Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Trellix NDR: Unleashing the Power of Trellix Wise AI for Unmatched Network Security
By Brajesh Kumar, Praveen Soraganvi and Ravikanth Rudrabhatla · March 13, 2025
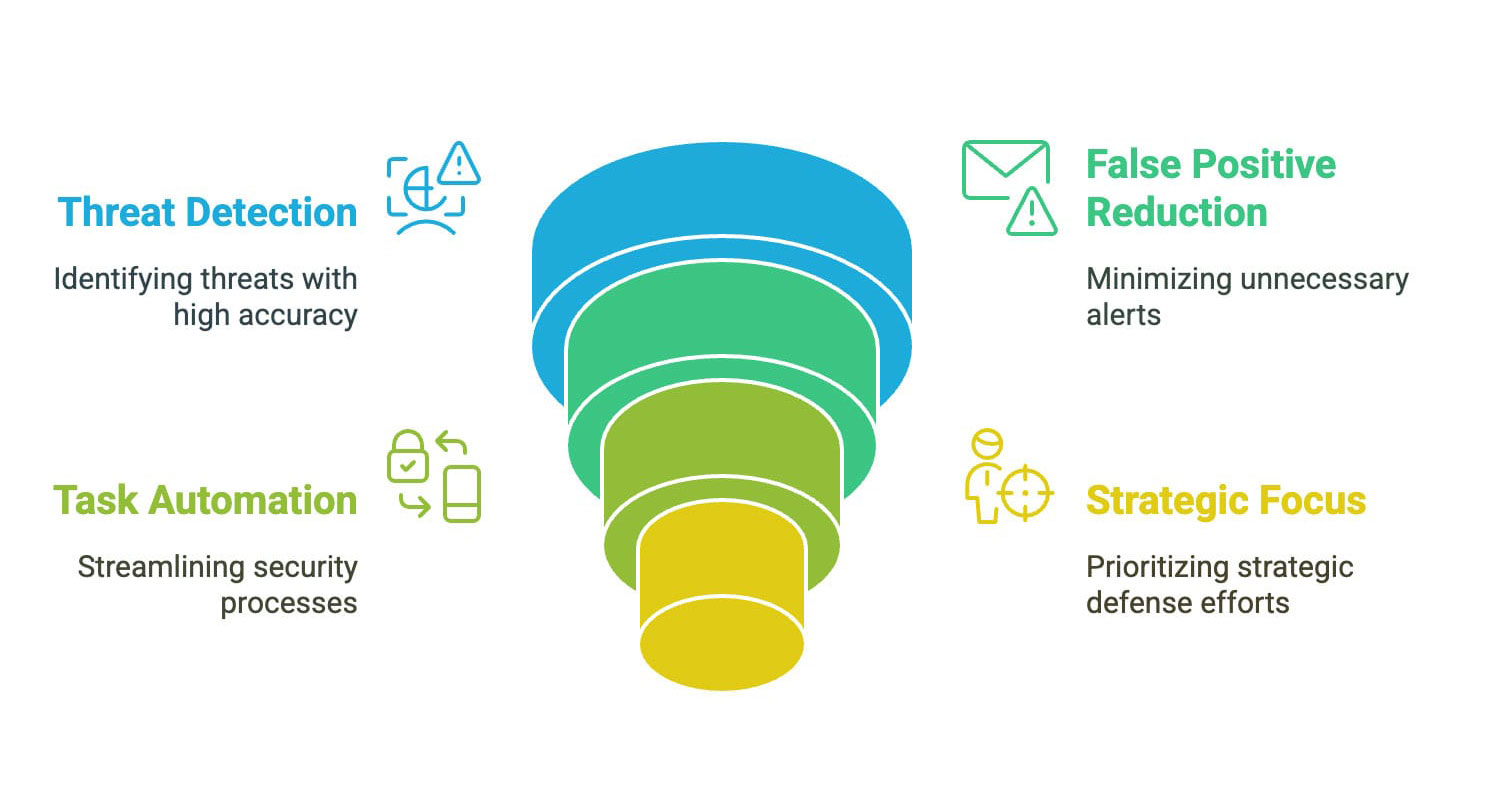
Together Trellix NDR with Trellix Wise provides greater threat detection accuracy, reduces false positives, automates complex tasks, and empowers your security team to focus on what matters most: strategic defense. It seamlessly integrates with your existing Trellix Network Security ecosystem, maximizing your current investment and fortifying your network defenses. Traditional Network Detection and Response (NDR) solutions struggle to keep pace with sophisticated threats in today's rapidly evolving cybersecurity landscape. Trellix NDR with Trellix Wise introduces a new groundbreaking approach to NDR, which leverages on-device large language models (LLMs) and an interconnected network of AI agents to detect and disrupt attacker activity across the cyber kill chain and accelerate investigation and response for security operations teams. This blog post uncovers the inner workings of our groundbreaking NDR solution with Trellix Wise, where advanced AI processes and analyzes network data at scale to generate comprehensive and actionable threat detections, investigations, and reports with unprecedented speed and accuracy.
