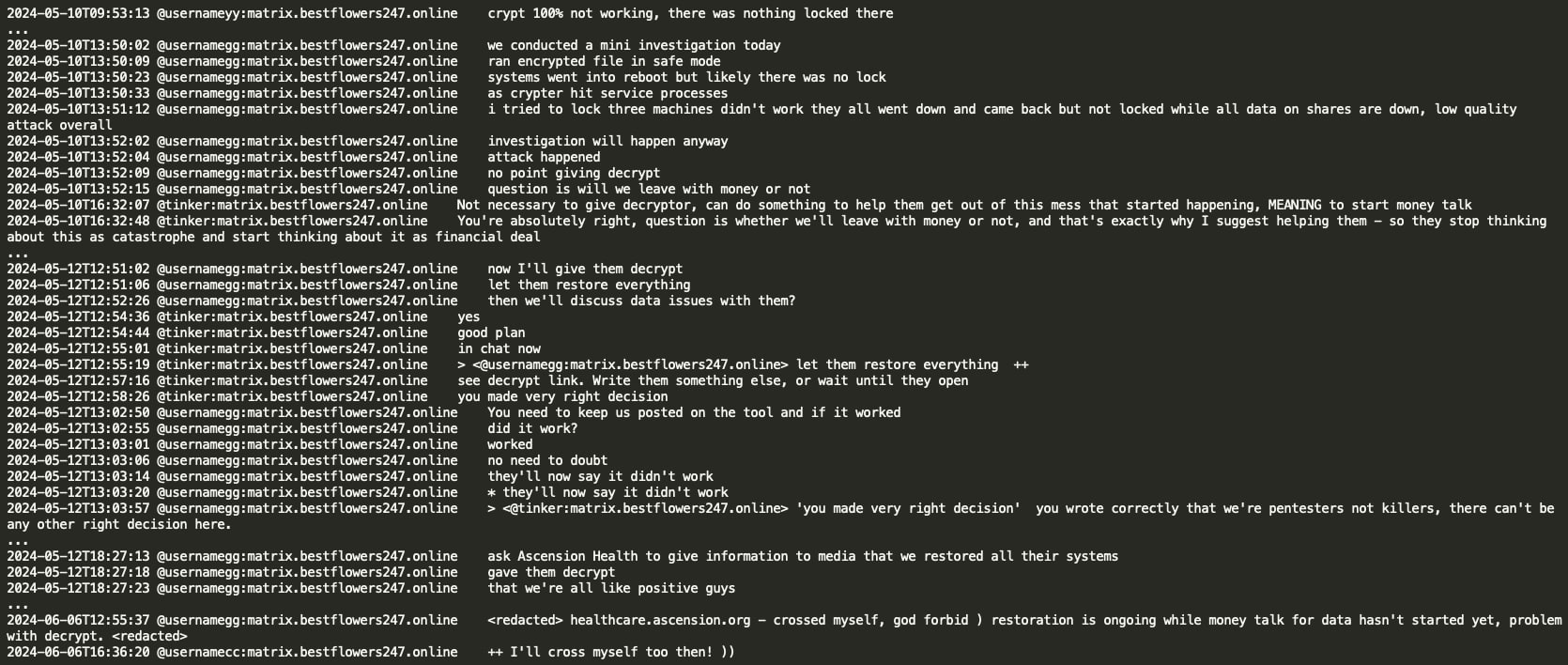
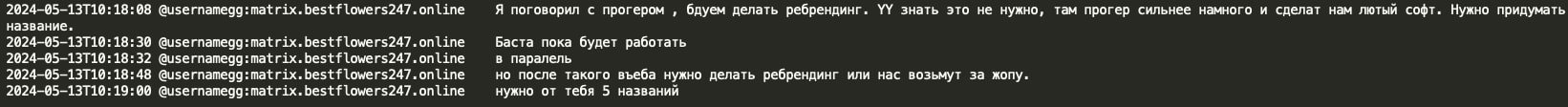
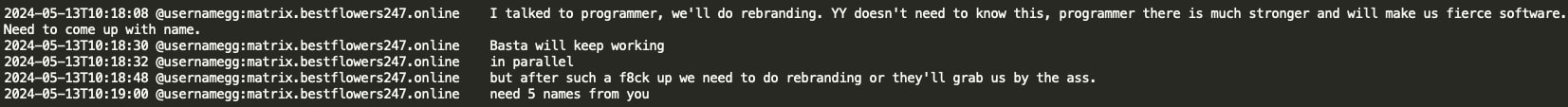
As the result of the unsuccessful Ascension Health hack, GG decided they should start working in parallel on rebranding and instructed his team to provide five new potential names for their new RaaS.
Collaboration with other malware families
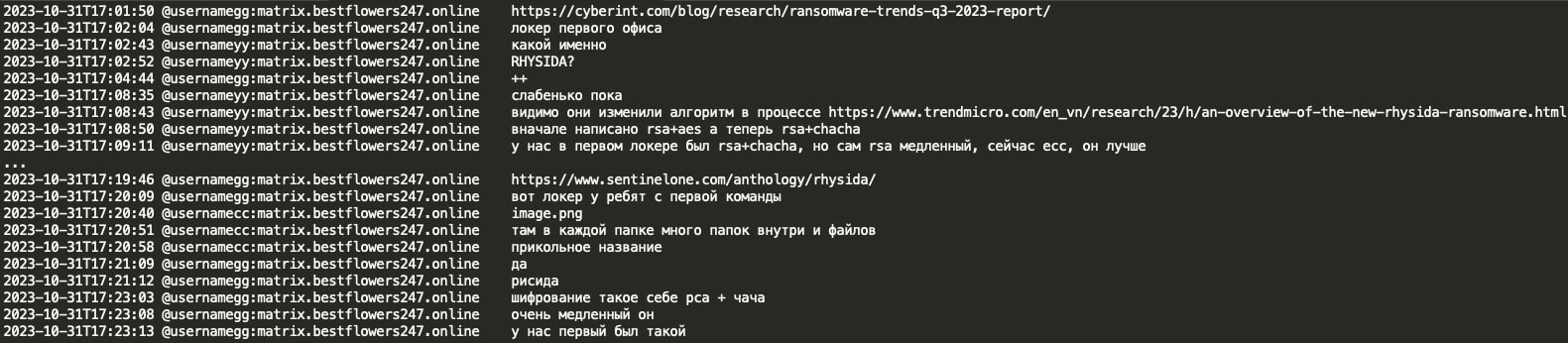
Black Basta-Rhysida
The first office/team appears to have its own locker - Rhysida ransomware. Black Basta gang members discussed that it is still weak and the encryption used (RSA + ChaCha20) resembles the first version of the Black Basta ransomware.
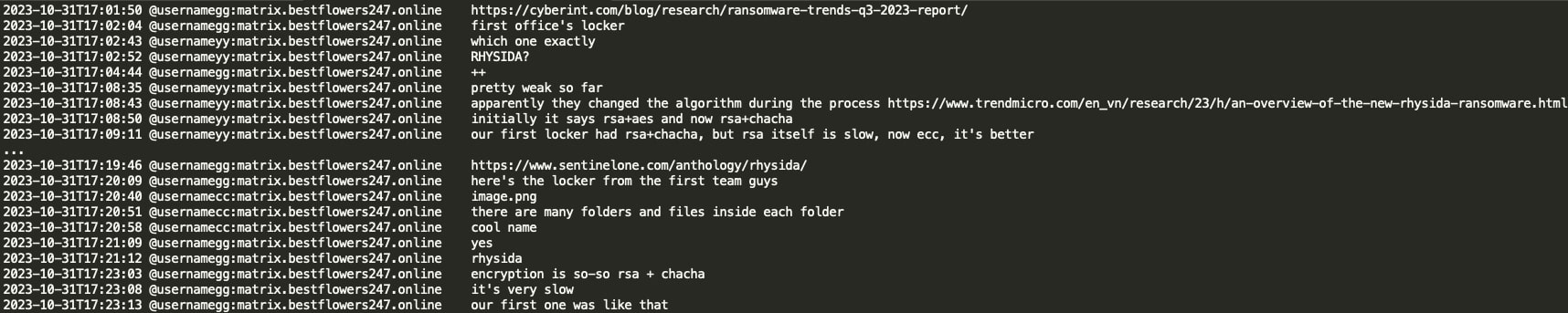
Black Basta-Cactus
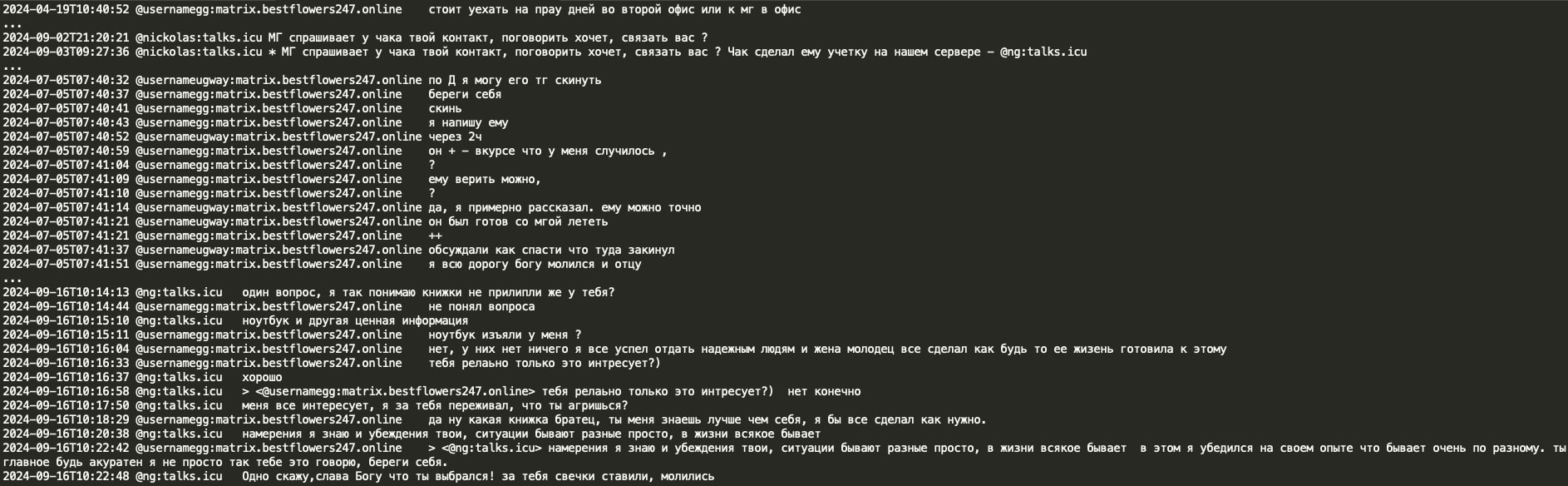
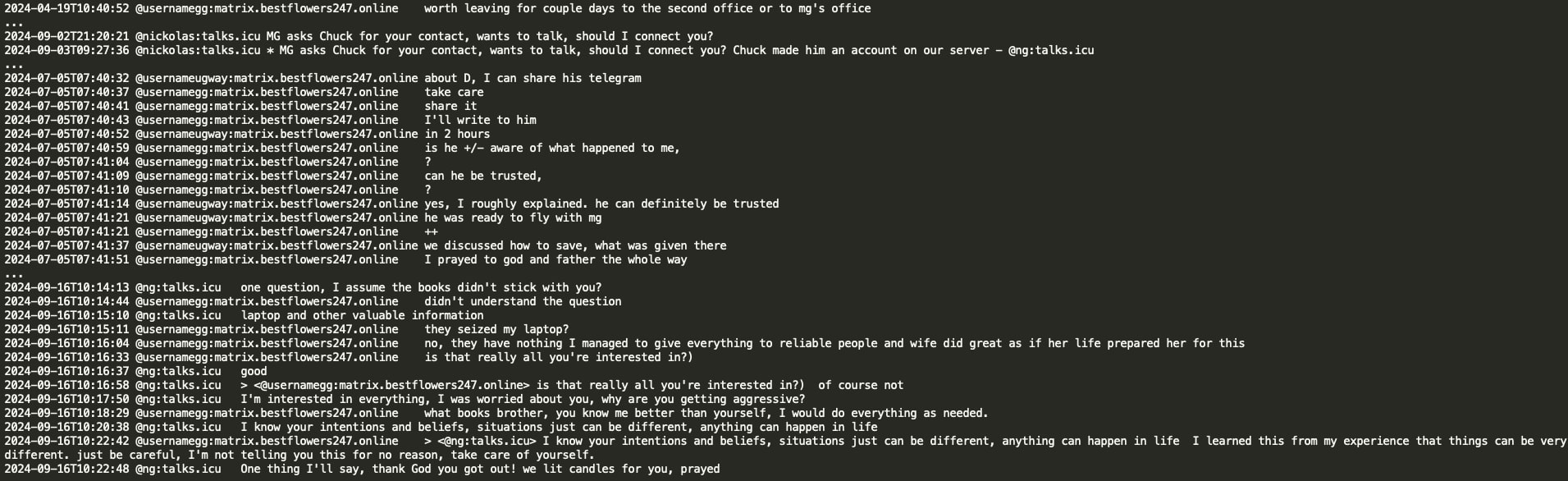
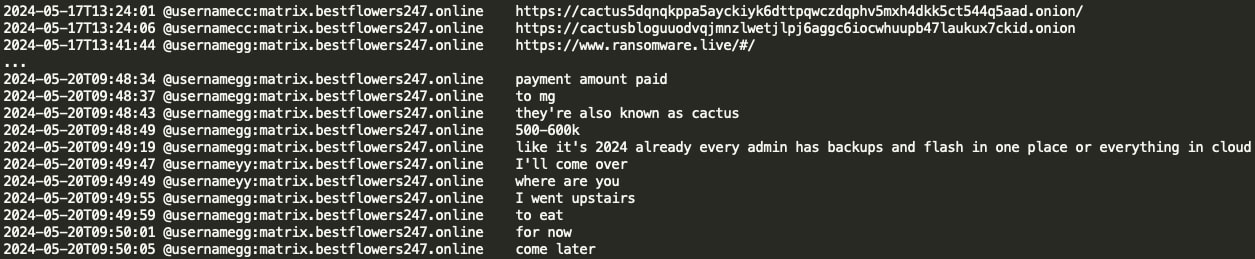
In May 2024, GG indicated that there is a team of 'MG' and that they are Cactus ransomware. The Black Basta chat logs contain several mentions of MG. Specifically, when GG was arrested abroad, MG and D apparently planned to fly there themselves to rescue him. GG stated that MG knows him better than MG knows themself (in the leak, MG’s matrix alias is ‘ng:talks.icu’ and their Jabber handle is ‘Znet’).
