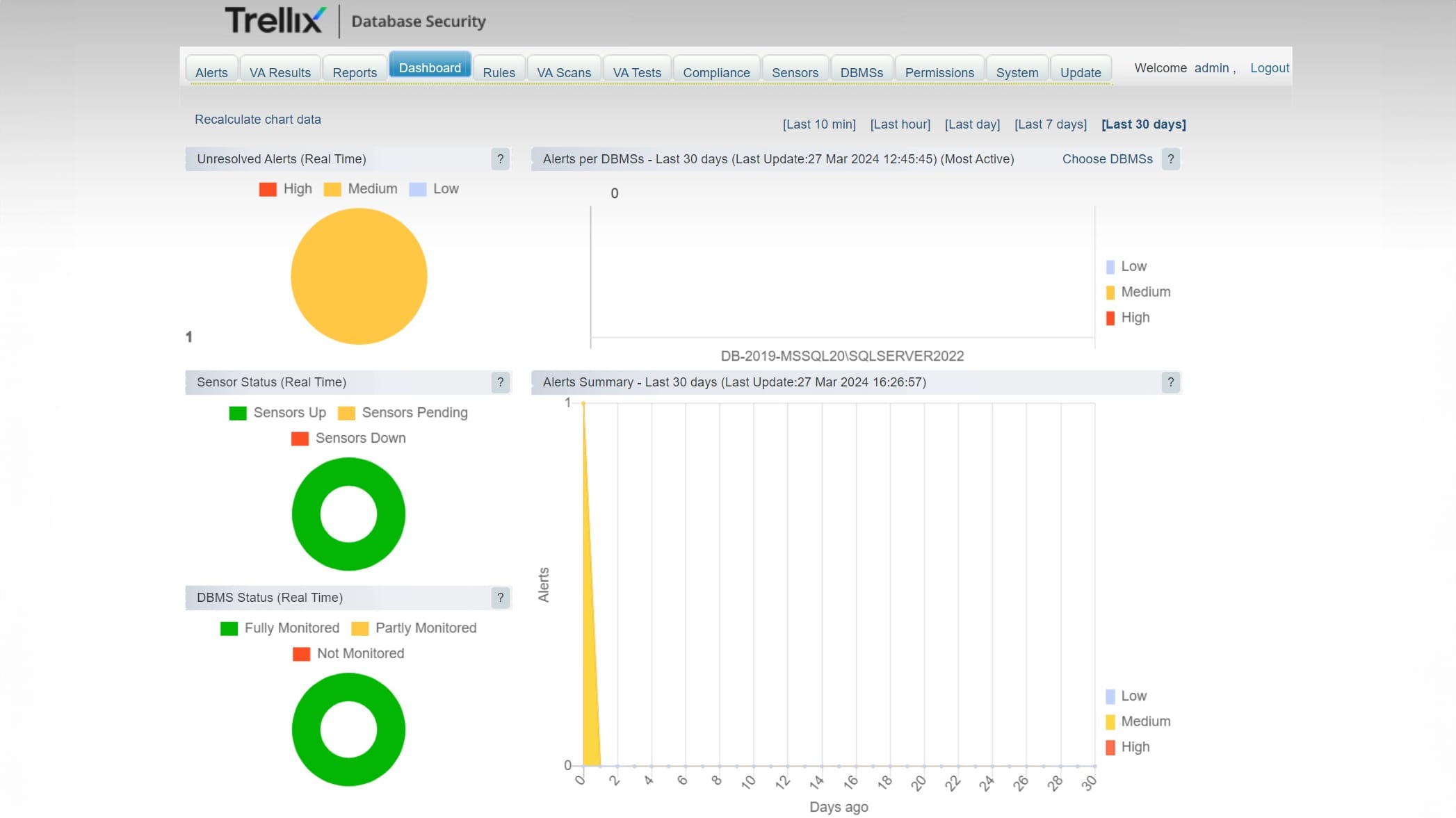
Trellix Database Security
Find and defend databases and the information they contain
Did you know ...
Trellix Data Security statistics
000+
Patch protections delivered by Trellix Database Security
000+
File formats supported by Trellix Data Loss Prevention
00M+
Drives protected worldwide by Trellix Data Encryption
Why Trellix Database Security?
Find and Classify
Discover sensitive and proprietary information in databases across the environment.
Support Compliance
Improve regulatory compliance by blocking unauthorized access to sensitive data.
Enhance Security
Address vulnerabilities quickly, with little to no downtime.
Product features
Frequently asked questions
Related resources

Learn to protect information from leaks and breaches while optimizing performance and managing access.

Protect your databases from vulnerabilities without downtime using Trellix Database Security Virtual Patching (vPatch)

Read how it provides advanced protection across database types while supporting compliance initiatives.

What problems does Data Security solve, and what capabilities should your solution include? Take a look at the future of Data Security.