Distributed AI architecture that scales
Trellix NDR with Trellix Wise’s unique approach is designed to provide intelligent, actionable outcomes. You can expect comprehensive network visibility, ensuring every potential threat is identified. Our AI-driven system accelerates threat detection, minimizing the window of vulnerability. You'll receive precise, prioritized recommendations tailored to your environment, enabling effective remediation. Finally, comprehensive, easy-to-understand reports translate complex data into clear insights, empowering your team to make informed decisions.
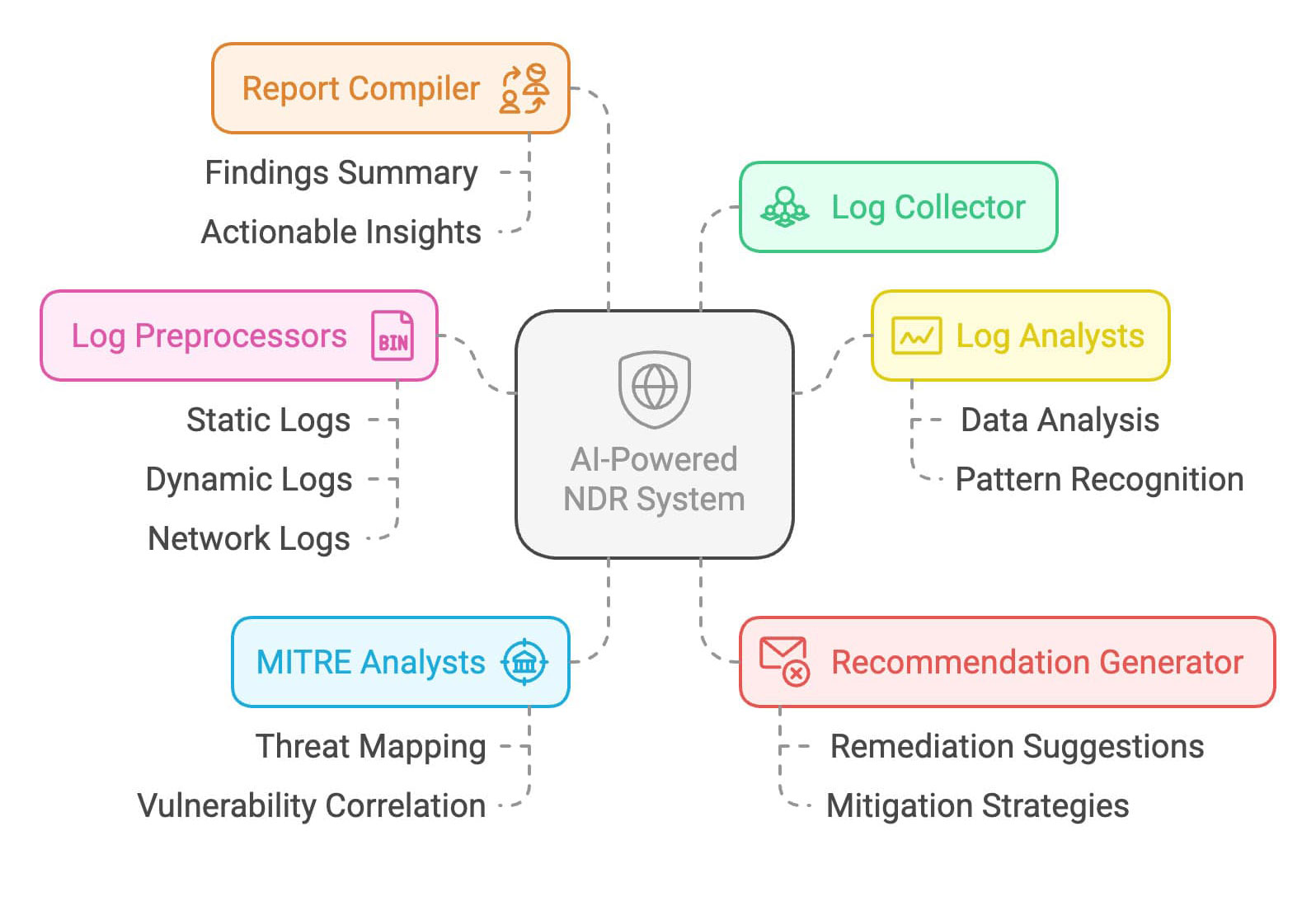
Key components of Trellix NDR with Trellix Wise:
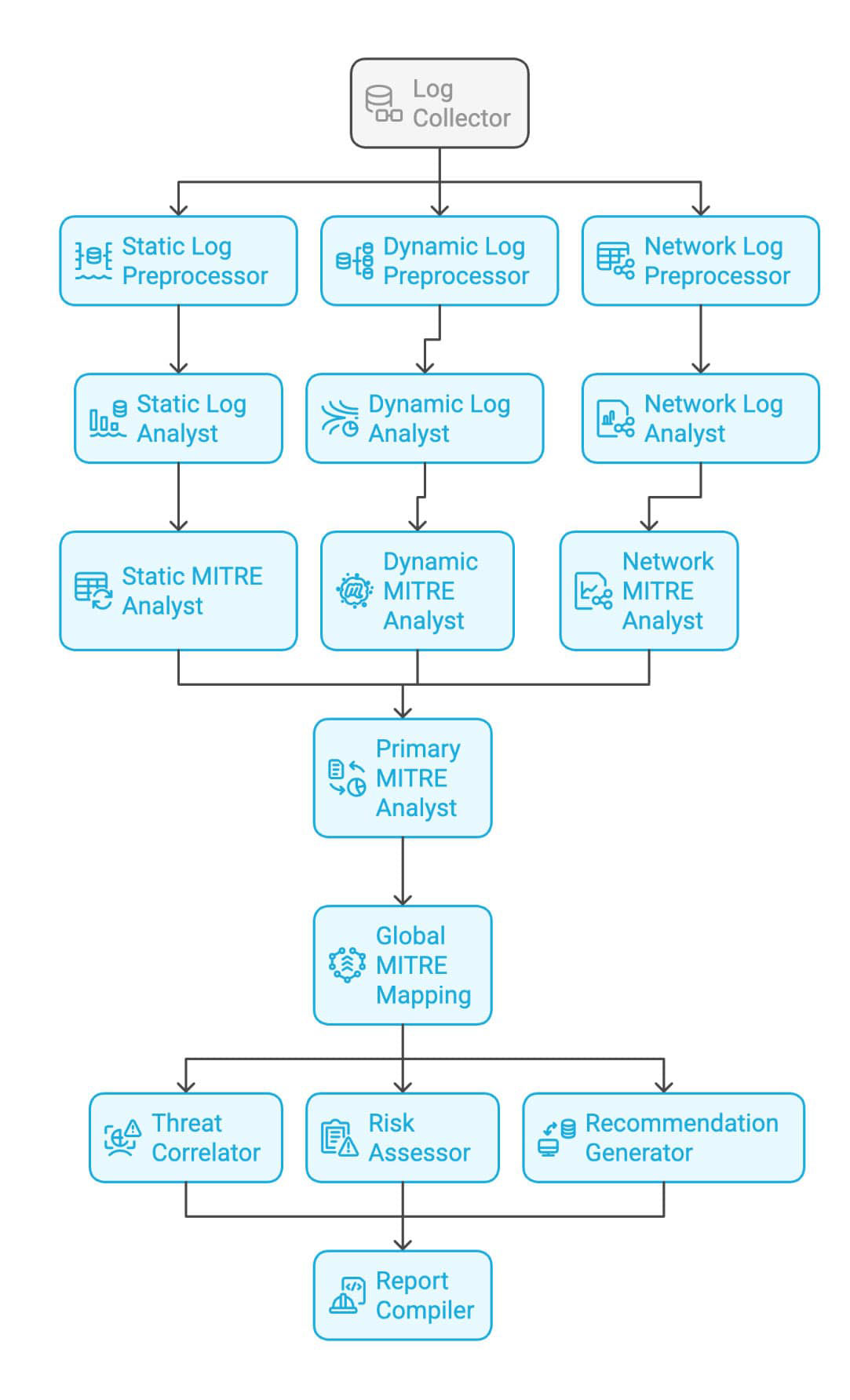
- Log Collector: The central hub that gathers data from various sources (It aggregates and stores the collected data in a centralized repository, making it easily accessible for analysis and reporting)