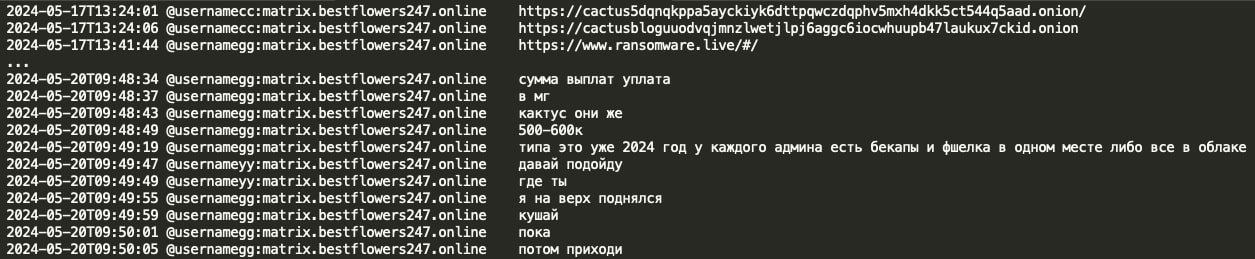
Here is GG mentioning that a payment of 500-600K (currency is unspecified) has been made to MG (aka Cactus ransomware), suggesting that Black Basta and Cactus ransomware teams work with each other:
Black Basta’s loaders: Qakbot, Pikabot, DarkGate and IcedID
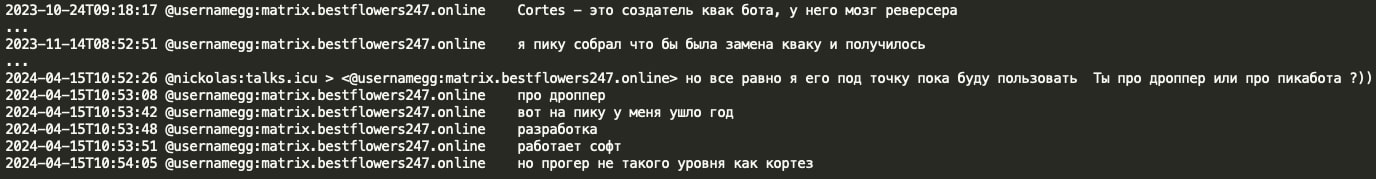
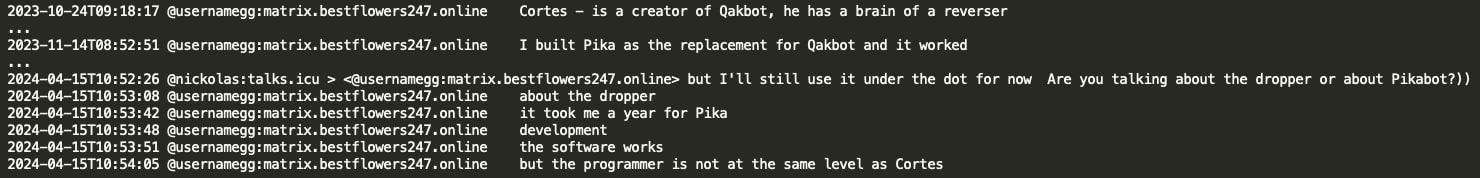
Mid April 2024, GG mentioned it took Black Basta a year to develop Pikabot after Qakbot’s takedown as the coder of Pika (or iPika) is not on the same level as Cortes (coder of Qakbot).
The developer of Pikabot appears to be a Ukrainian coder named mecor (aka n3auxaxl, w). It seems mecor (potentially a reference to the Hebrew word ‘Meqōr’) first relocated to Israel after Russia's incursion into Ukraine, however due to the Hamas attack on October 7th, they decided to relocate and settle in the Czech Republic.
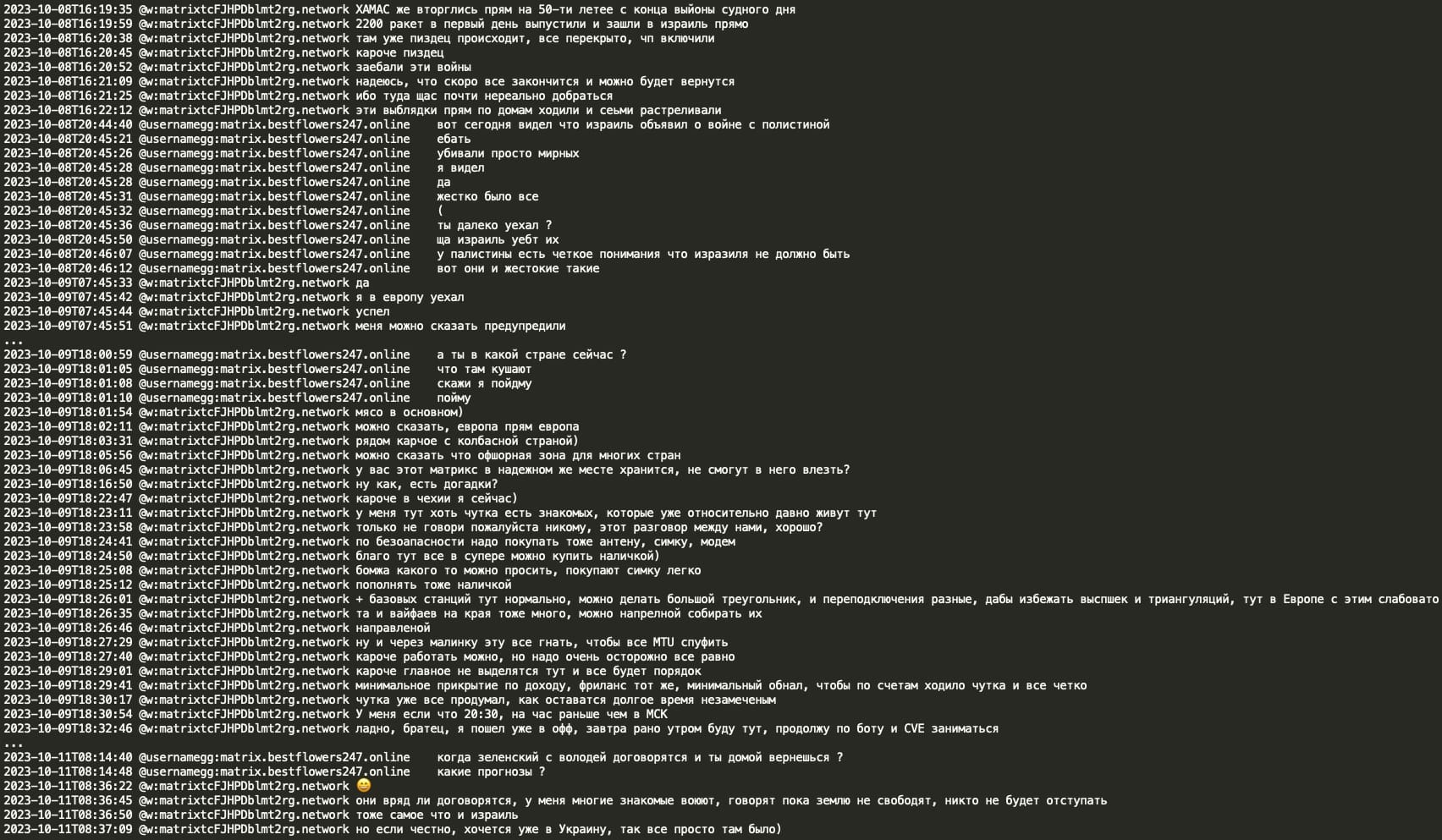
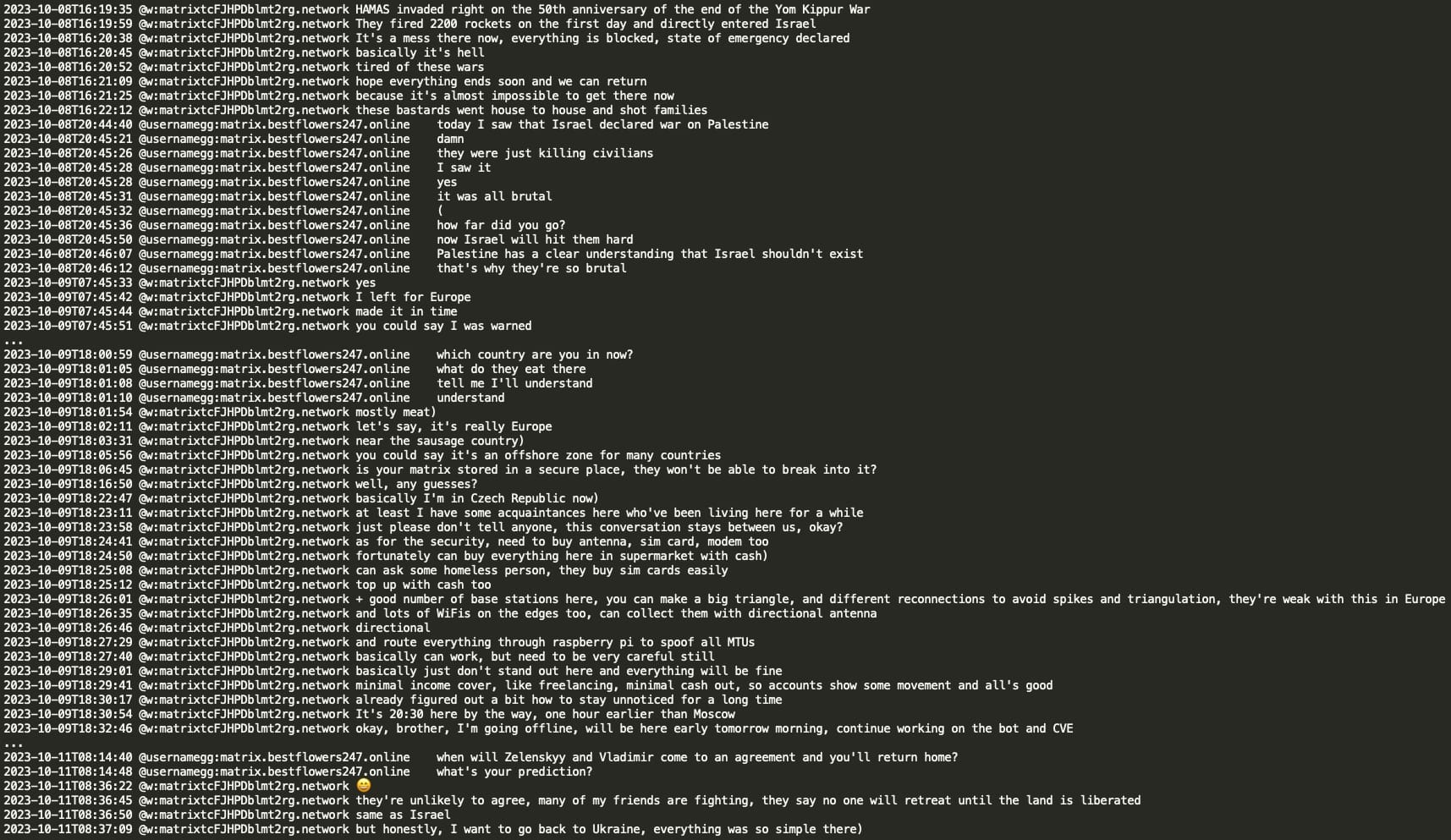
GG invited mecor to move to Russia and that he will help him with documents, housing and will give him money. Mecor can start working first from home and later GG will integrate him into the office team.
