Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Using EDR to Uncover an Info-Stealing Campaign that Used Legitimate Binaries
By Ale Houspanossian and Joe Malenfant · June 17, 2024
Are Monday’s ever quiet?
The short answer is: rarely. On a particularly quiet Monday morning in March 2024, our Research team discovered an interesting sequence of high confidence detections in Trellix EDR telemetry. Analysts dove into the telemetry and uncovered what appeared to be a fresh and cunning attack campaign affecting customers in Latin America and Asia Pacific.
What threat hunters ultimately discovered and documented was multiple behaviors related to initial access, credential access, persistence, defense evasion, privilege escalation, resource hijacking and more. The extremely low detections in threat feeds indicated this was a novel campaign specifically built to evade detection by modern threat detection tools.
This is the story of how we found it, and how we’re protecting you. The in depth research from our Advanced Research Center can be found here.
A little trickery goes a long way
Adversaries had managed to trick users into downloading password-protected archive files containing trojanized installers. When unsuspecting victims extracted the archive files, they would find (and eventually execute) an installer file named 'Setup.exe'. In reality, it was a renamed copy of a Cisco Webex Meetings application (ptService.exe), which covertly loaded a malicious DLL file (also contained in the archive file), which led to the execution of an information-stealing module.
The initial loader, executed via DLL Sideloading, was identified as HijackLoader. HijackLoader was used to download and execute an infostealer, identified as Vidar Stealer. Vidar Stealer can collect credentials and other sensitive data before sending it back to the attackers’ servers.
It is highly probable that victims were not interested in installing a Webex application but something else. By hijacking the execution of a legitimate Webex app process, the malware was able to fly under the radar of antivirus and EDR solutions. However, Trellix EDR detected multiple threat behaviors into a single, aggregated and actionable High Severity Threat alert. This way Trellix EDR puts SOC analysts on track to triage, investigate and respond to the cyber threat.
Attacker TTP’s mapped to MITRE ATT&CK
Attackers used a litany of tactics, techniques and procedures designed to circumvent threat detection tools. We’ll cover these at a high level, and more detail can be found in the blog.
Initial Access, Initial Execution and Defense Evasion: we’re all too familiar with loading an application and it having to perform some sort of update to run. In this case, adversaries tricked users into downloading malicious password-protected archive files that contained a Cisco WebEx installer and malicious DLLs. User execution (ATT&CK T1204) on a file named “Setup.exe” served as the initial execution.
Adversaries sideloaded a malicious DLL through the legitimate application (MITRE T1574.002). The Malicious loader (HijackLoader) is injected into a Windows Binary (MITRE ATT&CK T1055). Execution of HijackLoader results in the download and execution of an AutoIT3 binary (Vidar Stealer) (MITRE ATT&CK T1105, T1059.010), which in turns accessed internal files of both Chrome and Firefox web browsers, as well as Zoom (MITRE ATT&CK T1555.003) and maintains sustained network connectivity to C2 server (MITRE ATT&CK T1071.001). It is inferred that the malware managed to steal data and exfiltrate it to the C2 server (MITRE ATT&CK T1041).
The malware employs a known technique for bypassing User Account Control (UAC) and exploiting the CMSTPLUA COM interface for privilege escalation (MITRE ATT&CK T1548.002). Once privilege escalation had succeeded, the malware added itself to Windows Defender’s exclusion list for Defense Evasion (MITRE ATT&CK T1562.001). Later, .NET binaries are launched and injected (MITRE ATT&CK T1055) in an attempt to launch a cryptominer (MITRE ATT&CK T1496)
Defending with Trellix EDR
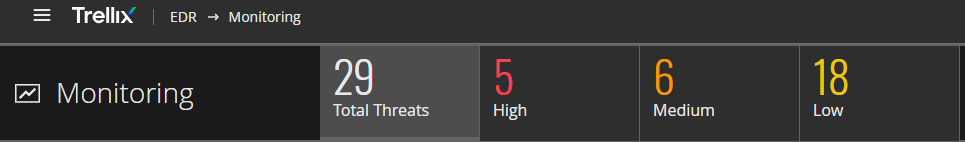
Trellix EDR Monitoring Workspace provides an overview of aggregated detections and alerts using three main severity levels (High, Medium and Low). This is a convenient way to navigate the Threat detections. We encourage customer security teams to triage every High and Medium Severity threats as part of their daily operations.
In this case, Trellix EDR was effective in unveiling the malicious activity. By delivering a single, aggregated and actionable High Severity Threat alert, Trellix EDR puts SOC analysts on track to triage, investigate and respond to cyber threats.