- Log Preprocessors: With specialized Log Preprocessors for each log type (static, dynamic, network), we ensure data accuracy and streamline processing, leading to faster and more reliable threat detection.
- Log Analysts: AI-driven Log Analysts delve deep into preprocessed data, enabling proactive threat detection and providing critical insights to prevent security breaches.
- MITRE Analysts: MITRE Analysts link threats to the ATT&CK framework, facilitating faster incident response by providing a clear understanding of attack techniques.
- Master MITRE Analyst: Consolidates and correlates MITRE mappings from multiple sources, providing a comprehensive view of threats and vulnerabilities.
- Recommendation Generator, Threat Correlator, and Risk Assessor: Advanced analysis modules generate actionable recommendations for remediation and mitigation, correlate threats and vulnerabilities to identify potential attack paths, assess risk levels, and provide prioritized recommendations and remediation
- Report Compiler: The Report Compiler synthesizes all findings into a concise and clear report, providing security teams with the actionable insights they need for rapid response and effective mitigation.
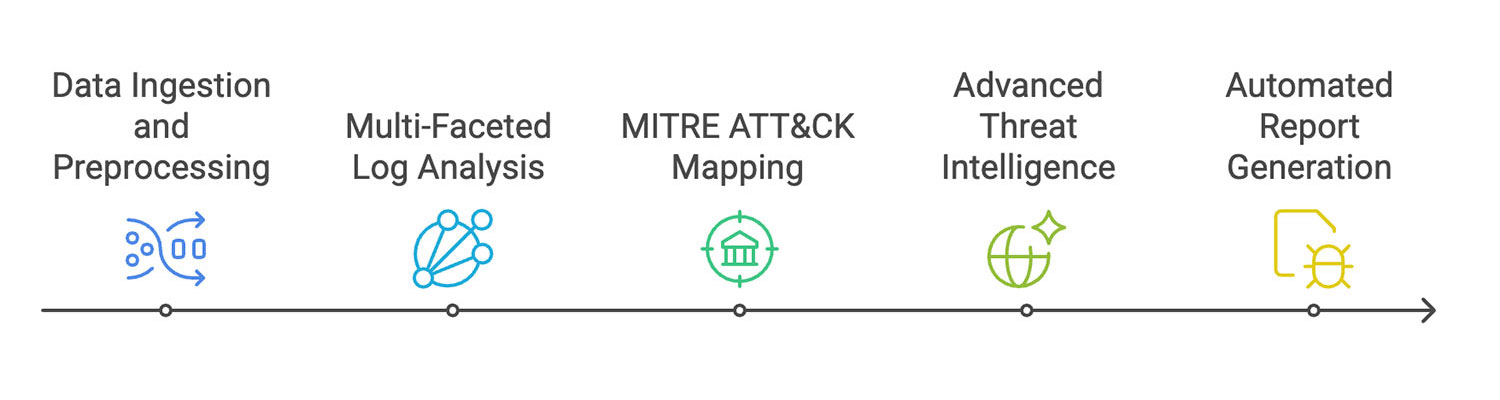
Trellix NDR with Trellix Wise employs a sophisticated, multi-layered approach to network security through an interconnected system of specialized AI agents and on-device large language models. At its core, the solution leverages these intelligent components to deliver comprehensive threat detection, analysis, and response capabilities while maintaining data privacy and reducing latency. Let's explore the five key stages of this innovative security framework that work in concert to protect your network infrastructure and provide actionable intelligence for your security teams.