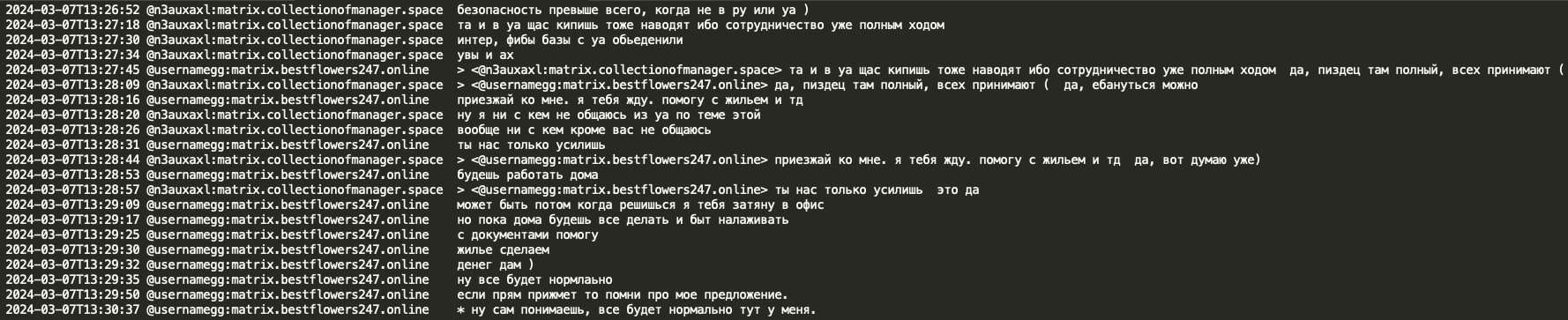
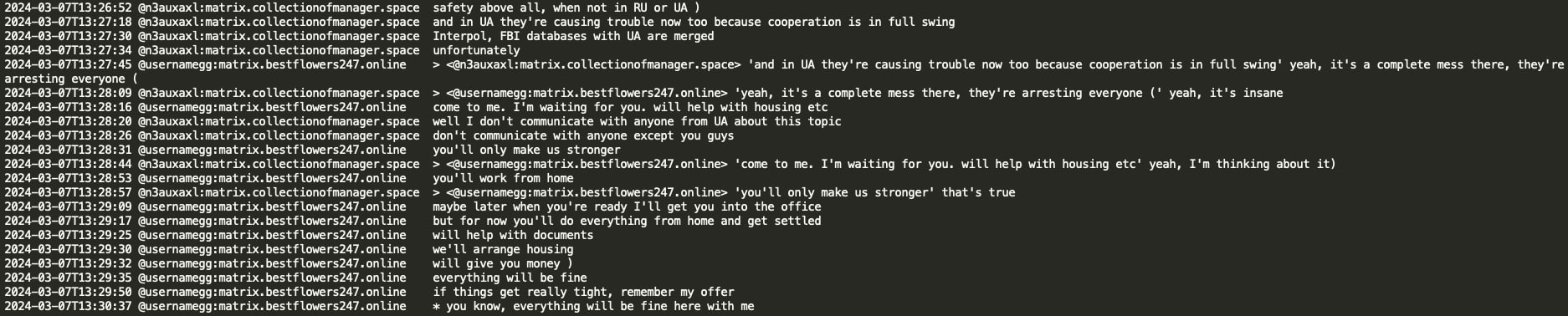
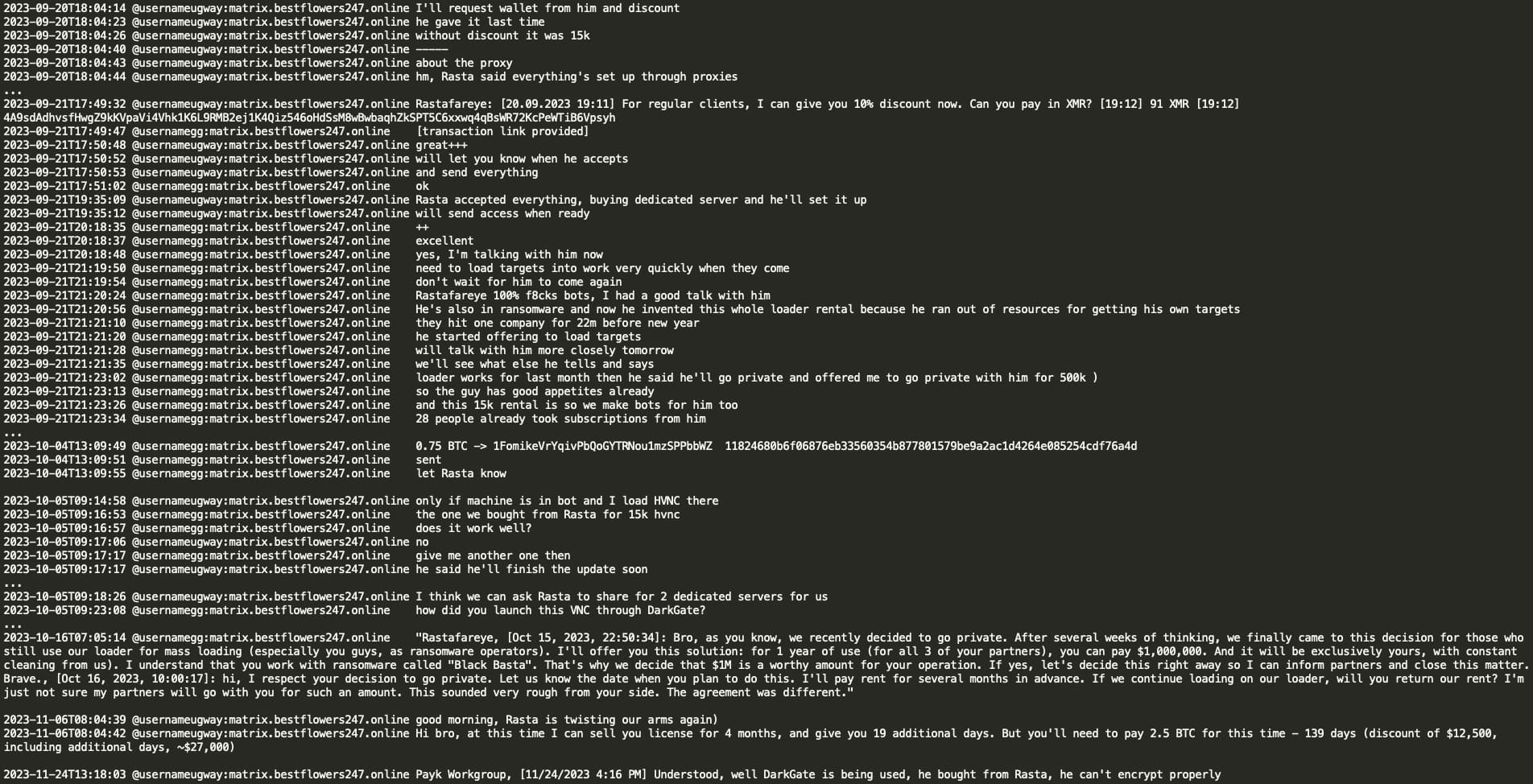
It appears that Black Basta had rented the DarkGate loader and HVNC from threat actor ‘Rastafareye’. Ugway (spammer) had direct communication with Rastafareye and negotiated discounts, rental terms, and other technical aspects of the DarkGate/HVNC malware. Ugway mentioned that Rastafareye was involved in the ransomware business himself, in addition to malware rentals. Rastafareye expressed a desire to go private, stating that he had enough subscribers (28 people), and offered $1M for a year of exclusive use of their loader. Ugway informed ‘Rasta’ that they would rent the loader for several months in advance.
From the leaked chat, we observed Black Basta transferring 0.75 BTC to Rastafareye. Ugway mentioned purchasing HVNC for 15K, and Rastafareye stated that he would extend the license for 4 months for 2.5 BTC.