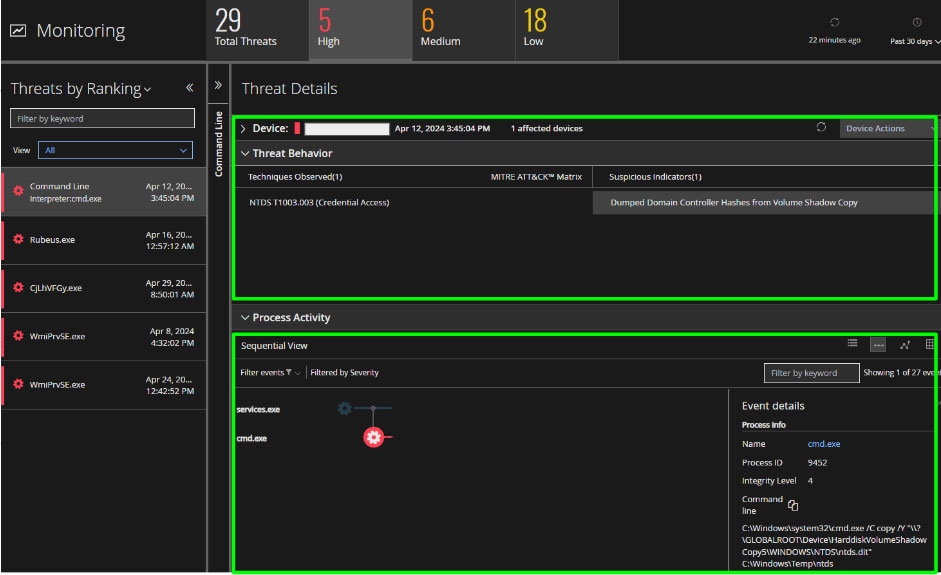
As shown in the next screenshot, Trellix EDR provides a clear view of the execution chain. There are multiple detections and alerts mapped to this activity tree.
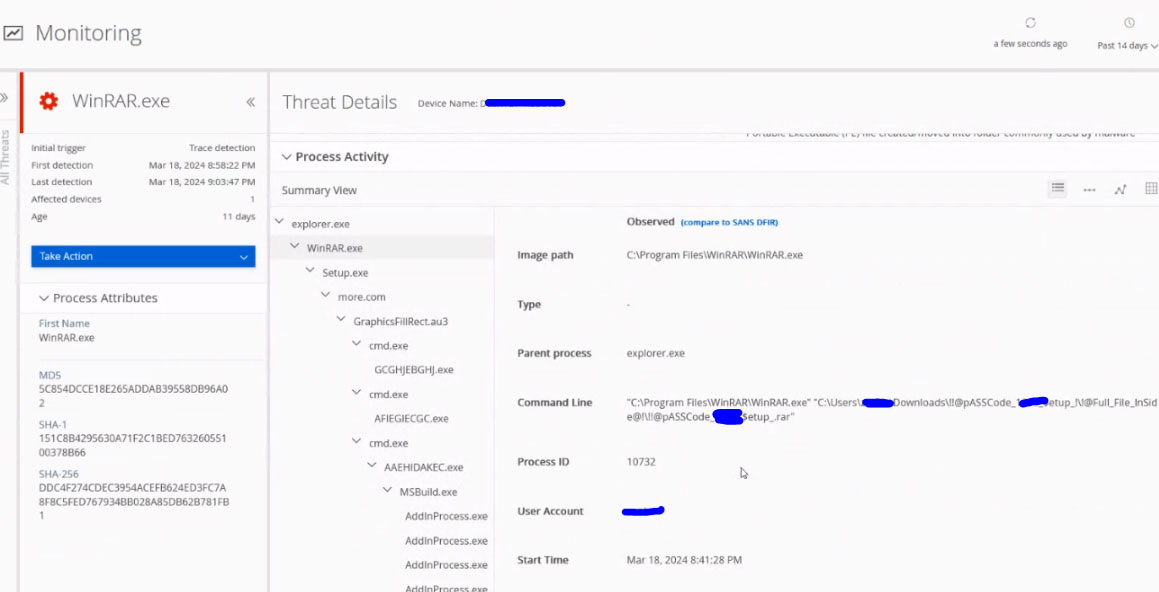
The typical workflow for triaging an alert like this, would involve checking the specific Threat Behaviors detected by Trellix EDR (in the same Trellix EDR Monitoring UI).