How It Works:
- Data ingestion and preprocessing: Our system begins with the Log Collector, an intelligent agent that aggregates data from multiple sources. This raw information is then routed to specialized Log Preprocessor agents, each optimized for specific log types (static, dynamic, and network). These agents clean, normalize, and structure the data for efficient analysis.
Our system's foundation is built on the Log Collector, a sophisticated agent that seamlessly aggregates data from diverse sources. This raw data is routed to our Log Preprocessor agents, each finely tuned to handle specific log types, including static, dynamic, and network logs. These agents employ advanced techniques to meticulously clean, normalize, and structure the data, ensuring it is optimized for efficient analysis and actionable insights - Multi-faceted log analysis: The preprocessed logs are sent to our Log Analyst agents. These AI-driven modules utilize on-device LLMs to conduct thorough and contextual analyses of the log data. We ensure quick results by processing the information locally while safeguarding data privacy and reducing latency risk.
- MITRE ATT&CK mapping: One of the most innovative aspects of our system is the integration of MITRE ATT&CK framework mapping. Dedicated MITRE Analyst agents (static, dynamic, and network) correlate, in real-time and retrospectively, observed behaviors with established tactics and techniques. The Master MITRE Analyst then synthesizes these findings to create a comprehensive threat picture.
- Advanced threat intelligence: The system's "brain" consists of three key components:
- Recommendation generator: Suggests actionable mitigation strategies(Generate actionable recommendations for remediation and mitigation)
- Threat correlator: Identifies relationships between seemingly disparate events(Correlate threats and vulnerabilities to identify potential attack paths)
- Risk assessor: Quantifies the potential impact of discovered threats (Assess risk levels and provide prioritized recommendations for remediation)
- Automated report generation: Finally, the Report Compiler agent collates all the analyzed data, insights, and recommendations into a clear, actionable threat report. This automated process ensures consistent, high-quality reporting without human bias or error.
- Summary of threats and vulnerabilities
- Recommendations for remediation and mitigation
- Risk assessment and prioritization
- Detailed analysis and findings
The Report Compiler provides a clear and concise analysis summary, making it easy for security teams to understand and act on the findings.