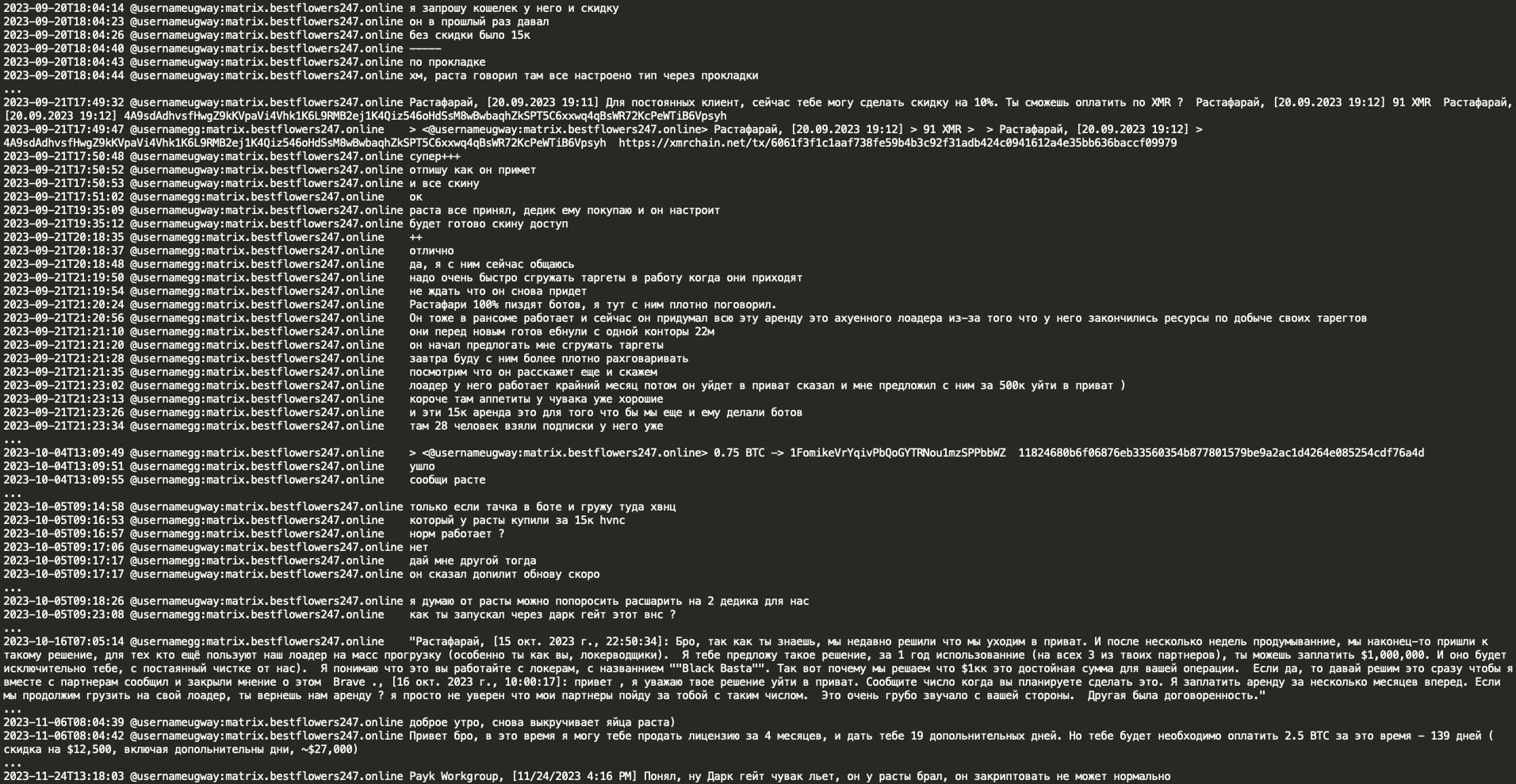
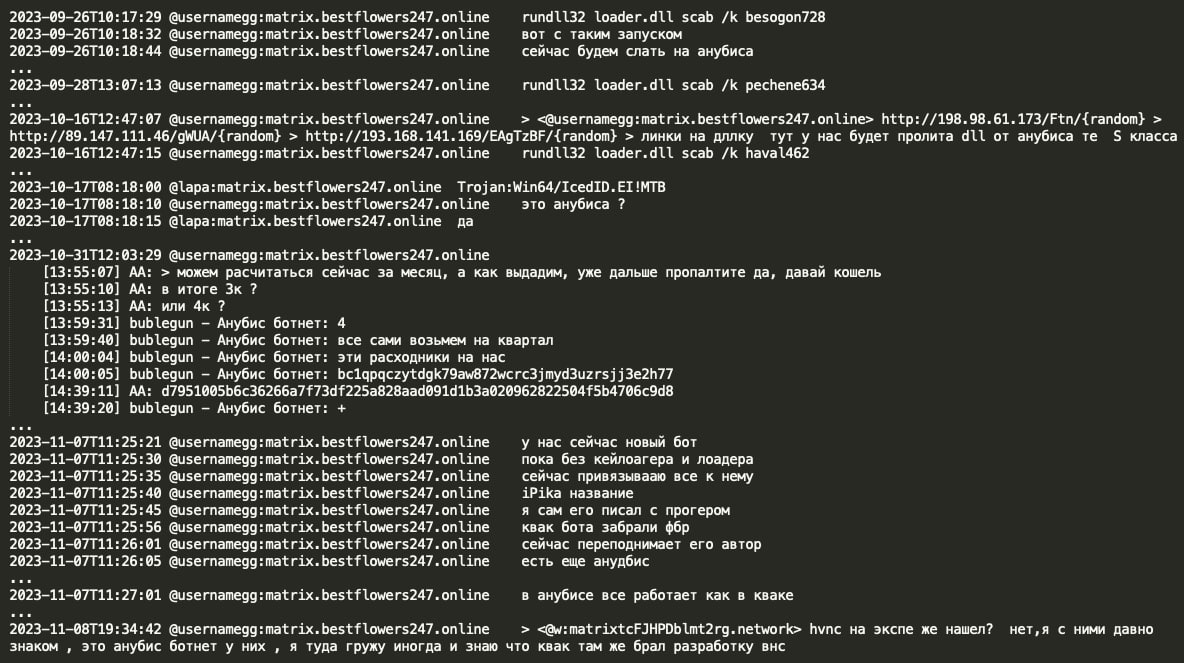
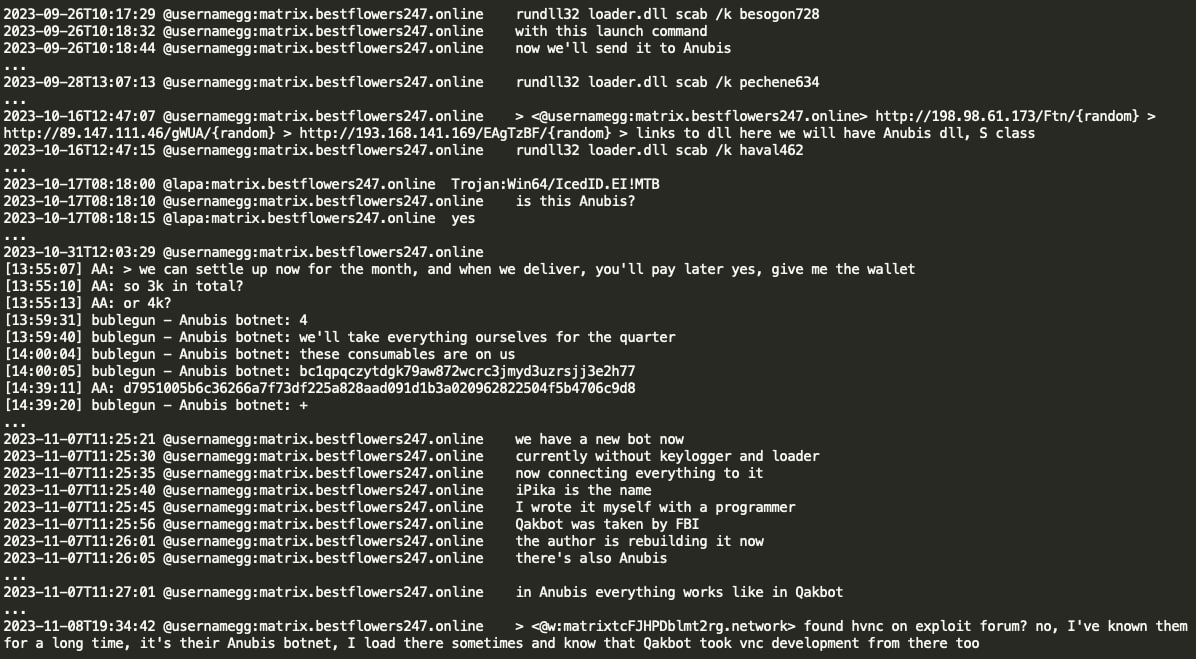
Furthermore, examination of Black Basta chats reveals their utilization of IcedID malware in their attack campaigns. IcedID malware which is believed to be created by Conti RaaS coder Leo appears to be leased by Black Basta gang, internally referred to as Anubis loader/botnet. Based on the signature identifier ‘Trojan:Win64/IcedID.EI!MTB’ and loader’s execution using rundll32.exe with function scab /k accompanied by arguments such as besogon728 or pechene634 or haval462, it can be inferred that the Anubis botnet is in fact IcedID malware. It seems that one month of IcedID rental incurred a cost of $4,000 USD for Black Basta group. GG indicated a longstanding familiarity with the Anubis team, noting Anubis' operational similarities to Qakbot and suggesting Qakbot's VNC development originated from Anubis malware.
Black Basta-LummaC2 Stealer
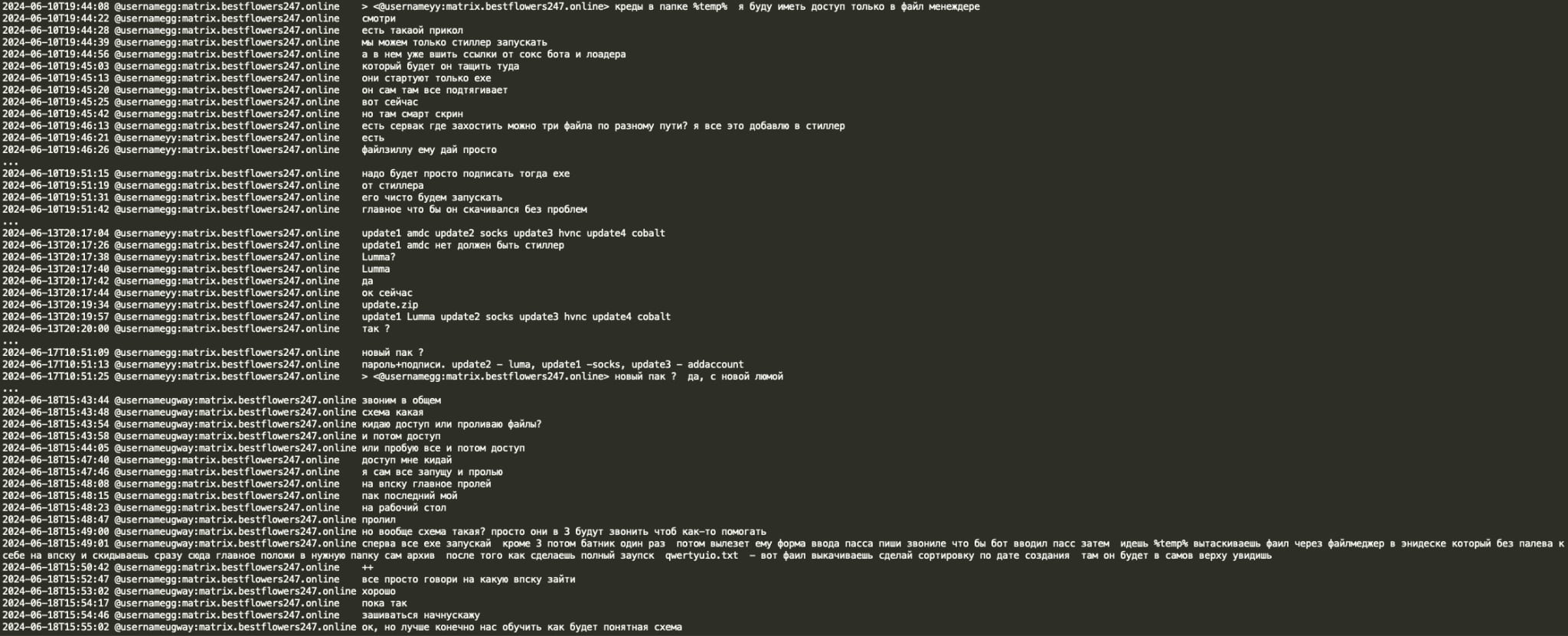
Black Basta gang appears to use LummaC2 infostealer both to steal credentials and as a dropper for additional malware (socks bot, HVNC, etc.). In the below conversation with YY (coder), GG (leader) and Ugway (spammer) go over an operation flow consisting of deploying a signed LummaC2 stealer executable which drops additional payloads in %temp% directory, then credentials and other stolen data collected in a file named qwertyuio.txt is exfiltrated through AnyDesk file manager to avoid detection.