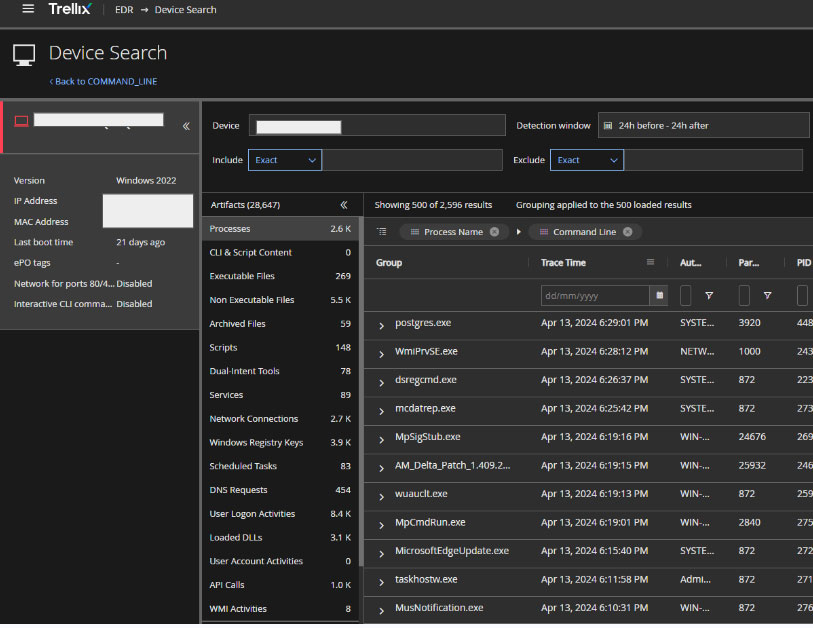
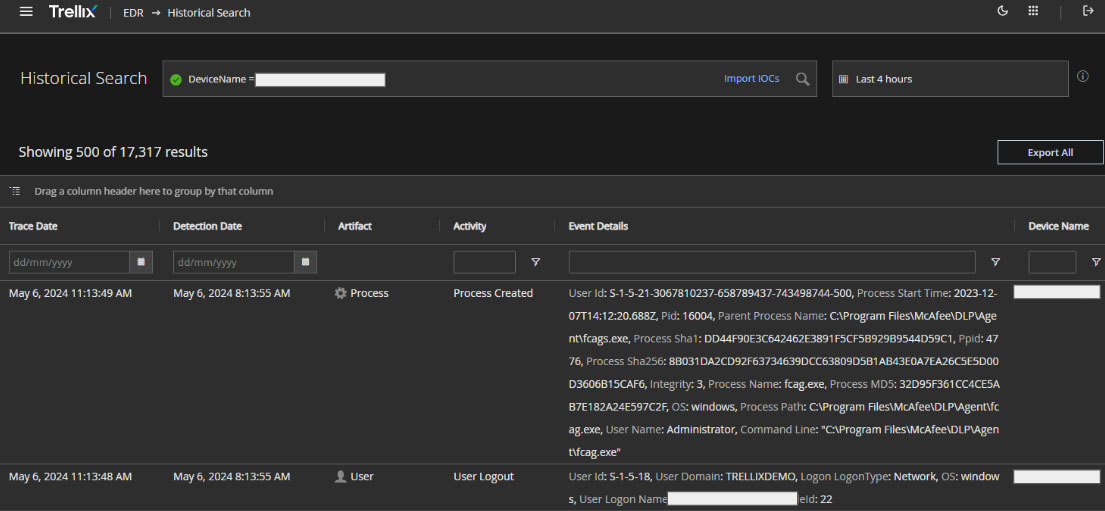
Trellix EDR provides the Device Search Workspace, which can be used to get into the details of the activity executed in the endpoint.
To try Trellix EDR for yourself, just request it here: https://www.trellix.com/request-demo/
RECENT NEWS
-
Apr 7, 2025
Trellix Strengthens Focus on Customer Engagement and Regulated Industries with Executive Appointments
-
Feb 5, 2025
Trellix Accelerates Secure Cloud Adoption in Australia with New Government Accreditations
-
Jan 28, 2025
Trellix and NEXTGEN Accelerate Cybersecurity Platform Adoption in Australia and New Zealand
-
Jan 22, 2025
Trellix Welcomes New CEO to Lead Next Phase of Growth
-
Jan 14, 2025
Trellix Accelerates Global Partner Growth with Revamped Xtend Partner Program
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