AI intelligence you can trust
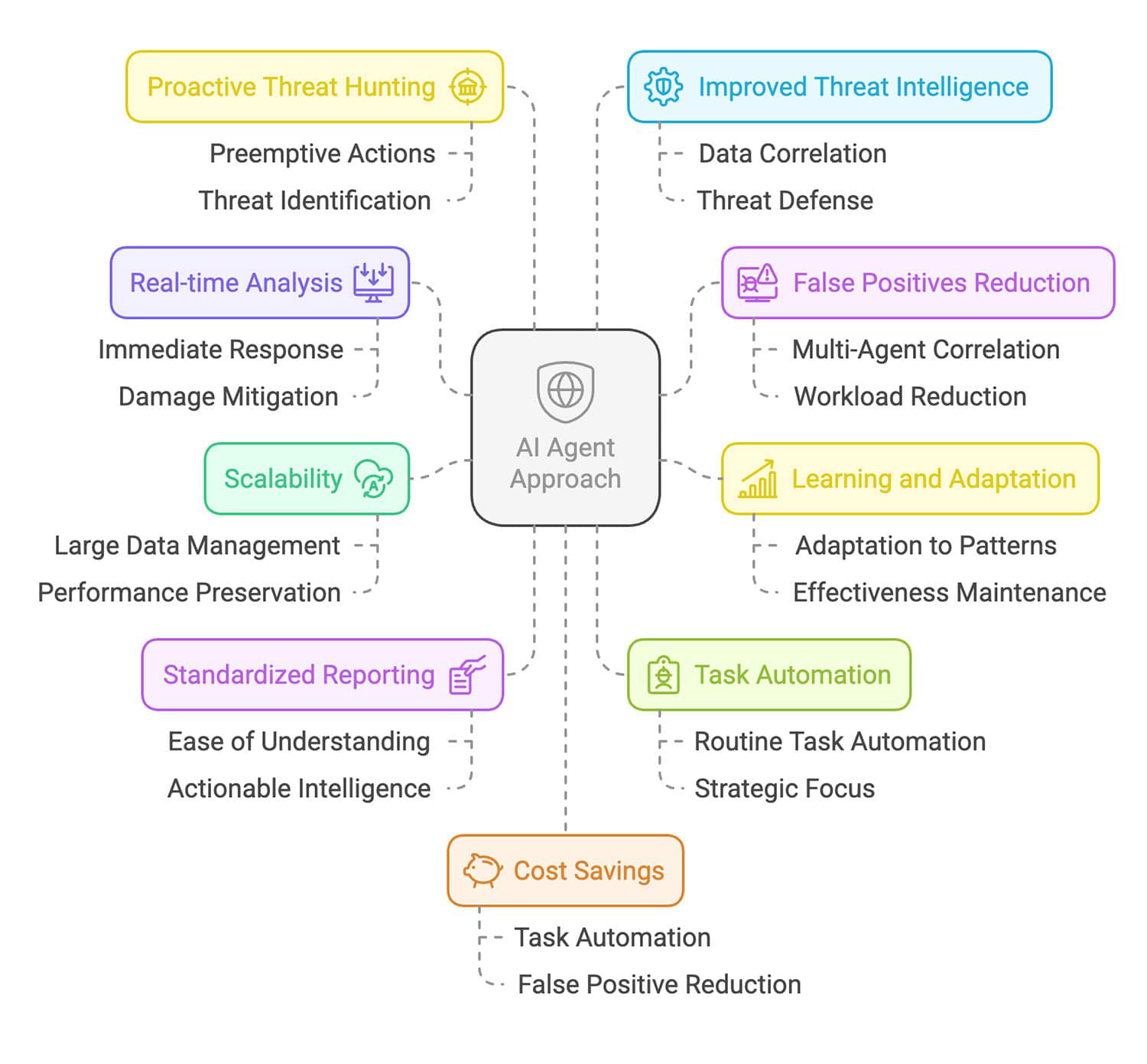
The implementation of AI agents in Trellix NDR with Trellix Wise represents a transformative leap in network security capabilities, delivering measurable advantages across multiple dimensions of threat detection and response. By leveraging our innovative multi-agent architecture and on-device LLMs, organizations can achieve enhanced security outcomes while significantly reducing operational overhead. Here are the key benefits that make our AI agent approach a game-changer in modern cybersecurity:
- Real-time analysis and response capabilities: Our AI agents can analyze and respond to threats as they occur, minimizing potential damage and reducing the time it takes to mitigate security incidents.
- Decreased false positives through multi-agent correlation: By correlating data from multiple AI agents, our system can identify and eliminate false positives, improving the accuracy of threat detection and reducing the workload on security teams.
- Ongoing learning and adaptation to emerging threat patterns: Our AI agents are constantly learning and adapting to new threat patterns, ensuring that our system remains effective against the latest threats.
- Scalability to manage large data volumes: Our AI agent approach is designed to scale, allowing us to manage and analyze large volumes of data without sacrificing performance.