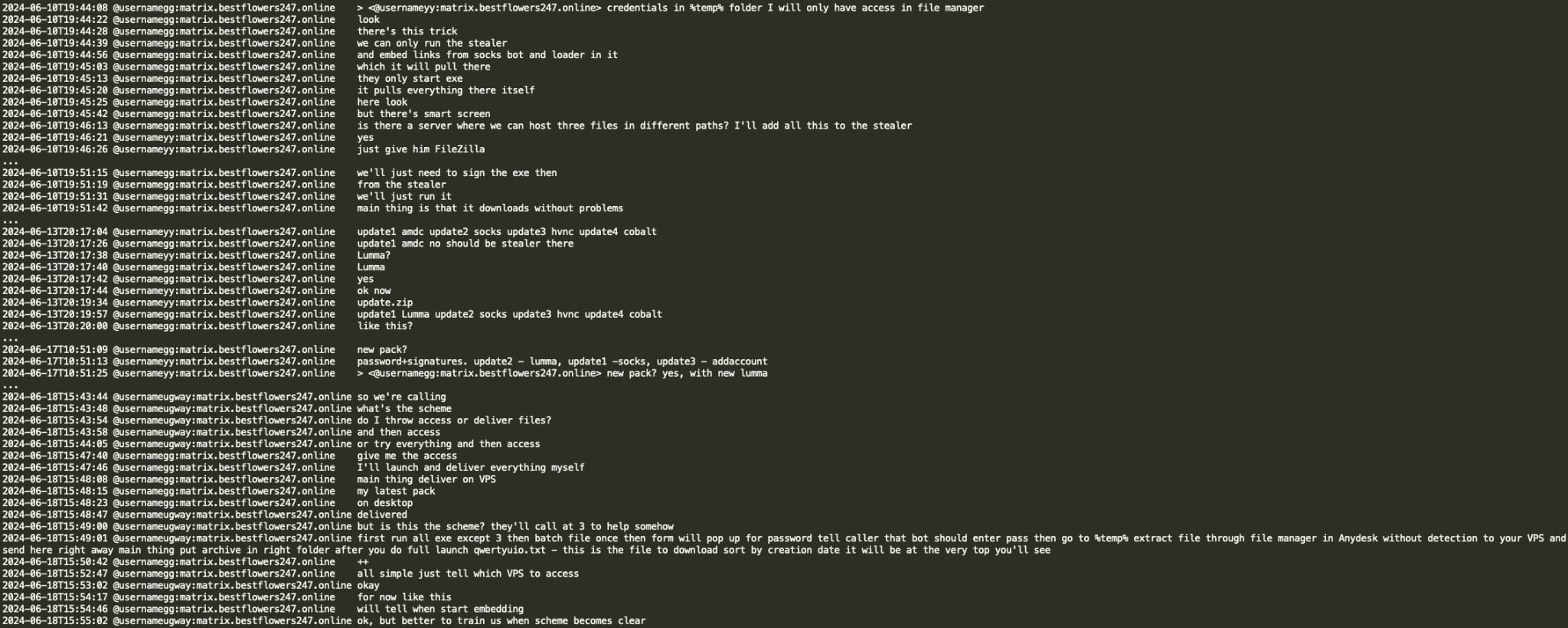
Black Basta’s custom C2 framework: Breaker
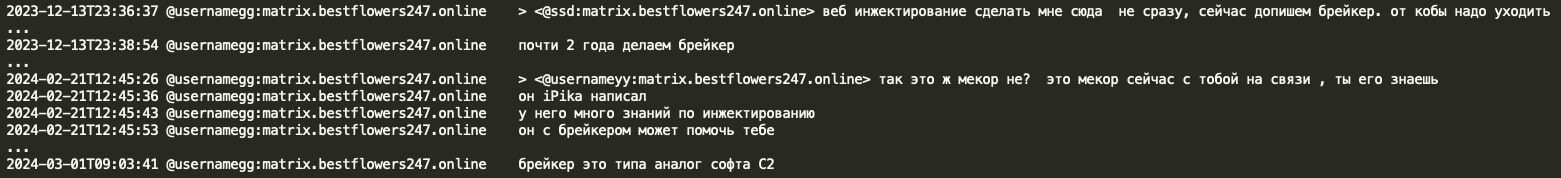
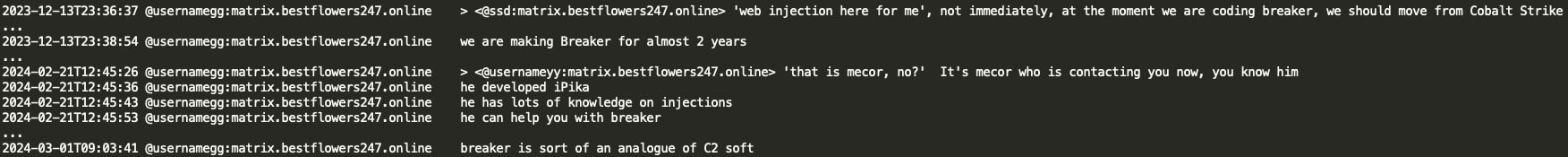
The Black Basta group appears to have developed its own post-exploitation C2 framework called Breaker. GG states that YY (coder) has been working on Breaker for the past two years and that they would like to transition from CobaltStrike/Metasploit frameworks to their custom tool Breaker. It appears that GG involved Pikabot developer mecor to assist YY with Breaker development as mecor has extensive knowledge around injections.
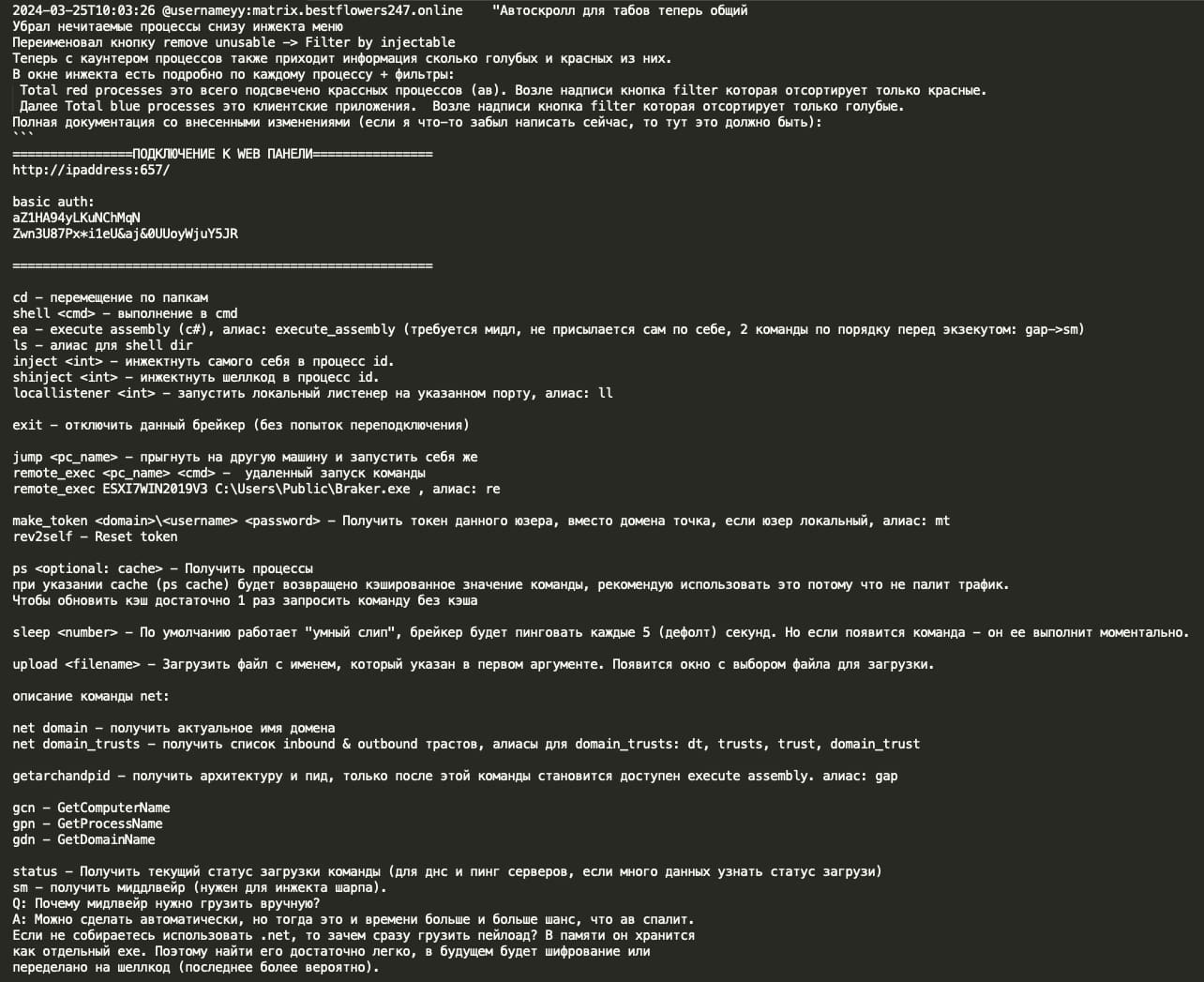
Below is the technical manual shared by YY with the rest of the Black Basta team, where we see that Breaker is designed for pentesting operations with a focus on stealth and persistence, including features to evade detection and maintain access across network systems such as:
- Command and control capabilities:
- Web panel interface
- Multiple communication protocols: TCP, DNS, and PING
- RC4 encryption for client-server communication
- Core functionalities:
- Process injection capabilities (self-inject and shellcode injection)
- Remote command execution
- File upload functionality
- Token manipulation (make_token, rev2self)
- Process listing with caching
- Remote system navigation
- .NET assembly execution
- User interface features:
- Web-based control panel
- Process filtering system (red for AV processes, blue for client applications)
- Interactive console with command history
- Global logs for technical monitoring
- Multiple target management through tabs
- Security features:
- Basic authentication
- Client IP banning capability
- Silent mode operation to avoid AV detection
- Process injection filtering
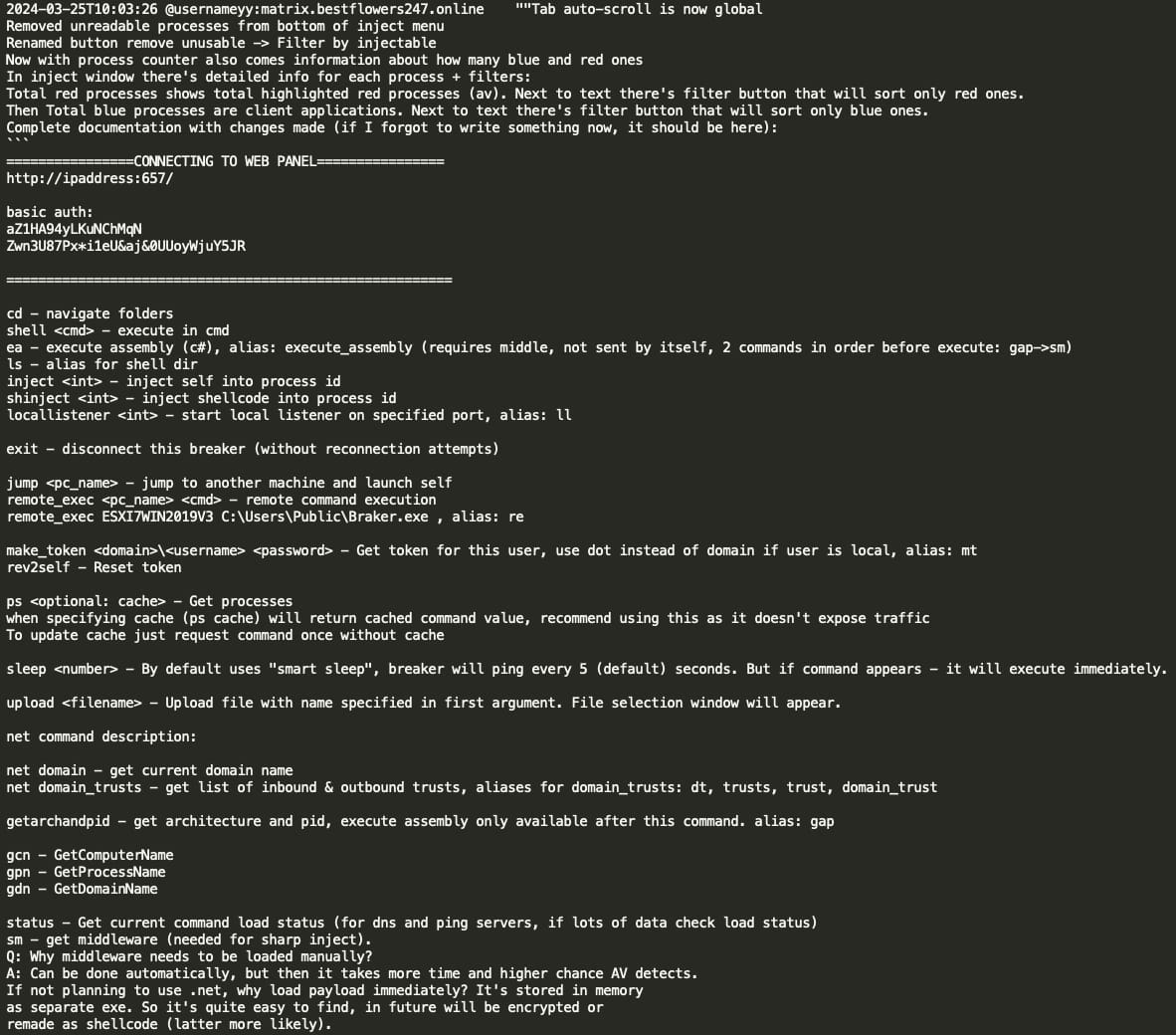
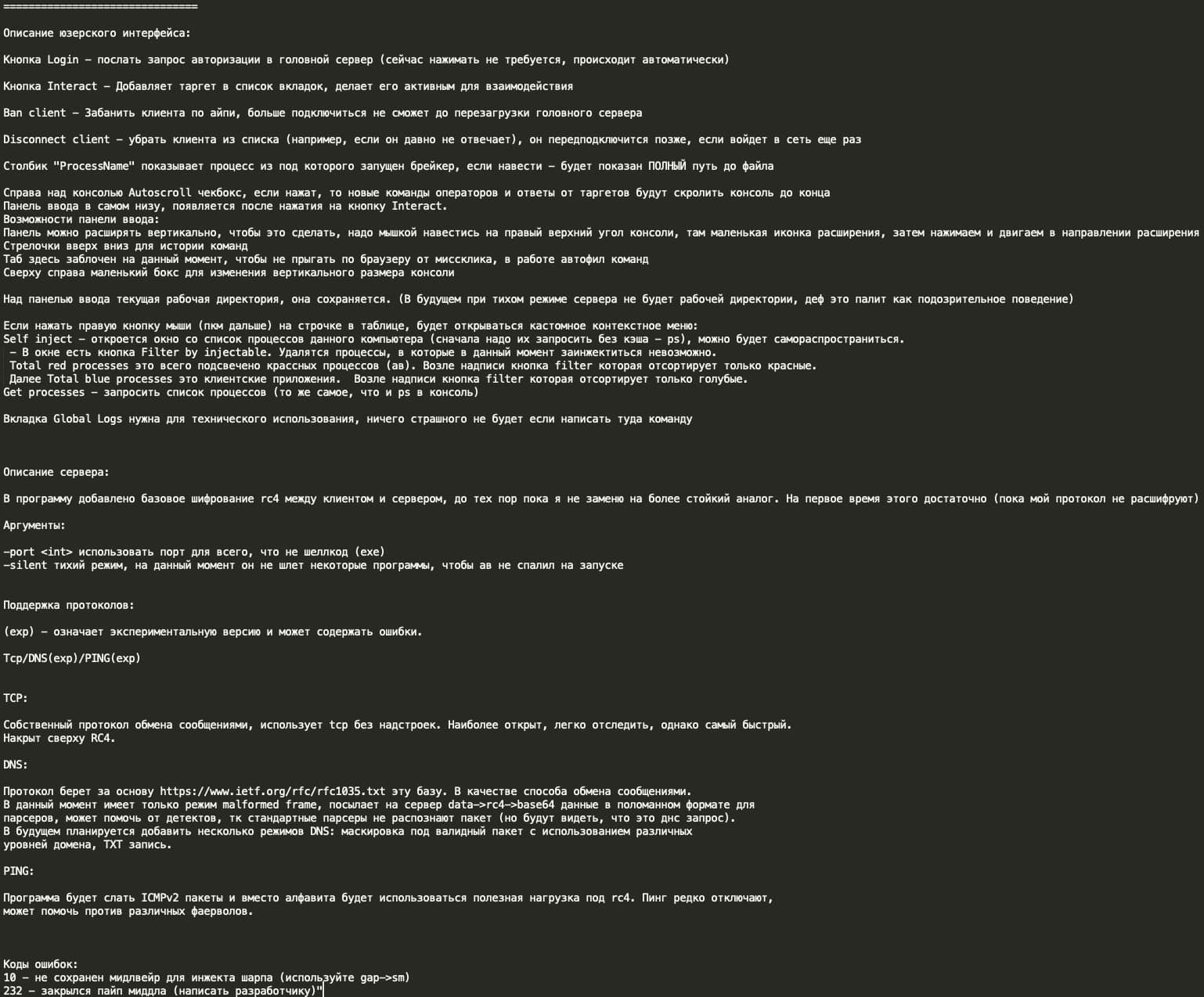
New ransomware development
After the Ascension Heath incident, GG became apprehensive and decided to work concurrently on new ransomware with mecor (developer of Pikabot), based on Conti source code. GG instructed mecor to commence work on the locker as soon as possible and to maintain confidentiality (only GG and mecor should have knowledge of it). GG believed that YY (developer of Black Basta) should not be aware of the new RaaS, as GG prefers that a new RaaS is not connected to Black Basta, and that security researchers, upon analysis, cannot connect them back to the Black Basta RaaS. GG mentioned that YY receives 10% of the Black Basta ransom and has already acquired a new apartment, car, and has established a few businesses on the side. If all goes well, mecor will receive 5% and a $100,000 USD initial bonus from the first victim lock.

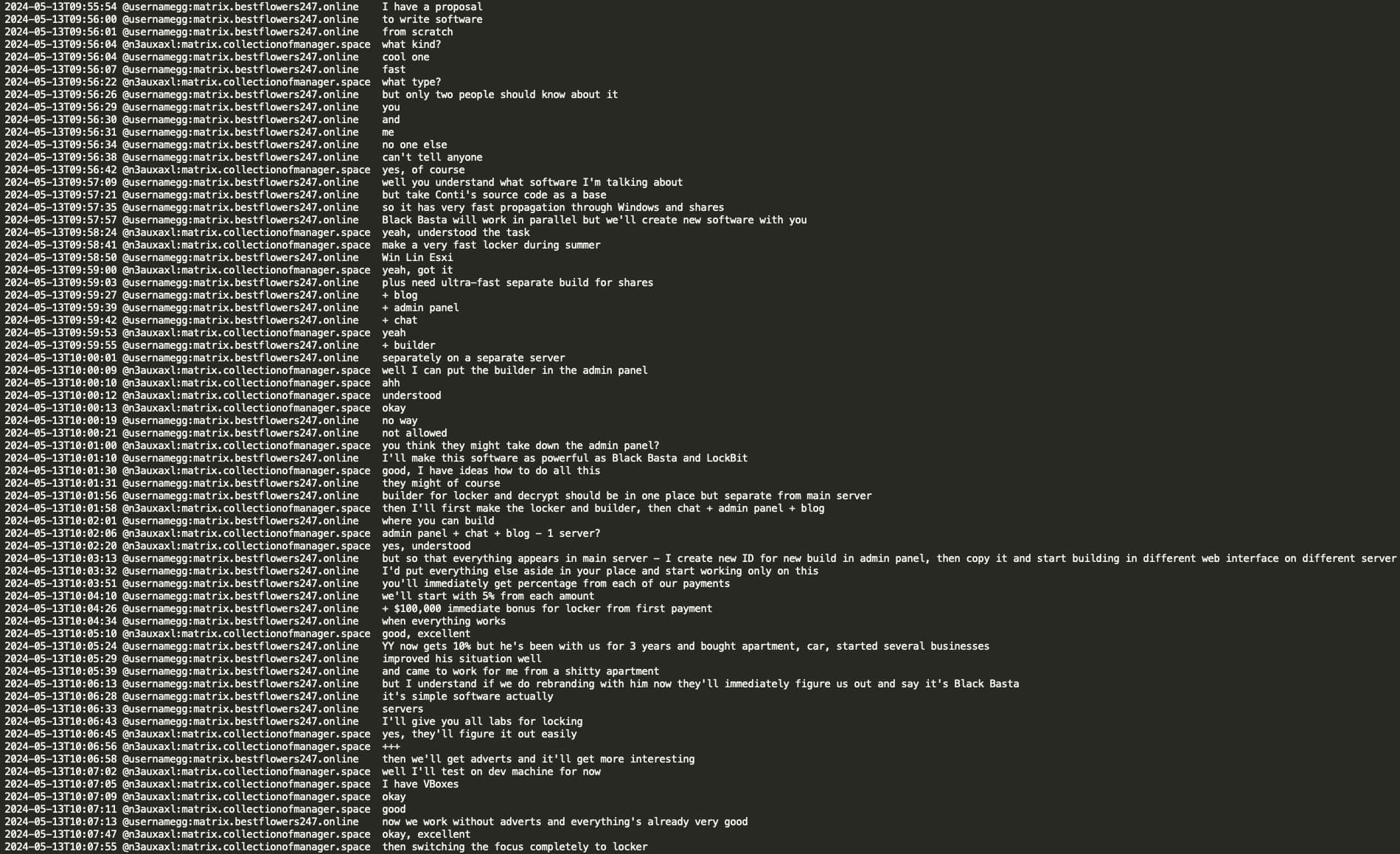
GG stated that he had squeezed everything out of Black Basta RaaS. Following the Ascension hack, they held a meeting at the office and fearing retaliation, they decided to replace everything: SIM cards, VPNs, VPS, and servers. GG expressed confidence that mecor could develop a new locker within a month, and mecor indicated that he will switch Pika off and will dedicate his full attention to the new locker.