- Consistent and standardized threat reporting: Our system provides consistent and standardized threat reporting, making it easier for security teams to understand and act on threat intelligence.
- Automation of routine tasks: AI agents can automate repetitive and time-consuming tasks, freeing up security analysts to focus on more complex and strategic issues.
- Proactive threat hunting: AI agents can proactively search for threats within an organization's environment, identifying and mitigating potential threats before they can cause damage.
- Improved threat intelligence: By analyzing and correlating data from multiple sources, AI agents can generate more comprehensive and accurate threat intelligence, helping organizations to better understand and defend against potential threats.
- Enhanced incident response: AI agents can assist with incident response by automating tasks, providing relevant information, and coordinating response efforts.
- Cost savings: By automating tasks, reducing false positives, and improving threat detection and response, our AI agent approach can help organizations to save money on security costs.
A better way to AI
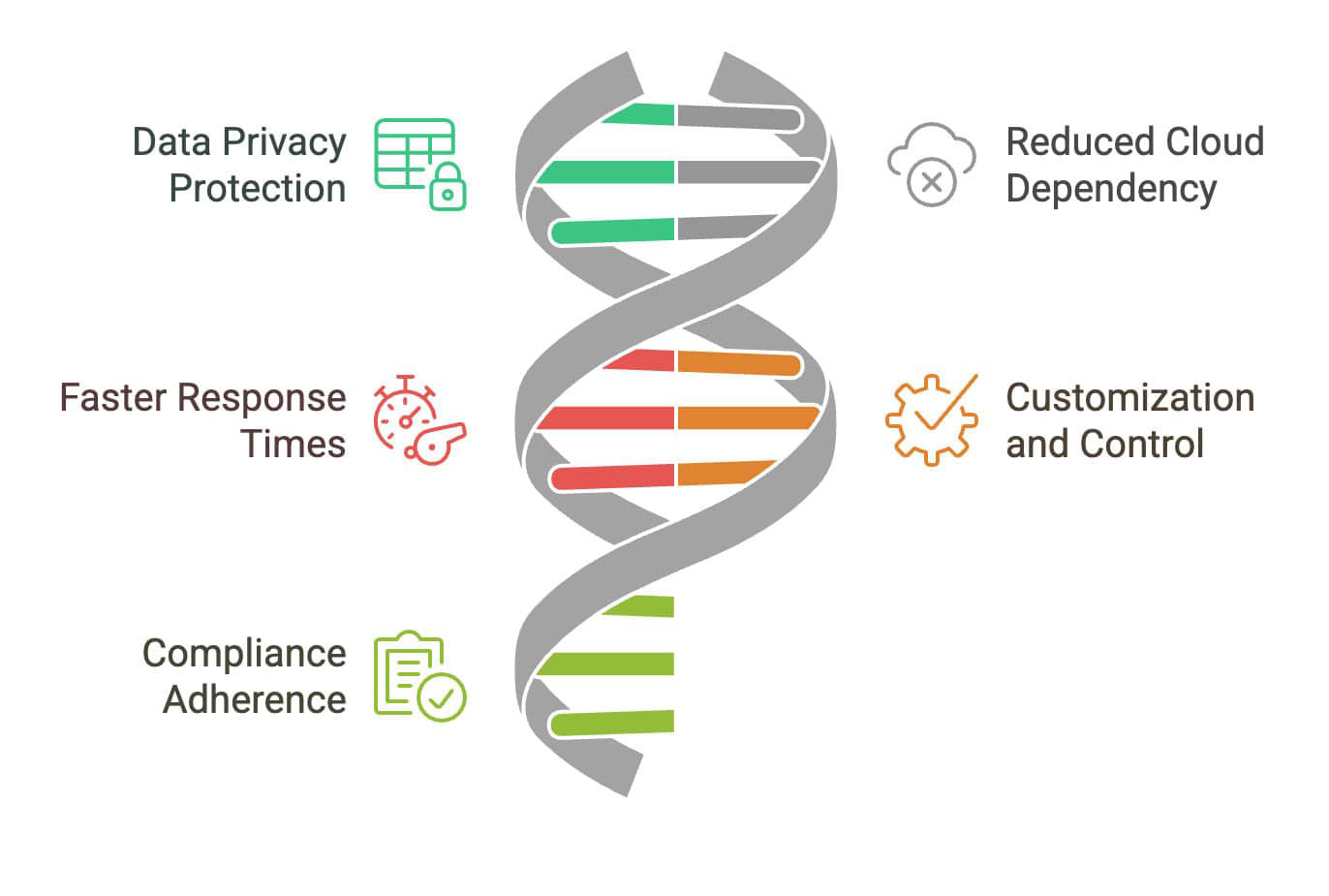
Our decision to implement on-device large language models (LLMs) for our NDR system is a game-changer in terms of security. This approach significantly enhances the security posture of our solution:
- Data privacy protection: By processing sensitive network data locally on the device, we remove the need to send potentially confidential information to external servers. This approach significantly reduces the attack surface and lowers the risk of data interception or unauthorized access during transmission.