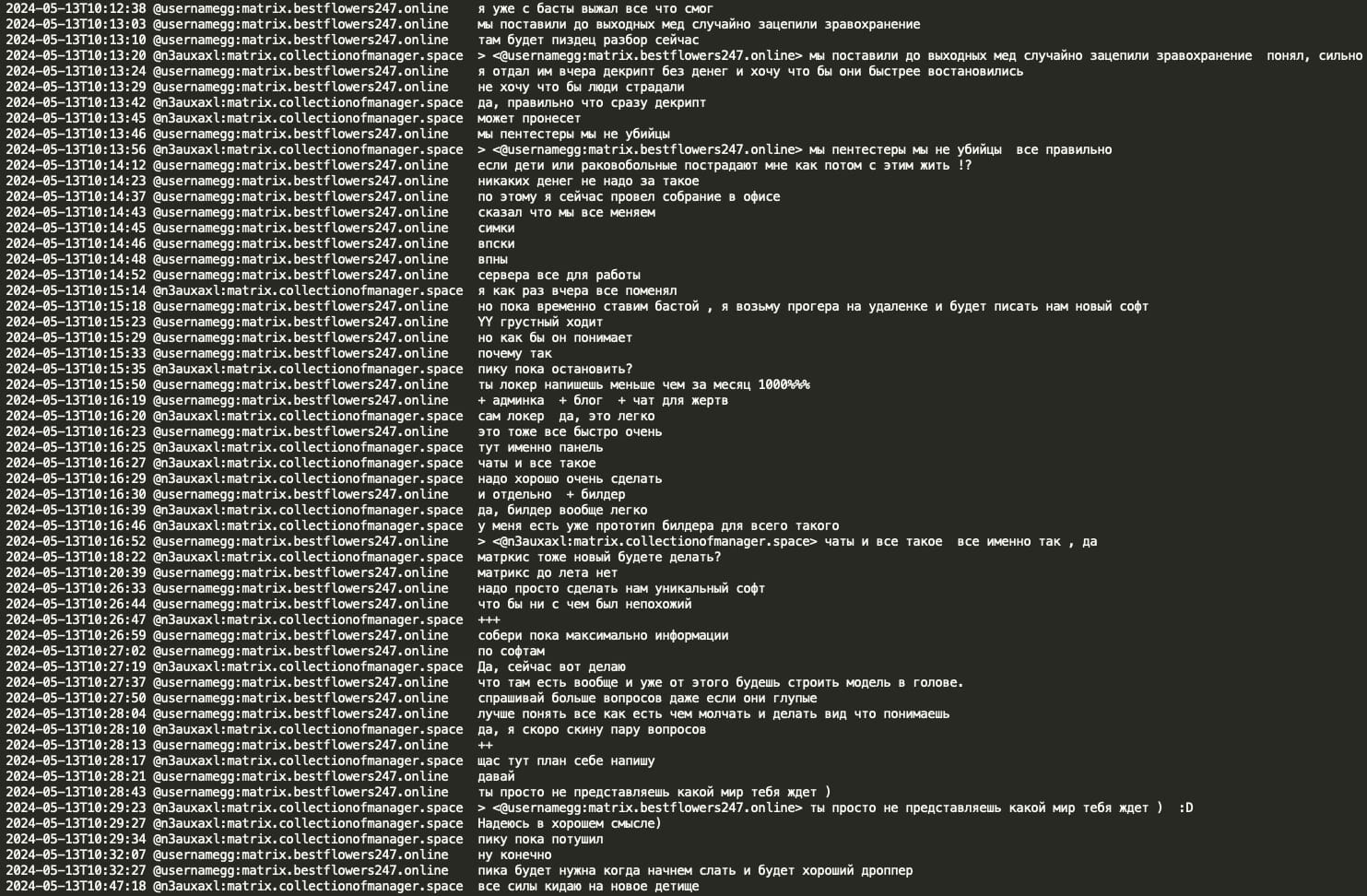
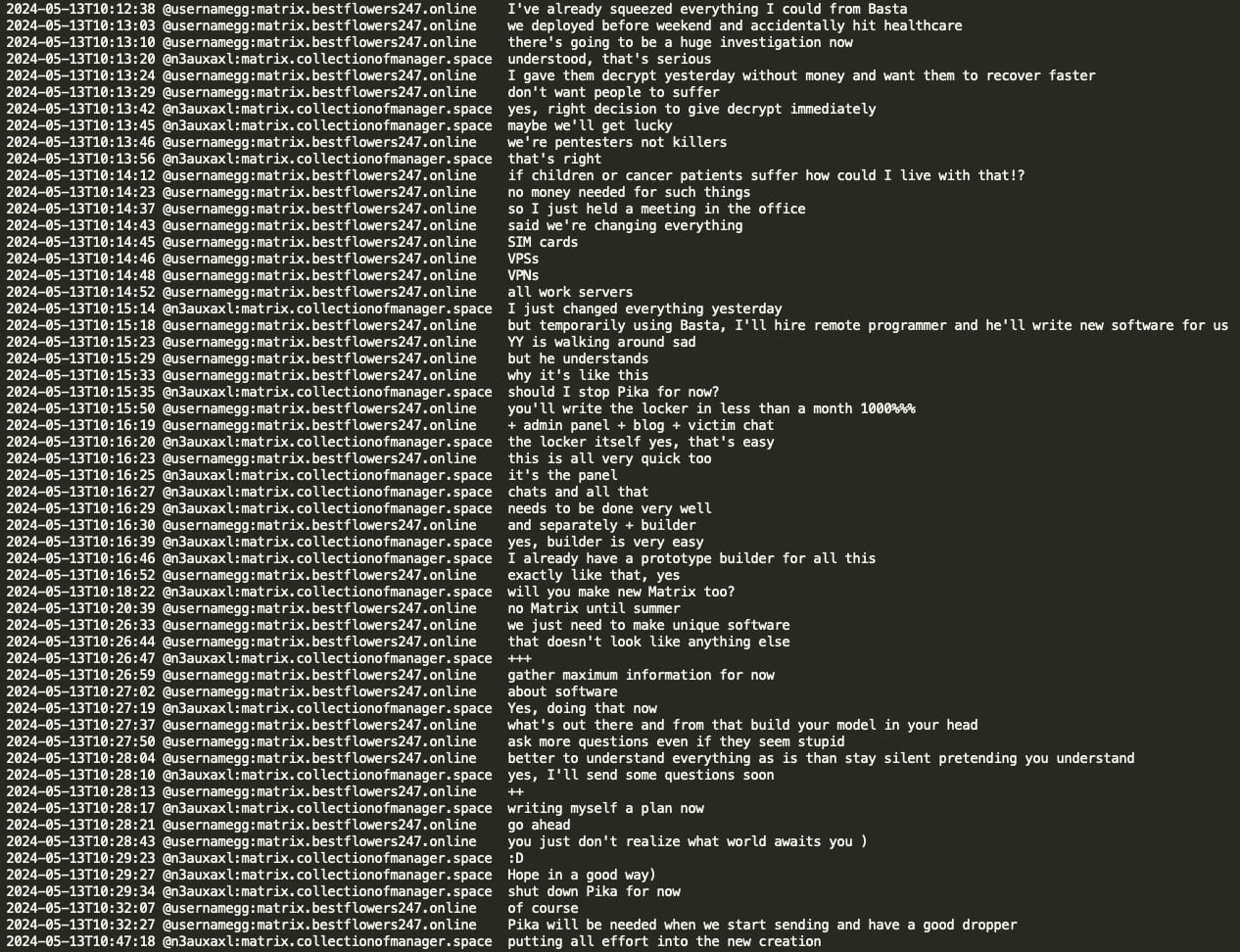
Mecor shared the prototype of a new RaaS in great detail – a sophisticated new ransomware locker written in C and ASM featuring a fully decentralized architecture with separate components for the locker, admin panel, chat, and blog, all operating through Tor with encrypted servers and Docker containerization for quick termination if compromised. The planned timeline indicates development of an MVP for PC locking by June 2024, with full debugging by July, and first deployments targeted for September 2024, while emphasizing security measures like fail2ban, closed ports, and complete system decomposition to ensure operational continuity even if individual components are compromised.
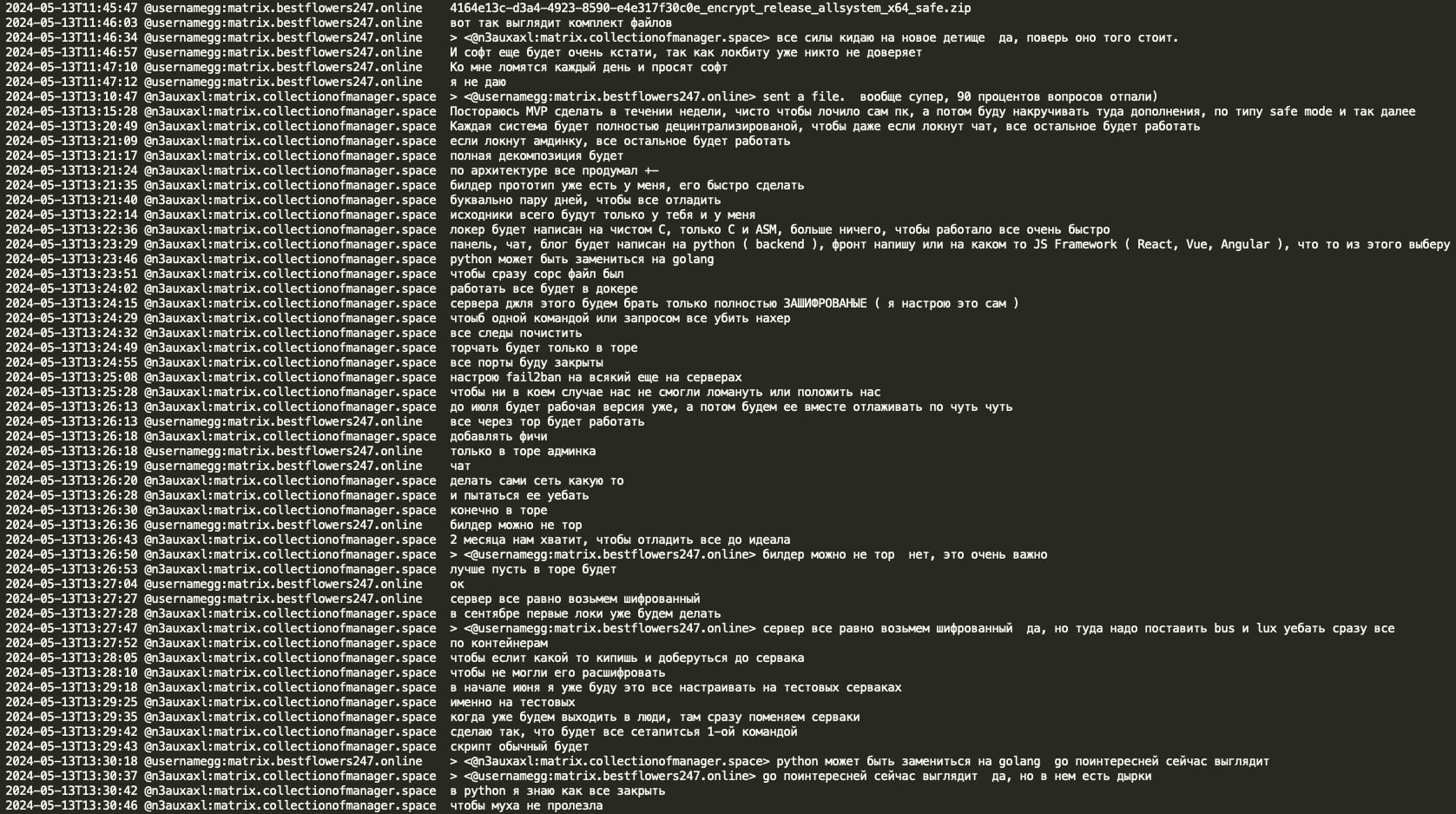
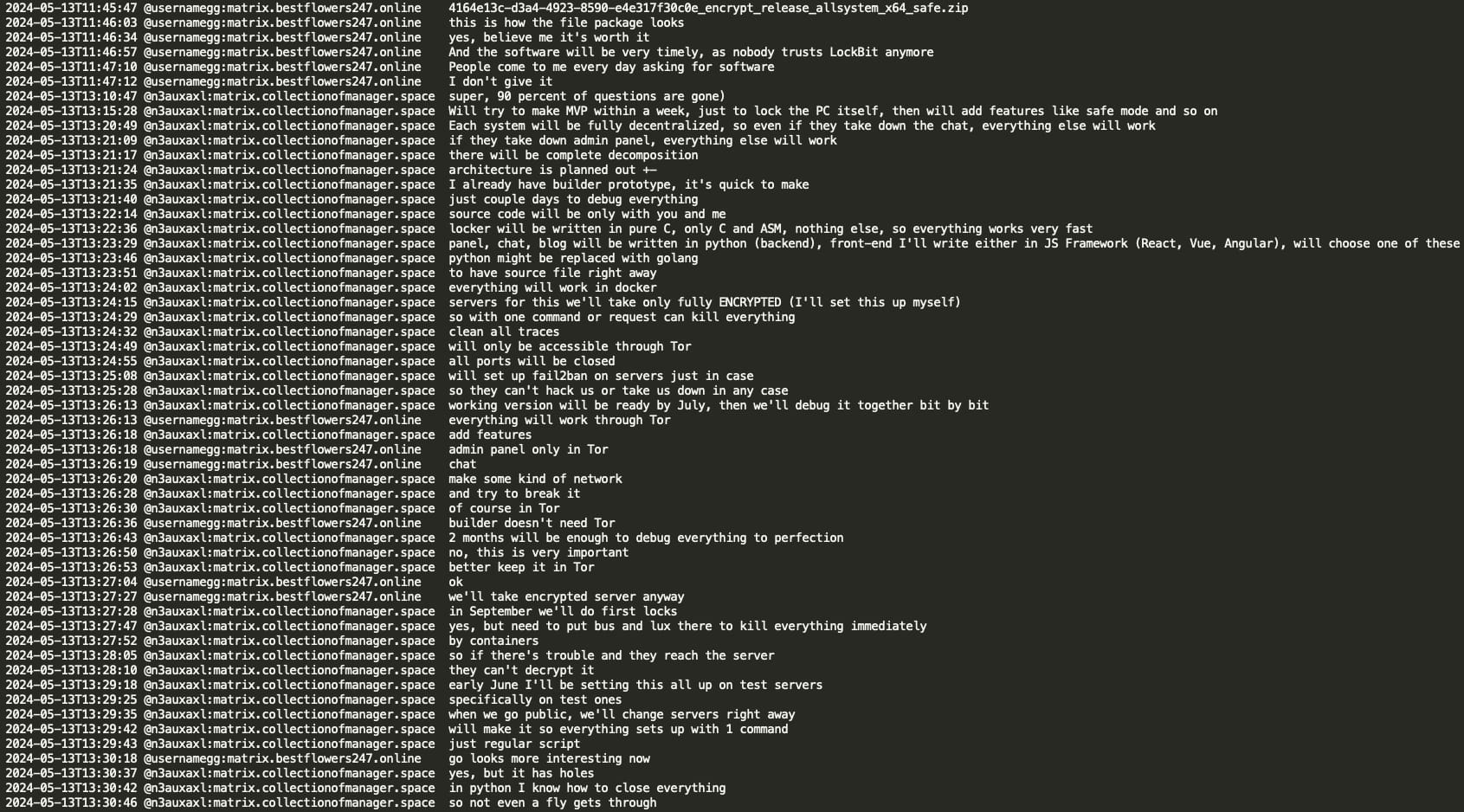
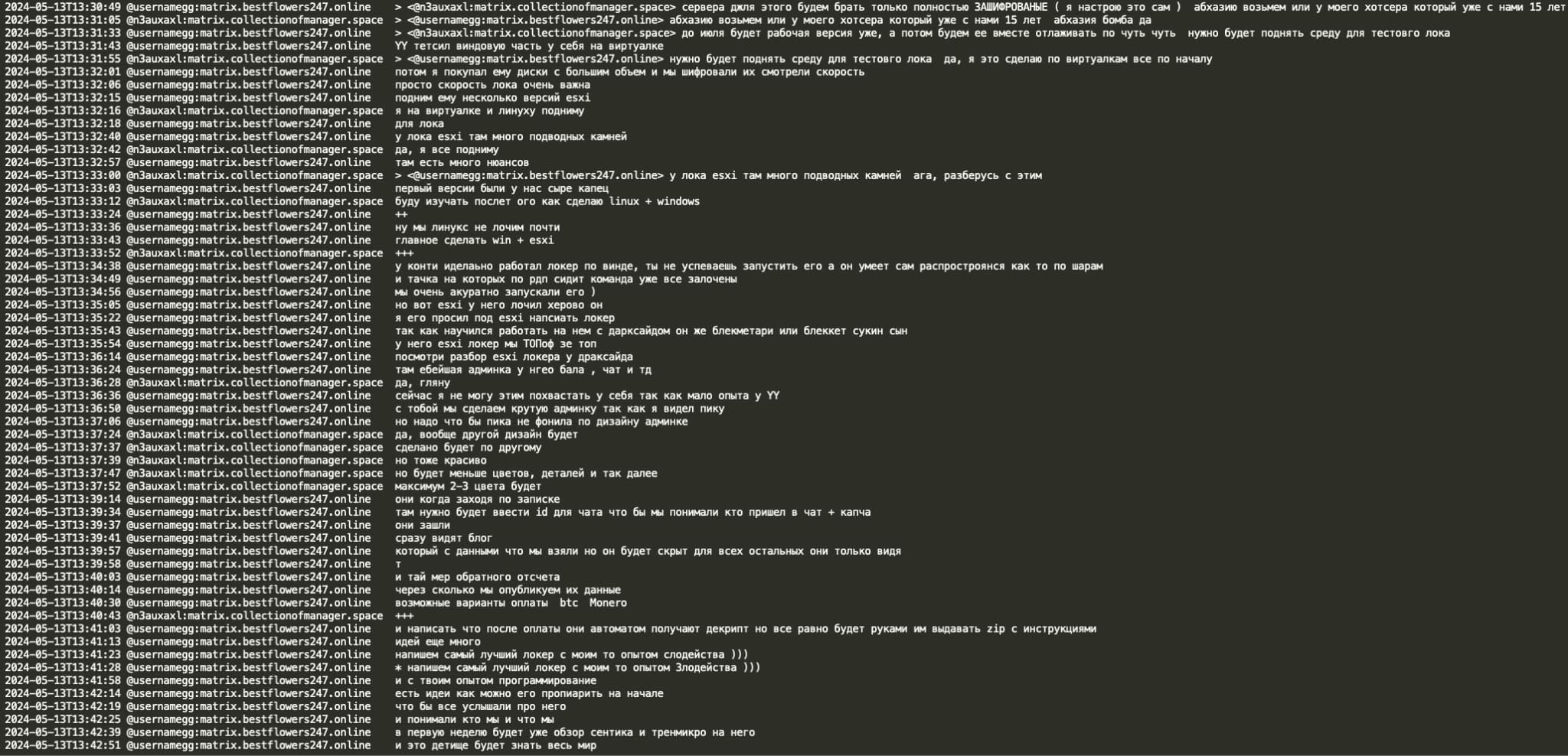
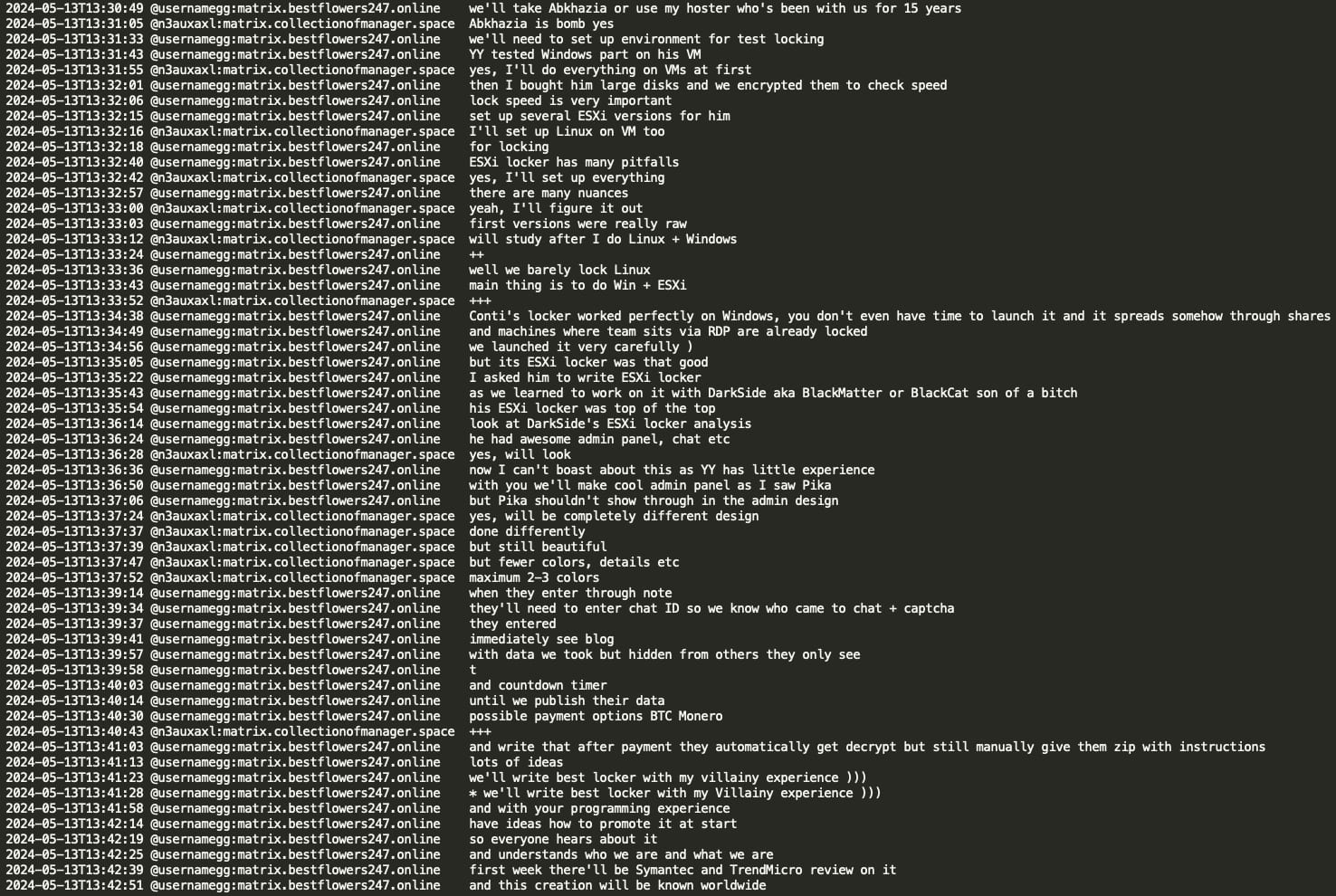
GG suggested focusing on Win(dows) + ESXi, mentioning that Black Basta seldom locks Linux. He stated that while Conti RaaS's Win was fast and effective, their ESXi was not optimal. GG recommended looking into Darkside/Blackmatter/BlackCat ESXi locker(s), praising its quality and admin panel. He emphasized the importance of encryption speed for new lockers and praised Pika's admin panel design. GG acknowledged that Black Basta's design was not exceptional due to YY's limited design experience. He cautioned against replicating Pika's design in the new locker to avoid attribution. Additionally, GG stated that they would utilize a familiar hosting provider in Abkhazia, with whom they have a 15-year history. This suggests that even if the ransomware gang rebrands, the hosting provider(s) for their infrastructure potentially remain consistent for over a decade.
Conclusion
The analysis of leaked Black Basta chats revealed potential connections to Russian authorities, the group's use of AI, and collaborations with other ransomware and malware operations. The chats showed that Black Basta has two offices in Moscow, the gang utilizes ChatGPT for various malicious purposes, including generating deceptive messages and rewriting malware code. We found out that Black Basta has also worked with other ransomware groups, such as Rhysida and Cactus, and used loaders like Qakbot, Pikabot, DarkGate and IcedID.
Furthermore, we discovered that Black Basta group developed a custom C2 framework called Breaker and were working on creating new ransomware, indicating a possible rebranding effort.
Reviewing the Black Basta chat leaks demonstrated that the group's operations have not fundamentally changed from the Conti RaaS era. They continue to operate as an enterprise with multiple physical locations in Russia and maintain different teams of callers, negotiators, cryptors, coders, traffers, and spammers. They persist in operating under the belief that Russian authorities will shield them from repercussions.
We have witnessed that although Conti/Trickbot affiliates may have joined different RaaS gangs, they kept maintaining valuable connections with each other. Every time a ransomware rebrand takes place, they regroup, learn from their mistakes, develop more sophisticated innovative tools (sometimes owing to AI), and continue under a new name as long as RaaS business generates financial gain.
Trellix has observed that Black Basta's activity has decreased in 2025. This may be related to the arrest of Black Basta's leader GG and the Ascension Health attack in 2024. As GG stated, he was apprehensive of retaliation from US Law Enforcement and that he ‘squeezed’ everything possible out of Black Basta. It was a time for rebranding with a new locker that would not be easily connected to Black Basta. However, in light of the Black Basta chat logs leaks, we believe this will be challenging as we have gained valuable intelligence on Black Basta's infrastructure, connections, inner workings, and tooling. This knowledge from chat leaks makes it difficult for the Black Basta gang to completely abandon the way they operate and start a new RaaS from scratch without a reference to their previous activities.
RECENT NEWS
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
-
Oct 28, 2025
Trellix AntiMalware Engine secures I-O Data network attached storage devices
-
Oct 23, 2025
Trellix CyberThreat Report Reveals Blurring Lines Between Nation-State Espionage and Financially Motivated AI Attacks
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.