- Reduced cloud dependency: On-device LLMs function independently of internet connectivity, ensuring ongoing protection even in situations where cloud access is compromised or unavailable. This resilience is vital for maintaining security operations in air-gapped networks or during network outages.
- Faster response times: Local processing removes latency associated with cloud-based solutions, facilitating near-instantaneous threat detection and response. In the fast-paced world of cybersecurity, every second counts, and on-device LLMs offer a crucial advantage in response speed.
- Customization and control: Organizations gain greater control over the LLM models installed on their devices. This allows for fine-tuning and customization to meet specific security needs or address industry-specific threats without depending on external vendors for model updates.
- Compliance adherence: For industries with stringent data regulations (e.g., healthcare, finance), on-device LLMs ensure that sensitive data remains within the organization's control, simplifying compliance with standards like GDPR, HIPAA, or PCI-DSS.
- Tamper-resistant analysis: Integrating LLMs directly into security devices makes it more difficult for attackers to manipulate or circumvent the AI-driven analysis. This adds an extra layer of security to the threat detection process itself.
- Offline capabilities: In the case of a network-based attack that disrupts internet connectivity, on-device LLMs can continue to operate, providing essential threat analysis and response capabilities when they're needed most.
- Reduced attack surface: By eliminating the need for constant communication with cloud servers, we significantly decrease the potential entry points for attackers, making the overall system more secure and resilient against network-based threats.
Conclusion:
By leveraging the power of on-device LLMs and a network of specialized AI agents, our NDR solution marks a significant advancement in threat detection and response capabilities. This innovative approach enables organizations to stay ahead of evolving cyber threats, offering unmatched visibility and actionable intelligence to protect their digital assets.
The implementation of on-device LLMs signifies a fundamental change in our approach to AI-driven cybersecurity. This technology not only boosts the effectiveness of our NDR solution but also alleviates many security concerns linked to traditional cloud-based AI systems.
As we continue to refine and expand our Trellix NDR solution with Trellix Wise GenAI capabilities, we remain dedicated to pushing the limits of what's achievable in cybersecurity. Stay tuned for future updates as we work diligently to keep your networks secure in an increasingly complex threat landscape.
Try for yourself
Trellix continues to invest in network detection and response that utilize AI and ML. Learn more about Trellix network security solutions or request a demo to try for yourself today.
RECENT NEWS
-
Apr 7, 2025
Trellix Strengthens Focus on Customer Engagement and Regulated Industries with Executive Appointments
-
Feb 5, 2025
Trellix Accelerates Secure Cloud Adoption in Australia with New Government Accreditations
-
Jan 28, 2025
Trellix and NEXTGEN Accelerate Cybersecurity Platform Adoption in Australia and New Zealand
-
Jan 22, 2025
Trellix Welcomes New CEO to Lead Next Phase of Growth
-
Jan 14, 2025
Trellix Accelerates Global Partner Growth with Revamped Xtend Partner Program
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
